From 2a0f18cfd8fe14876b8351ae87a1cc5fcaad160e Mon Sep 17 00:00:00 2001
From: PaulaTomasG <94612518+PaulaTomasG@users.noreply.github.com>
Date: Fri, 30 Sep 2022 16:19:07 +0200
Subject: [PATCH 01/10] Update event-4768.md
Event ID 4768 with kerb return code 0x17 does exist and gets logged. It's 0x10 and 0x18 the only ones that rely on even 4771 instead.
See line 32 in this same article.
---
windows/security/threat-protection/auditing/event-4768.md | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/windows/security/threat-protection/auditing/event-4768.md b/windows/security/threat-protection/auditing/event-4768.md
index 6846561482..14a09b7044 100644
--- a/windows/security/threat-protection/auditing/event-4768.md
+++ b/windows/security/threat-protection/auditing/event-4768.md
@@ -219,7 +219,7 @@ The most common values:
| 0x14 | KDC\_ERR\_TGT\_REVOKED | TGT has been revoked | Since the remote KDC may change its PKCROSS key while there are PKCROSS tickets still active, it SHOULD cache the old PKCROSS keys until the last issued PKCROSS ticket expires. Otherwise, the remote KDC will respond to a client with a KRB-ERROR message of type KDC\_ERR\_TGT\_REVOKED. See [RFC1510](https://www.ietf.org/proceedings/49/I-D/draft-ietf-cat-kerberos-pk-cross-07.txt) for more details. |
| 0x15 | KDC\_ERR\_CLIENT\_NOTYET | Client not yet valid—try again later | No information. |
| 0x16 | KDC\_ERR\_SERVICE\_NOTYET | Server not yet valid—try again later | No information. |
-| 0x17 | KDC\_ERR\_KEY\_EXPIRED | Password has expired—change password to reset | The user’s password has expired.
This error code cannot occur in event “[4768](event-4768.md). A Kerberos authentication ticket (TGT) was requested”. It occurs in “[4771](event-4771.md). Kerberos pre-authentication failed” event. |
+| 0x17 | KDC\_ERR\_KEY\_EXPIRED | Password has expired—change password to reset | The user’s password has expired. |
| 0x18 | KDC\_ERR\_PREAUTH\_FAILED | Pre-authentication information was invalid | The wrong password was provided.
This error code cannot occur in event “[4768](event-4768.md). A Kerberos authentication ticket (TGT) was requested”. It occurs in “[4771](event-4771.md). Kerberos pre-authentication failed” event. |
| 0x19 | KDC\_ERR\_PREAUTH\_REQUIRED | Additional pre-authentication required | This error often occurs in UNIX interoperability scenarios. MIT-Kerberos clients do not request pre-authentication when they send a KRB\_AS\_REQ message. If pre-authentication is required (the default), Windows systems will send this error. Most MIT-Kerberos clients will respond to this error by giving the pre-authentication, in which case the error can be ignored, but some clients might not respond in this way. |
| 0x1A | KDC\_ERR\_SERVER\_NOMATCH | KDC does not know about the requested server | No information. |
From c353652b97e343590665d0af65b811437858d39e Mon Sep 17 00:00:00 2001
From: Sriraman M S <45987684+msbemba@users.noreply.github.com>
Date: Tue, 15 Nov 2022 19:53:26 +0530
Subject: [PATCH 02/10] Update install-md-app-guard.md
Made changes to the navigation in the steps to install by using Intune
fixes #https://github.com/MicrosoftDocs/windows-itpro-docs/issues/10770
---
.../install-md-app-guard.md | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
index b4fb01a3c6..ea6fccbf62 100644
--- a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
+++ b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
@@ -100,7 +100,7 @@ Application Guard functionality is turned off by default. However, you can quick
1. In the **Platform** list, select **Windows 10 and later**.
- 1. In the **Profile** list, select **Endpoint protection**.
+ 1. In the **Profile** Type, Choose **Templates** and select **Endpoint protection** .
1. Choose **Create**.
From 13fdf16793f4547c1b74e968631d54f5b8ee952d Mon Sep 17 00:00:00 2001
From: Sriraman M S <45987684+msbemba@users.noreply.github.com>
Date: Wed, 16 Nov 2022 10:13:49 +0530
Subject: [PATCH 03/10] Update
windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
Co-authored-by: JohanFreelancer9 <48568725+JohanFreelancer9@users.noreply.github.com>
---
.../install-md-app-guard.md | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
index ea6fccbf62..0eb70f9270 100644
--- a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
+++ b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
@@ -100,7 +100,7 @@ Application Guard functionality is turned off by default. However, you can quick
1. In the **Platform** list, select **Windows 10 and later**.
- 1. In the **Profile** Type, Choose **Templates** and select **Endpoint protection** .
