mirror of
https://github.com/MicrosoftDocs/windows-itpro-docs.git
synced 2025-05-18 08:17:23 +00:00
Merge branch 'main' into jgeurten-multi-base-considerations-com
This commit is contained in:
commit
6e39dcd3c4
@ -20284,6 +20284,16 @@
|
|||||||
"source_path": "windows/deployment/windows-autopatch/references/windows-autopatch-preview-addendum.md",
|
"source_path": "windows/deployment/windows-autopatch/references/windows-autopatch-preview-addendum.md",
|
||||||
"redirect_url": "/windows/deployment/windows-autopatch/overview/windows-autopatch-overview",
|
"redirect_url": "/windows/deployment/windows-autopatch/overview/windows-autopatch-overview",
|
||||||
"redirect_document_id": true
|
"redirect_document_id": true
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"source_path": "windows/security/identity-protection/hello-for-business/microsoft-compatible-security-key.md",
|
||||||
|
"redirect_url": "/azure/active-directory/authentication/howto-authentication-passwordless-security-key",
|
||||||
|
"redirect_document_id": false
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"source_path": "windows/security/identity-protection/hello-for-business/reset-security-key.md",
|
||||||
|
"redirect_url": "/azure/active-directory/authentication/howto-authentication-passwordless-security-key",
|
||||||
|
"redirect_document_id": false
|
||||||
}
|
}
|
||||||
]
|
]
|
||||||
}
|
}
|
||||||
|
|||||||
66
README.md
66
README.md
@ -1,3 +1,67 @@
|
|||||||
|
# Overview
|
||||||
|
|
||||||
|
## Learn how to contribute
|
||||||
|
|
||||||
|
Anyone who is interested can contribute to the topics. When you contribute, your work will go directly into the content set after being merged. It will then be published to [Microsoft Learn](https://learn.microsoft.com/) and you will be listed as a contributor at: <https://github.com/MicrosoftDocs/windows-docs-pr/graphs/contributors>.
|
||||||
|
|
||||||
|
### Quickly update an article using GitHub.com
|
||||||
|
|
||||||
|
Contributors who only make infrequent or small updates can edit the file directly on GitHub.com without having to install any additional software. This article shows you how. [This two-minute video](https://www.microsoft.com/videoplayer/embed/RE1XQTG) also covers how to contribute.
|
||||||
|
|
||||||
|
1. Make sure you're signed in to GitHub.com with your GitHub account.
|
||||||
|
2. Browse to the page you want to edit on Microsoft Learn.
|
||||||
|
3. On the right-hand side of the page, click **Edit** (pencil icon).
|
||||||
|
|
||||||
|
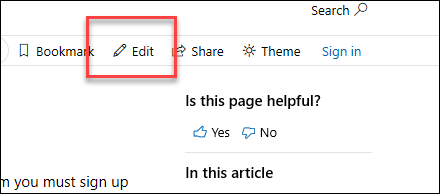
|
||||||
|
|
||||||
|
4. The corresponding topic file on GitHub opens, where you need to click the **Edit this file** pencil icon.
|
||||||
|
|
||||||
|
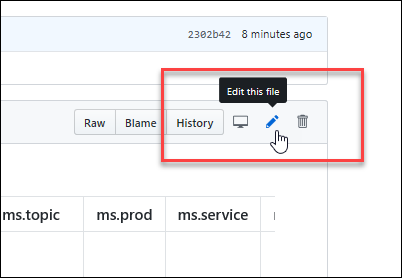
|
||||||
|
|
||||||
|
5. The topic opens in a line-numbered editing page where you can make changes to the file. Files in GitHub are written and edited using Markdown language. For help on using Markdown, see [Mastering Markdown](https://guides.github.com/features/mastering-markdown/). Select the **Preview changes** tab to view your changes as you go.
|
||||||
|
|
||||||
|
6. When you're finished making changes, go to the **Propose file change** section at the bottom of the page:
|
||||||
|
|
||||||
|
- A brief title is required. By default, the title is the name of the file, but you can change it.
|
||||||
|
- Optionally, you can enter more details in the **Add an optional extended description** box.
|
||||||
|
|
||||||
|
When you're ready, click the green **Propose file change** button.