+ 1. In the **Profile** type, choose **Templates** and select **Endpoint protection**.
1. Choose **Create**.
From 059c0d6e2c46512dd49e7973297c5db8515f8f3c Mon Sep 17 00:00:00 2001
From: Denise Vangel-MSFT
Date: Wed, 30 Nov 2022 12:47:40 -0800
Subject: [PATCH 04/10] Update install-md-app-guard.md
---
.../install-md-app-guard.md | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
index 0eb70f9270..dba507f3c0 100644
--- a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
+++ b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
@@ -8,7 +8,7 @@ ms.pagetype: security
ms.localizationpriority: medium
author: vinaypamnani-msft
ms.author: vinpa
-ms.date: 09/09/2021
+ms.date: 11/30/2022
ms.reviewer:
manager: aaroncz
ms.custom: asr
From d23d717dcbfc8d789a8d20451afed341b2155046 Mon Sep 17 00:00:00 2001
From: Denise Vangel-MSFT
Date: Wed, 30 Nov 2022 12:50:46 -0800
Subject: [PATCH 05/10] Update install-md-app-guard.md
---
.../install-md-app-guard.md | 39 ++++++++++---------
1 file changed, 20 insertions(+), 19 deletions(-)
diff --git a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
index dba507f3c0..97f4e14332 100644
--- a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
+++ b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
@@ -27,10 +27,12 @@ ms.collection:
## Review system requirements
See [System requirements for Microsoft Defender Application Guard](./reqs-md-app-guard.md) to review the hardware and software installation requirements for Microsoft Defender Application Guard.
->[!NOTE]
->Microsoft Defender Application Guard is not supported on VMs and VDI environment. For testing and automation on non-production machines, you may enable WDAG on a VM by enabling Hyper-V nested virtualization on the host.
+
+> [!NOTE]
+> Microsoft Defender Application Guard is not supported on VMs and VDI environment. For testing and automation on non-production machines, you may enable WDAG on a VM by enabling Hyper-V nested virtualization on the host.
## Prepare for Microsoft Defender Application Guard
+
Before you can install and use Microsoft Defender Application Guard, you must determine which way you intend to use it in your enterprise. You can use Application Guard in either **Standalone** or **Enterprise-managed** mode.
### Standalone mode
@@ -51,6 +53,7 @@ Applies to:
You and your security department can define your corporate boundaries by explicitly adding trusted domains and by customizing the Application Guard experience to meet and enforce your needs on employee devices. Enterprise-managed mode also automatically redirects any browser requests to add non-enterprise domain(s) in the container.
The following diagram shows the flow between the host PC and the isolated container.
+

## Install Application Guard
@@ -59,22 +62,22 @@ Application Guard functionality is turned off by default. However, you can quick
### To install by using the Control Panel
-1. Open the **Control Panel**, click **Programs,** and then click **Turn Windows features on or off**.
+1. Open the **Control Panel**, click **Programs,** and then select **Turn Windows features on or off**.

-2. Select the check box next to **Microsoft Defender Application Guard** and then click **OK**.
+2. Select the check box next to **Microsoft Defender Application Guard** and then select **OK**.
Application Guard and its underlying dependencies are all installed.
### To install by using PowerShell
->[!NOTE]
->Ensure your devices have met all system requirements prior to this step. PowerShell will install the feature without checking system requirements. If your devices don't meet the system requirements, Application Guard may not work. This step is recommended for enterprise managed scenarios only.
+> [!NOTE]
+> Ensure your devices have met all system requirements prior to this step. PowerShell will install the feature without checking system requirements. If your devices don't meet the system requirements, Application Guard may not work. This step is recommended for enterprise managed scenarios only.
-1. Click the **Search** or **Cortana** icon in the Windows 10 or Windows 11 taskbar and type **PowerShell**.
+1. Select the **Search** or **Cortana** icon in the Windows 10 or Windows 11 taskbar and type **PowerShell**.
-2. Right-click **Windows PowerShell**, and then click **Run as administrator**.