|
||||||
|
|
||||||
|
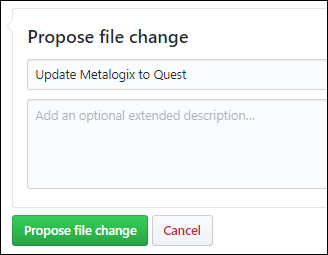
|
||||||
|
|
||||||
|
7. On the **Comparing changes** page that appears, click the green **Create pull request** button.
|
||||||
|
|
||||||
|
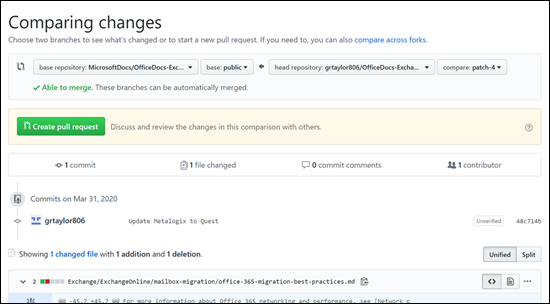
|
||||||
|
|
||||||
|
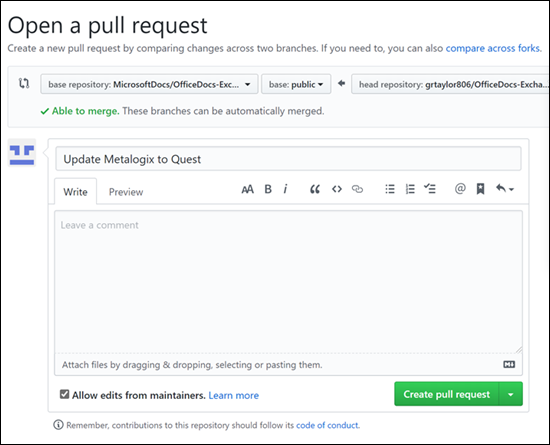
8. On the **Open a pull request** page that appears, click the green **Create pull request** button.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
> [!NOTE]
|
||||||
|
> Your permissions in the repo determine what you see in the last several steps. People with no special privileges will see the **Propose file change** section and subsequent confirmation pages as described. People with permissions to create and approve their own pull requests will see a similar **Commit changes** section with extra options for creating a new branch and fewer confirmation pages.<br/><br/>The point is: click any green buttons that are presented to you until there are no more.
|
||||||
|
|
||||||
|
The writer identified in the metadata of the topic will be notified and will eventually review and approve your changes so the topic will be updated on Microsoft Learn. If there are questions or issues with the updates, the writer will contact you.
|
||||||
|
|
||||||
## Microsoft Open Source Code of Conduct
|
## Microsoft Open Source Code of Conduct
|
||||||
|
|
||||||
This project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/).
|
This project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/).
|
||||||
For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [opencode@microsoft.com](mailto:opencode@microsoft.com) with any additional questions or comments.
|
|
||||||
|
For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [opencode@microsoft.com](mailto:opencode@microsoft.com) with any additional questions or comments.
|
||||||
|
|
||||||
|
### Contributing
|
||||||
|
|
||||||
|
This project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit <https://cla.microsoft.com>.
|
||||||
|
|
||||||
|
When you submit a pull request, a CLA-bot will automatically determine whether you need to provide a CLA and decorate the PR appropriately (e.g., label, comment). Simply follow the instructions provided by the bot. You will only need to do this once across all repos using our CLA.
|
||||||
|
|
||||||
|
### Legal Notices
|
||||||
|
|
||||||
|
Microsoft and any contributors grant you a license to the Microsoft documentation and other content in this repository under the [Creative Commons Attribution 4.0 International Public License](https://creativecommons.org/licenses/by/4.0/legalcode), see the [LICENSE](LICENSE) file, and grant you a license to any code in the repository under the [MIT License](https://opensource.org/licenses/MIT), see the [LICENSE-CODE](LICENSE-CODE) file.
|
||||||
|
|
||||||
|
Microsoft, Windows, Microsoft Azure and/or other Microsoft products and services referenced in the documentation may be either trademarks or registered trademarks of Microsoft in the United States and/or other countries.
|
||||||
|
|
||||||
|
The licenses for this project do not grant you rights to use any Microsoft names, logos, or trademarks. Microsoft's general trademark guidelines can be found at <https://go.microsoft.com/fwlink/?LinkID=254653>.
|
||||||
|
|
||||||
|
Privacy information can be found at <https://privacy.microsoft.com/>
|
||||||
|
|
||||||
|
Microsoft and any contributors reserve all others rights, whether under their respective copyrights, patents, or trademarks, whether by implication, estoppel or otherwise.
|
||||||
|
|||||||
@ -2,51 +2,17 @@
|
|||||||
|
|
||||||
|
|
||||||
|
|
||||||
## Week of September 19, 2022
|
## Week of December 19, 2022
|
||||||
|
|
||||||
|
|
||||||
| Published On |Topic title | Change |
|
| Published On |Topic title | Change |
|
||||||
|------|------------|--------|
|
|------|------------|--------|
|
||||||
| 9/20/2022 | [Education scenarios Microsoft Store for Education](/education/windows/education-scenarios-store-for-business) | modified |
|
| 12/22/2022 | [Windows 11 SE Overview](/education/windows/windows-11-se-overview) | modified |
|
||||||
|
|
||||||
|
|
||||||
## Week of September 12, 2022
|
## Week of December 12, 2022
|
||||||
|
|
||||||
|
|
||||||
| Published On |Topic title | Change |
|
| Published On |Topic title | Change |
|
||||||
|------|------------|--------|
|
|------|------------|--------|
|
||||||
| 9/13/2022 | [Chromebook migration guide (Windows 10)](/education/windows/chromebook-migration-guide) | modified |
|
| 12/13/2022 | [Configure Stickers for Windows 11 SE](/education/windows/edu-stickers) | modified |
|
||||||
| 9/14/2022 | [Windows 11 SE Overview](/education/windows/windows-11-se-overview) | modified |
|
|
||||||
| 9/14/2022 | [Windows 11 SE settings list](/education/windows/windows-11-se-settings-list) | modified |
|
|
||||||
|
|
||||||
|
|
||||||
## Week of September 05, 2022
|
|
||||||
|
|
||||||
|
|
||||||
| Published On |Topic title | Change |
|
|
||||||
|------|------------|--------|
|
|
||||||
| 9/8/2022 | [Education scenarios Microsoft Store for Education](/education/windows/education-scenarios-store-for-business) | modified |
|
|
||||||
| 9/8/2022 | [Get Minecraft Education Edition](/education/windows/get-minecraft-for-education) | modified |
|
|
||||||
| 9/8/2022 | [For teachers get Minecraft Education Edition](/education/windows/teacher-get-minecraft) | modified |
|
|
||||||
| 9/9/2022 | [Take tests in Windows](/education/windows/take-tests-in-windows-10) | modified |
|
|
||||||
|
|
||||||
|
|
||||||
## Week of August 29, 2022
|
|
||||||
|
|
||||||
|
|
||||||
| Published On |Topic title | Change |
|
|
||||||
|------|------------|--------|
|
|
||||||
| 8/31/2022 | [Configure applications with Microsoft Intune](/education/windows/tutorial-school-deployment/configure-device-apps) | added |
|
|
||||||
| 8/31/2022 | [Configure and secure devices with Microsoft Intune](/education/windows/tutorial-school-deployment/configure-device-settings) | added |
|
|
||||||
| 8/31/2022 | [Configure devices with Microsoft Intune](/education/windows/tutorial-school-deployment/configure-devices-overview) | added |