+2. Right-click **Windows PowerShell**, and then select **Run as administrator**.
Windows PowerShell opens with administrator credentials.
@@ -94,17 +97,15 @@ Application Guard functionality is turned off by default. However, you can quick
:::image type="content" source="images/MDAG-EndpointMgr-newprofile.jpg" alt-text="Enroll devices in Intune.":::
-1. Sign in to the [Microsoft Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
-
-1. Choose **Devices** > **Configuration profiles** > **+ Create profile**, and do the following:
+1. In the [Microsoft Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431), choose **Devices** > **Configuration profiles** > **+ Create profile**, and do the following:
1. In the **Platform** list, select **Windows 10 and later**.
- 1. In the **Profile** type, choose **Templates** and select **Endpoint protection**.
+ 2. In the **Profile** type, choose **Templates** and select **Endpoint protection**.
- 1. Choose **Create**.
+ 3. Choose **Create**.
-1. Specify the following settings for the profile:
+2. Specify the following settings for the profile:
- **Name** and **Description**
@@ -114,16 +115,16 @@ Application Guard functionality is turned off by default. However, you can quick
- Choose your preferences for **Clipboard behavior**, **External content**, and the remaining settings.
-1. Choose **OK**, and then choose **OK** again.
+3. Choose **OK**, and then choose **OK** again.
-1. Review your settings, and then choose **Create**.
+4. Review your settings, and then choose **Create**.
-1. Choose **Assignments**, and then do the following:
+5. Choose **Assignments**, and then do the following:
1. On the **Include** tab, in the **Assign to** list, choose an option.
- 1. If you have any devices or users you want to exclude from this endpoint protection profile, specify those on the **Exclude** tab.
+ 2. If you have any devices or users you want to exclude from this endpoint protection profile, specify those on the **Exclude** tab.
- 1. Click **Save**.
+ 3. Select **Save**.
After the profile is created, any devices to which the policy should apply will have Microsoft Defender Application Guard enabled. Users might have to restart their devices in order for protection to be in place.
From 81a81b940cb2d09e1b155f17cfb2179477f9f1ec Mon Sep 17 00:00:00 2001
From: =?UTF-8?q?C=C4=83t=C4=83lin=20Emil=20Fetoiu?=
Date: Mon, 12 Dec 2022 11:05:58 -0800
Subject: [PATCH 06/10] Doc updates to Firewall CSP
Add documentation for firewall logging settings, for each of DomainProfile, PrivateProfile, PublicProfile. The settings are:
- EnableLogDroppedPackets
- EnableLogSuccessConnections
- EnableLogIgnoredRules
- LogMaxFileSize
- LogFilePath
Update documentation for FirewallRules/FirewallRuleName/IcmpTypesAndCodes to mention a comma separated list of values can be specified
Update documentation for FirewallRules/FirewallRuleName/InterfaceTypes to add MBB (Mobile Broadband) to allowed values
---
windows/client-management/mdm/firewall-csp.md | 37 ++++++++++++++++++-
1 file changed, 36 insertions(+), 1 deletion(-)
diff --git a/windows/client-management/mdm/firewall-csp.md b/windows/client-management/mdm/firewall-csp.md
index 3d2f9042c4..a425989761 100644
--- a/windows/client-management/mdm/firewall-csp.md
+++ b/windows/client-management/mdm/firewall-csp.md
@@ -52,6 +52,11 @@ Firewall
------------DisableStealthMode
------------Shielded
------------DisableUnicastResponsesToMulticastBroadcast
+------------EnableLogDroppedPackets
+------------EnableLogSuccessConnections
+------------EnableLogIgnoredRules
+------------LogMaxFileSize
+------------LogFilePath
------------DisableInboundNotifications
------------AuthAppsAllowUserPrefMerge
------------GlobalPortsAllowUserPrefMerge
@@ -65,6 +70,11 @@ Firewall
------------DisableStealthMode
------------Shielded
------------DisableUnicastResponsesToMulticastBroadcast
+------------EnableLogDroppedPackets
+------------EnableLogSuccessConnections
+------------EnableLogIgnoredRules
+------------LogMaxFileSize
+------------LogFilePath
------------DisableInboundNotifications
------------AuthAppsAllowUserPrefMerge
------------GlobalPortsAllowUserPrefMerge
@@ -78,6 +88,11 @@ Firewall
------------DisableStealthMode
------------Shielded
------------DisableUnicastResponsesToMulticastBroadcast
+------------EnableLogDroppedPackets
+------------EnableLogSuccessConnections
+------------EnableLogIgnoredRules
+------------LogMaxFileSize
+------------LogFilePath
------------DisableInboundNotifications
------------AuthAppsAllowUserPrefMerge
------------GlobalPortsAllowUserPrefMerge
@@ -223,6 +238,25 @@ Boolean value. If it's true, unicast responses to multicast broadcast traffic ar
Default value is false.