|
|
||||||
| 8/31/2022 | [Enrollment in Intune with standard out-of-box experience (OOBE)](/education/windows/tutorial-school-deployment/enroll-aadj) | added |
|
|
||||||
| 8/31/2022 | [Enrollment in Intune with Windows Autopilot](/education/windows/tutorial-school-deployment/enroll-autopilot) | added |
|
|
||||||
| 8/31/2022 | [Device enrollment overview](/education/windows/tutorial-school-deployment/enroll-overview) | added |
|
|
||||||
| 8/31/2022 | [Enrollment of Windows devices with provisioning packages](/education/windows/tutorial-school-deployment/enroll-package) | added |
|
|
||||||
| 8/31/2022 | [Introduction](/education/windows/tutorial-school-deployment/index) | added |
|
|
||||||
| 8/31/2022 | [Manage devices with Microsoft Intune](/education/windows/tutorial-school-deployment/manage-overview) | added |
|
|
||||||
| 8/31/2022 | [Management functionalities for Surface devices](/education/windows/tutorial-school-deployment/manage-surface-devices) | added |
|
|
||||||
| 8/31/2022 | [Reset and wipe Windows devices](/education/windows/tutorial-school-deployment/reset-wipe) | added |
|
|
||||||
| 8/31/2022 | [Set up Azure Active Directory](/education/windows/tutorial-school-deployment/set-up-azure-ad) | added |
|
|
||||||
| 8/31/2022 | [Set up device management](/education/windows/tutorial-school-deployment/set-up-microsoft-intune) | added |
|
|
||||||
| 8/31/2022 | [Troubleshoot Windows devices](/education/windows/tutorial-school-deployment/troubleshoot-overview) | added |
|
|
||||||
|
|||||||
@ -79,71 +79,71 @@ The following table lists all the applications included in Windows 11 SE and the
|
|||||||
|
|
||||||
The following applications can also run on Windows 11 SE, and can be deployed using Intune for Education. For more information, see [Configure applications with Microsoft Intune][EDUWIN-1]
|
The following applications can also run on Windows 11 SE, and can be deployed using Intune for Education. For more information, see [Configure applications with Microsoft Intune][EDUWIN-1]
|
||||||
|
|
||||||
| Application | Supported version | App Type | Vendor |
|
| Application | Supported version | App Type | Vendor |
|
||||||
|-----------------------------------------|-------------------|----------|------------------------------|
|
|-------------------------------------------|-------------------|----------|-------------------------------------------|
|
||||||
| 3d builder | 15.2.10821.1070 | Win32 | Microsoft |
|
| `3d builder` | `18.0.1931.0` | Win32 | `Microsoft` |
|
||||||
|Absolute Software Endpoint Agent | 7.20.0.1 | Win32 | Absolute Software Corporation|
|
| `Absolute Software Endpoint Agent` | 7.20.0.1 | Win32 | `Absolute Software Corporation` |
|
||||||
| AirSecure | 8.0.0 | Win32 | AIR |
|
| `AirSecure` | 8.0.0 | Win32 | `AIR` |
|
||||||
| Alertus Desktop | 5.4.44.0 | Win32 | Alertus technologies |
|
| `Alertus Desktop` | 5.4.48.0 | Win32 | `Alertus technologies` |
|
||||||
| Brave Browser | 106.0.5249.65 | Win32 | Brave |
|
| `Brave Browser` | 106.0.5249.119 | Win32 | `Brave` |
|
||||||
| Bulb Digital Portfolio | 0.0.7.0 | Store | Bulb |
|
| `Bulb Digital Portfolio` | 0.0.7.0 | `Store` | `Bulb` |
|
||||||
| CA Secure Browser | 14.0.0 | Win32 | Cambium Development |
|
| `CA Secure Browser` | 14.0.0 | Win32 | `Cambium Development` |
|
||||||
| Cisco Umbrella | 3.0.110.0 | Win32 | Cisco |
|
| `Cisco Umbrella` | 3.0.110.0 | Win32 | `Cisco` |
|
||||||
| CKAuthenticator | 3.6+ | Win32 | Content Keeper |
|
| `CKAuthenticator` | 3.6+ | Win32 | `Content Keeper` |
|
||||||
| Class Policy | 114.0.0 | Win32 | Class Policy |
|
| `Class Policy` | 114.0.0 | Win32 | `Class Policy` |
|
||||||
| Classroom.cloud | 1.40.0004 | Win32 | NetSupport |
|
| `Classroom.cloud` | 1.40.0004 | Win32 | `NetSupport` |
|
||||||
| CoGat Secure Browser | 11.0.0.19 | Win32 | Riverside Insights |
|
| `CoGat Secure Browser` | 11.0.0.19 | Win32 | `Riverside Insights` |
|
||||||
| Dragon Professional Individual | 15.00.100 | Win32 | Nuance Communications |
|
| `Dragon Professional Individual` | 15.00.100 | Win32 | `Nuance Communications` |
|
||||||
| DRC INSIGHT Online Assessments | 12.0.0.0 | Store | Data recognition Corporation |
|
| `DRC INSIGHT Online Assessments` | 12.0.0.0 | `Store` | `Data recognition Corporation` |
|
||||||
| Duo from Cisco | 2.25.0 | Win32 | Cisco |
|
| `Duo from Cisco` | 3.0.0 | Win32 | `Cisco` |
|
||||||
| e-Speaking Voice and Speech recognition | 4.4.0.8 | Win32 | e-speaking |
|
| `e-Speaking Voice and Speech recognition` | 4.4.0.8 | Win32 | `e-speaking` |
|
||||||
| Epson iProjection | 3.31 | Win32 | Epson |
|
| `Epson iProjection` | 3.31 | Win32 | `Epson` |
|
||||||
| eTests | 4.0.25 | Win32 | CASAS |
|
| `eTests` | 4.0.25 | Win32 | `CASAS` |
|
||||||
| FortiClient | 7.2.0.4034+ | Win32 | Fortinet |
|
| `FortiClient` | 7.2.0.4034+ | Win32 | `Fortinet` |
|
||||||
| Free NaturalReader | 16.1.2 | Win32 | Natural Soft |
|
| `Free NaturalReader` | 16.1.2 | Win32 | `Natural Soft` |
|
||||||
| Ghotit Real Writer & Reader | 10.14.2.3 | Win32 | Ghotit Ltd |
|
| `Ghotit Real Writer & Reader` | 10.14.2.3 | Win32 | `Ghotit Ltd` |
|
||||||
| GoGuardian | 1.4.4 | Win32 | GoGuardian |
|
| `GoGuardian` | 1.4.4 | Win32 | `GoGuardian` |
|
||||||
| Google Chrome | 102.0.5005.115 | Win32 | Google |
|
| `Google Chrome` | 102.0.5005.115 | Win32 | `Google` |
|
||||||
| Illuminate Lockdown Browser | 2.0.5 | Win32 | Illuminate Education |
|
| `Illuminate Lockdown Browser` | 2.0.5 | Win32 | `Illuminate Education` |
|
||||||
| Immunet | 7.5.0.20795 | Win32 | Immunet |
|
| `Immunet` | 7.5.8.21178 | Win32 | `Immunet` |
|
||||||
| Impero Backdrop Client | 4.4.86 | Win32 | Impero Software |
|
| `Impero Backdrop Client` | 4.4.86 | Win32 | `Impero Software` |
|
||||||
| Inspiration 10 | 10.11 | Win32 | TechEdology Ltd |
|
| `Inspiration 10` | 10.11 | Win32 | `TechEdology Ltd` |
|
||||||
| JAWS for Windows | 2022.2112.24 | Win32 | Freedom Scientific |
|
| `JAWS for Windows` | 2022.2112.24 | Win32 | `Freedom Scientific` |
|
||||||
| Kite Student Portal | 9.0.0.0 | Win32 | Dynamic Learning Maps |
|
| `Kite Student Portal` | 9.0.0.0 | Win32 | `Dynamic Learning Maps` |
|
||||||
| Kortext | 2.3.433.0 | Store | Kortext |
|
| `Kortext` | 2.3.433.0 | `Store` | `Kortext` |