Value type is bool. Supported operations are Add, Get and Replace.
+**/EnableLogDroppedPackets**
+Boolean value. If this value is true, firewall will log all dropped packets. The merge law for this option is to let "on" values win.
+Default value is false. Supported operations are Get and Replace.
+
+**/EnableLogSuccessConnections**
+Boolean value. If this value is true, firewall will log all successful inbound connections. The merge law for this option is to let "on" values win.
+Default value is false. Supported operations are Get and Replace.
+
+**/EnableLogIgnoredRules**
+Boolean value. If this value is true, firewall will log ignored firewall rules. The merge law for this option is to let "on" values win.
+Default value is false. Supported operations are Get and Replace.
+
+**/LogMaxFileSize**
+Integer value that specifies the size, in kilobytes, of the log file where dropped packets, successful connections and ignored rules are logged. The merge law for this option is to let the value of the GroupPolicyRSoPStore win if it is configured, otherwise the MdmStore value wins if it is configured, otherwise the local store value is used.
+Default value is 1024. Supported operations are Get and Replace
+
+**/LogFilePath**
+String value that represents the file path to the log where firewall logs dropped packets, successful connections and ignored rules. The merge law for this option is to let the value of the GroupPolicyRSoPStore win if it is configured, otherwise the MdmStore value wins if it is configured, otherwise the local store value is used. Default value is "%systemroot%\system32\LogFiles\Firewall\pfirewall.log". Supported operations are Get and Replace
+
**/DisableInboundNotifications**
Boolean value. If this value is false, the firewall MAY display a notification to the user when an application is blocked from listening on a port. If this value is on, the firewall MUST NOT display such a notification. The merge law for this option is to let the value of the GroupPolicyRSoPStore win if it's configured; otherwise, the local store value is used.
Default value is false.
@@ -349,7 +383,7 @@ Value type is string. Supported operations are Add, Get, Replace, and Delete.
**FirewallRules/_FirewallRuleName_/IcmpTypesAndCodes**
-ICMP types and codes applicable to the firewall rule. To specify all ICMP types and codes, use the “\*” character. For specific ICMP types and codes, use the “:” character to separate the type and code, for example, 3:4, 1:\*. The “\*” character can be used to represent any code. The “\*” character cannot be used to specify any type; examples such as “\*:4” or “\*:\*” are invalid.
+Comma separated list of ICMP types and codes applicable to the firewall rule. To specify all ICMP types and codes, use the “\*” character. For specific ICMP types and codes, use the “:” character to separate the type and code, for example, 3:4, 1:\*. The “\*” character can be used to represent any code. The “\*” character cannot be used to specify any type; examples such as “\*:4” or “\*:\*” are invalid.
If not specified, the default is All.
Value type is string. Supported operations are Add, Get, Replace, and Delete.
@@ -431,6 +465,7 @@ Comma separated list of interface types. Valid values:
- RemoteAccess
- Wireless
- Lan
+- MBB (i.e. Mobile Broadband)
If not specified, the default is All.
Value type is string. Supported operations are Get and Replace.
From e00f530b42fb52421ab01a623865586629889dbc Mon Sep 17 00:00:00 2001
From: Jeff Borsecnik <36546697+jborsecnik@users.noreply.github.com>
Date: Wed, 14 Dec 2022 10:42:01 -0800
Subject: [PATCH 07/10] standardize readme file per DevOps TASK 7260369
---
README.md | 66 ++++++++++++++++++++++++++++++++++++++++++++++++++++++-
1 file changed, 65 insertions(+), 1 deletion(-)
diff --git a/README.md b/README.md
index 824a7c6d56..0bc19b009f 100644
--- a/README.md
+++ b/README.md
@@ -1,3 +1,67 @@
+# Overview
+
+## Learn how to contribute
+
+Anyone who is interested can contribute to the topics. When you contribute, your work will go directly into the content set after being merged. It will then be published to [Microsoft Learn](https://learn.microsoft.com/) and you will be listed as a contributor at: .