|
||||||
| Kurzweil 3000 Assistive Learning | 20.13.0000 | Win32 | Kurzweil Educational Systems |
|
| `Kurzweil 3000 Assistive Learning` | 20.13.0000 | Win32 | `Kurzweil Educational Systems` |
|
||||||
| LanSchool Classic | 9.1.0.46 | Win32 | Stoneware, Inc. |
|
| `LanSchool Classic` | 9.1.0.46 | Win32 | `Stoneware, Inc.` |
|
||||||
| LanSchool Air | 2.0.13312 | Win32 | Stoneware, Inc. |
|
| `LanSchool Air` | 2.0.13312 | Win32 | `Stoneware, Inc.` |
|
||||||
| Lightspeed Smart Agent | 1.9.1 | Win32 | Lightspeed Systems |
|
| `Lightspeed Smart Agent` | 1.9.1 | Win32 | `Lightspeed Systems` |
|
||||||
| MetaMoJi ClassRoom | 3.12.4.0 | Store | MetaMoJi Corporation |
|
| `MetaMoJi ClassRoom` | 3.12.4.0 | `Store` | `MetaMoJi Corporation` |
|
||||||
| Microsoft Connect | 10.0.22000.1 | Store | Microsoft |
|
| `Microsoft Connect` | 10.0.22000.1 | `Store` | `Microsoft` |
|
||||||
| Mozilla Firefox | 99.0.1 | Win32 | Mozilla |
|
| `Mozilla Firefox` | 105.0.0 | Win32 | `Mozilla` |
|
||||||
| NAPLAN | 2.5.0 | Win32 | NAP |
|
| `NAPLAN` | 2.5.0 | Win32 | `NAP` |
|
||||||
| Netref Student | 22.2.0 | Win32 | NetRef |
|
| `Netref Student` | 22.2.0 | Win32 | `NetRef` |
|
||||||
| NetSupport Manager | 12.01.0014 | Win32 | NetSupport |
|
| `NetSupport Manager` | 12.01.0014 | Win32 | `NetSupport` |
|
||||||
| NetSupport Notify | 5.10.1.215 | Win32 | NetSupport |
|
| `NetSupport Notify` | 5.10.1.215 | Win32 | `NetSupport` |
|
||||||
| NetSupport School | 14.00.0011 | Win32 | NetSupport |
|
| `NetSupport School` | 14.00.0012 | Win32 | `NetSupport` |
|
||||||
| NextUp Talker | 1.0.49 | Win32 | NextUp Technologies |
|
| `NextUp Talker` | 1.0.49 | Win32 | `NextUp Technologies` |
|
||||||
| NonVisual Desktop Access | 2021.3.1 | Win32 | NV Access |
|
| `NonVisual Desktop Access` | 2021.3.1 | Win32 | `NV Access` |
|
||||||
| NWEA Secure Testing Browser | 5.4.356.0 | Win32 | NWEA |
|
| `NWEA Secure Testing Browser` | 5.4.356.0 | Win32 | `NWEA` |
|
||||||
| PaperCut | 22.0.6 | Win32 | PaperCut Software International Pty Ltd |
|
| `PaperCut` | 22.0.6 | Win32 | `PaperCut Software International Pty Ltd` |
|
||||||
| Pearson TestNav | 1.10.2.0 | Store | Pearson |
|
| `Pearson TestNav` | 1.10.2.0 | `Store` | `Pearson` |
|
||||||
| Questar Secure Browser | 4.8.3.376 | Win32 | Questar, Inc |
|
| `Questar Secure Browser` | 5.0.1.456 | Win32 | `Questar, Inc` |
|
||||||
| ReadAndWriteForWindows | 12.0.60.0 | Win32 | Texthelp Ltd. |
|
| `ReadAndWriteForWindows` | 12.0.74 | Win32 | `Texthelp Ltd.` |
|
||||||
| Remote Desktop client (MSRDC) | 1.2.3213.0 | Win32 | Microsoft |
|
| `Remote Desktop client (MSRDC)` | 1.2.3213.0 | Win32 | `Microsoft` |
|
||||||
| Remote Help | 3.8.0.12 | Win32 | Microsoft |
|
| `Remote Help` | 4.0.1.13 | Win32 | `Microsoft` |
|
||||||
| Respondus Lockdown Browser | 2.0.9.00 | Win32 | Respondus |
|
| `Respondus Lockdown Browser` | 2.0.9.03 | Win32 | `Respondus` |
|
||||||
| Safe Exam Browser | 3.3.2.413 | Win32 | Safe Exam Browser |
|
| `Safe Exam Browser` | 3.3.2.413 | Win32 | `Safe Exam Browser` |
|
||||||
| Senso.Cloud | 2021.11.15.0 | Win32 | Senso.Cloud |
|