+
+### Quickly update an article using GitHub.com
+
+Contributors who only make infrequent or small updates can edit the file directly on GitHub.com without having to install any additional software. This article shows you how. [This two-minute video](https://www.microsoft.com/videoplayer/embed/RE1XQTG) also covers how to contribute.
+
+1. Make sure you're signed in to GitHub.com with your GitHub account.
+2. Browse to the page you want to edit on Microsoft Learn.
+3. On the right-hand side of the page, click **Edit** (pencil icon).
+
+ 
+
+4. The corresponding topic file on GitHub opens, where you need to click the **Edit this file** pencil icon.
+
+ 
+
+5. The topic opens in a line-numbered editing page where you can make changes to the file. Files in GitHub are written and edited using Markdown language. For help on using Markdown, see [Mastering Markdown](https://guides.github.com/features/mastering-markdown/). Select the **Preview changes** tab to view your changes as you go.
+
+6. When you're finished making changes, go to the **Propose file change** section at the bottom of the page:
+
+ - A brief title is required. By default, the title is the name of the file, but you can change it.
+ - Optionally, you can enter more details in the **Add an optional extended description** box.
+
+ When you're ready, click the green **Propose file change** button.
+
+ 
+
+7. On the **Comparing changes** page that appears, click the green **Create pull request** button.
+
+ 
+
+8. On the **Open a pull request** page that appears, click the green **Create pull request** button.
+
+ 
+
+> [!NOTE]
+> Your permissions in the repo determine what you see in the last several steps. People with no special privileges will see the **Propose file change** section and subsequent confirmation pages as described. People with permissions to create and approve their own pull requests will see a similar **Commit changes** section with extra options for creating a new branch and fewer confirmation pages.
The point is: click any green buttons that are presented to you until there are no more.
+
+The writer identified in the metadata of the topic will be notified and will eventually review and approve your changes so the topic will be updated on Microsoft Learn. If there are questions or issues with the updates, the writer will contact you.
+
## Microsoft Open Source Code of Conduct
+
This project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/).
-For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [opencode@microsoft.com](mailto:opencode@microsoft.com) with any additional questions or comments.
\ No newline at end of file
+
+For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [opencode@microsoft.com](mailto:opencode@microsoft.com) with any additional questions or comments.
+
+### Contributing
+
+This project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit .
+
+When you submit a pull request, a CLA-bot will automatically determine whether you need to provide a CLA and decorate the PR appropriately (e.g., label, comment). Simply follow the instructions provided by the bot. You will only need to do this once across all repos using our CLA.
+
+### Legal Notices
+
+Microsoft and any contributors grant you a license to the Microsoft documentation and other content in this repository under the [Creative Commons Attribution 4.0 International Public License](https://creativecommons.org/licenses/by/4.0/legalcode), see the [LICENSE](LICENSE) file, and grant you a license to any code in the repository under the [MIT License](https://opensource.org/licenses/MIT), see the [LICENSE-CODE](LICENSE-CODE) file.
+
+Microsoft, Windows, Microsoft Azure and/or other Microsoft products and services referenced in the documentation may be either trademarks or registered trademarks of Microsoft in the United States and/or other countries.
+
+The licenses for this project do not grant you rights to use any Microsoft names, logos, or trademarks. Microsoft's general trademark guidelines can be found at .
+
+Privacy information can be found at
+
+Microsoft and any contributors reserve all others rights, whether under their respective copyrights, patents, or trademarks, whether by implication, estoppel or otherwise.
From 5afac7ed8d6c34917a0a8e9701e5a06b334586be Mon Sep 17 00:00:00 2001
From: Jeff Borsecnik <36546697+jborsecnik@users.noreply.github.com>
Date: Fri, 16 Dec 2022 09:25:54 -0800
Subject: [PATCH 08/10] Update README.md
---
README.md | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/README.md b/README.md
index 0bc19b009f..29c01e584f 100644
--- a/README.md
+++ b/README.md
@@ -2,7 +2,7 @@
## Learn how to contribute
-Anyone who is interested can contribute to the topics. When you contribute, your work will go directly into the content set after being merged. It will then be published to [Microsoft Learn](https://learn.microsoft.com/) and you will be listed as a contributor at: .
+Anyone who is interested can contribute to the topics. When you contribute, your work will go directly into the content set after being merged. It will then be published to [Microsoft Learn](https://learn.microsoft.com/) and you will be listed as a contributor at: .
### Quickly update an article using GitHub.com
From a347e14ac63faed29787498f08ae9c29cdc96d3d Mon Sep 17 00:00:00 2001
From: Jeff Borsecnik <36546697+jborsecnik@users.noreply.github.com>
Date: Fri, 16 Dec 2022 16:52:06 -0800
Subject: [PATCH 09/10] Update README.md
---
README.md | 10 +++++-----
1 file changed, 5 insertions(+), 5 deletions(-)
diff --git a/README.md b/README.md
index 29c01e584f..98c771d56d 100644
--- a/README.md
+++ b/README.md
@@ -12,11 +12,11 @@ Contributors who only make infrequent or small updates can edit the file directl
2. Browse to the page you want to edit on Microsoft Learn.
3. On the right-hand side of the page, click **Edit** (pencil icon).
- 
+ 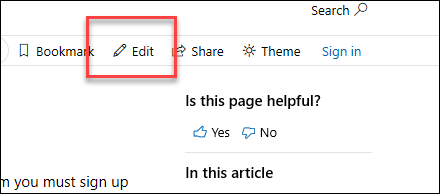
4. The corresponding topic file on GitHub opens, where you need to click the **Edit this file** pencil icon.
- 
+ 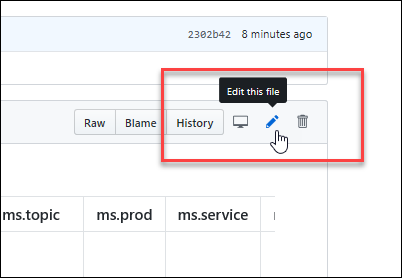
5. The topic opens in a line-numbered editing page where you can make changes to the file. Files in GitHub are written and edited using Markdown language. For help on using Markdown, see [Mastering Markdown](https://guides.github.com/features/mastering-markdown/). Select the **Preview changes** tab to view your changes as you go.
@@ -27,15 +27,15 @@ Contributors who only make infrequent or small updates can edit the file directl
When you're ready, click the green **Propose file change** button.
- 
+ 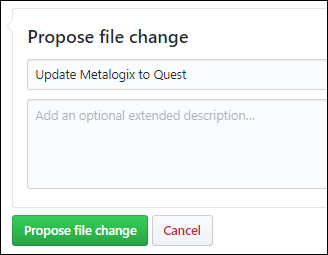
7. On the **Comparing changes** page that appears, click the green **Create pull request** button.
- 
+ 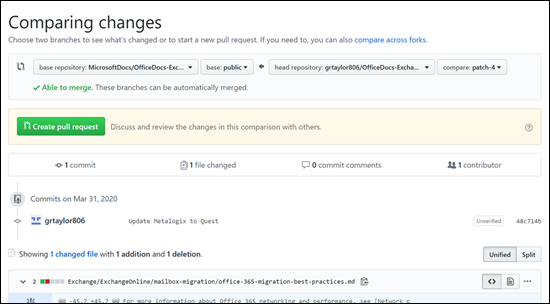
8. On the **Open a pull request** page that appears, click the green **Create pull request** button.
- 
+ 
> [!NOTE]
> Your permissions in the repo determine what you see in the last several steps. People with no special privileges will see the **Propose file change** section and subsequent confirmation pages as described. People with permissions to create and approve their own pull requests will see a similar **Commit changes** section with extra options for creating a new branch and fewer confirmation pages.
The point is: click any green buttons that are presented to you until there are no more.
From 71496988589b2ed0952461098b405db0ae8d381b Mon Sep 17 00:00:00 2001
From: Vinay Pamnani <37223378+vinaypamnani-msft@users.noreply.github.com>
Date: Tue, 3 Jan 2023 12:16:07 -0500
Subject: [PATCH 10/10] Update install-md-app-guard.md
---
.../microsoft-defender-application-guard/install-md-app-guard.md | 1 +
1 file changed, 1 insertion(+)
diff --git a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
index 97f4e14332..57977dcbe6 100644
--- a/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
+++ b/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard.md
@@ -15,6 +15,7 @@ ms.custom: asr
ms.technology: itpro-security
ms.collection:
- highpri
+ms.topic: how-to
---
# Prepare to install Microsoft Defender Application Guard