| `Senso.Cloud` | 2021.11.15.0 | Win32 | `Senso.Cloud` |
|
||||||
| Smoothwall Monitor | 2.8.0 | Win32 | Smoothwall Ltd
|
| `Smoothwall Monitor` | 2.8.0 | Win32 | `Smoothwall Ltd` |
|
||||||
| SuperNova Magnifier & Screen Reader | 21.02 | Win32 | Dolphin Computer Access |
|
| `SuperNova Magnifier & Screen Reader` | 21.02 | Win32 | `Dolphin Computer Access` |
|
||||||
| SuperNova Magnifier & Speech | 21.02 | Win32 | Dolphin Computer Access |
|
| `SuperNova Magnifier & Speech` | 21.02 | Win32 | `Dolphin Computer Access` |
|
||||||
| VitalSourceBookShelf | 10.2.26.0 | Win32 | VitalSource Technologies Inc |
|
| `VitalSourceBookShelf` | 10.2.26.0 | Win32 | `VitalSource Technologies Inc` |
|
||||||
| Winbird | 19 | Win32 | Winbird Co., Ltd. |
|
| `Winbird` | 19 | Win32 | `Winbird Co., Ltd.` |
|
||||||
| WordQ | 5.4.23 | Win32 | Mathetmots |
|
| `WordQ` | 5.4.23 | Win32 | `Mathetmots` |
|
||||||
| Zoom | 5.9.1 (2581) | Win32 | Zoom |
|
| `Zoom` | 5.12.8 (10232) | Win32 | `Zoom` |
|
||||||
| ZoomText Fusion | 2022.2109.10 | Win32 | Freedom Scientific |
|
| `ZoomText Fusion` | 2022.2109.10 | Win32 | `Freedom Scientific` |
|
||||||
| ZoomText Magnifier/Reader | 2022.2109.25 | Win32 | Freedom Scientific |
|
| `ZoomText Magnifier/Reader` | 2022.2109.25 | Win32 | `Freedom Scientific` |
|
||||||
|
|
||||||
## Add your own applications
|
## Add your own applications
|
||||||
|
|
||||||
|
|||||||
@ -1,6 +1,6 @@
|
|||||||
---
|
---
|
||||||
title: Azure Active Directory integration with MDM
|
title: Azure Active Directory integration with MDM
|
||||||
description: Azure Active Directory is the world largest enterprise cloud identity management service.
|
description: Azure Active Directory is the world's largest enterprise cloud identity management service.
|
||||||
ms.reviewer:
|
ms.reviewer:
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.author: vinpa
|
ms.author: vinpa
|
||||||
@ -14,7 +14,7 @@ ms.date: 12/31/2017
|
|||||||
|
|
||||||
# Azure Active Directory integration with MDM
|
# Azure Active Directory integration with MDM
|
||||||
|
|
||||||
Azure Active Directory is the world largest enterprise cloud identity management service. It’s used by organizations to access Office 365 and business applications from Microsoft and third-party software as a service (SaaS) vendors. Many of the rich Windows 10 experiences for organizational users (such as store access or OS state roaming) use Azure AD as the underlying identity infrastructure. Windows integrates with Azure AD, allowing devices to be registered in Azure AD and enrolled into MDM in an integrated flow.
|
Azure Active Directory is the world's largest enterprise cloud identity management service. It’s used by organizations to access Office 365 and business applications from Microsoft and third-party software as a service (SaaS) vendors. Many of the rich Windows 10 experiences for organizational users (such as store access or OS state roaming) use Azure AD as the underlying identity infrastructure. Windows integrates with Azure AD, allowing devices to be registered in Azure AD and enrolled into MDM in an integrated flow.
|
||||||
|
|
||||||
Once a device is enrolled in MDM, the MDM:
|
Once a device is enrolled in MDM, the MDM:
|
||||||
|
|
||||||
|
|||||||
@ -52,6 +52,11 @@ Firewall
|
|||||||
------------DisableStealthMode
|
------------DisableStealthMode
|
||||||
------------Shielded
|
------------Shielded
|
||||||
------------DisableUnicastResponsesToMulticastBroadcast
|
------------DisableUnicastResponsesToMulticastBroadcast
|
||||||
|
------------EnableLogDroppedPackets
|
||||||
|
------------EnableLogSuccessConnections
|
||||||
|
------------EnableLogIgnoredRules
|
||||||
|
------------LogMaxFileSize
|
||||||
|
------------LogFilePath
|
||||||
------------DisableInboundNotifications
|
------------DisableInboundNotifications
|
||||||
------------AuthAppsAllowUserPrefMerge
|
------------AuthAppsAllowUserPrefMerge
|
||||||
------------GlobalPortsAllowUserPrefMerge
|
------------GlobalPortsAllowUserPrefMerge
|
||||||
@ -65,6 +70,11 @@ Firewall
|
|||||||
------------DisableStealthMode
|
------------DisableStealthMode
|
||||||
------------Shielded
|
------------Shielded
|
||||||
------------DisableUnicastResponsesToMulticastBroadcast
|
------------DisableUnicastResponsesToMulticastBroadcast
|
||||||
|
------------EnableLogDroppedPackets
|
||||||
|
------------EnableLogSuccessConnections
|
||||||
|
------------EnableLogIgnoredRules
|
||||||
|
------------LogMaxFileSize
|
||||||
|
------------LogFilePath
|
||||||
------------DisableInboundNotifications
|
------------DisableInboundNotifications
|
||||||
------------AuthAppsAllowUserPrefMerge
|
------------AuthAppsAllowUserPrefMerge
|
||||||
------------GlobalPortsAllowUserPrefMerge
|
------------GlobalPortsAllowUserPrefMerge
|
||||||
@ -78,6 +88,11 @@ Firewall
|
|||||||
------------DisableStealthMode
|
------------DisableStealthMode
|
||||||
------------Shielded
|
------------Shielded
|
||||||
------------DisableUnicastResponsesToMulticastBroadcast
|
------------DisableUnicastResponsesToMulticastBroadcast
|
||||||
|
------------EnableLogDroppedPackets
|
||||||
|
------------EnableLogSuccessConnections
|
||||||
|
------------EnableLogIgnoredRules
|
||||||
|
------------LogMaxFileSize
|
||||||
|
------------LogFilePath
|
||||||
------------DisableInboundNotifications
|
------------DisableInboundNotifications
|
||||||
------------AuthAppsAllowUserPrefMerge
|
------------AuthAppsAllowUserPrefMerge
|
||||||
------------GlobalPortsAllowUserPrefMerge
|
------------GlobalPortsAllowUserPrefMerge
|
||||||
@ -223,6 +238,25 @@ Boolean value. If it's true, unicast responses to multicast broadcast traffic ar
|
|||||||
Default value is false.
|
Default value is false.
|
||||||
Value type is bool. Supported operations are Add, Get and Replace.
|
Value type is bool. Supported operations are Add, Get and Replace.
|
||||||
|
|
||||||
|
<a href="" id="enablelogdroppedpackets"></a>**/EnableLogDroppedPackets**
|
||||||
|
Boolean value. If this value is true, firewall will log all dropped packets. The merge law for this option is to let "on" values win.
|
||||||
|
Default value is false. Supported operations are Get and Replace.
|
||||||
|
|
||||||
|
<a href="" id="enablelogsuccessconnections"></a>**/EnableLogSuccessConnections**
|
||||||
|
Boolean value. If this value is true, firewall will log all successful inbound connections. The merge law for this option is to let "on" values win.
|
||||||
|
Default value is false. Supported operations are Get and Replace.
|
||||||
|
|
||||||
|
<a href="" id="enablelogignoredrules"></a>**/EnableLogIgnoredRules**
|
||||||
|
Boolean value. If this value is true, firewall will log ignored firewall rules. The merge law for this option is to let "on" values win.
|
||||||
|
Default value is false. Supported operations are Get and Replace.
|
||||||
|
|
||||||
|
<a href="" id="logmaxfilesize"></a>**/LogMaxFileSize**
|
||||||
|
Integer value that specifies the size, in kilobytes, of the log file where dropped packets, successful connections and ignored rules are logged. The merge law for this option is to let the value of the GroupPolicyRSoPStore win if it is configured, otherwise the MdmStore value wins if it is configured, otherwise the local store value is used.
|
||||||
|
Default value is 1024. Supported operations are Get and Replace
|
||||||
|
|
||||||
|
<a href="" id="logfilepath"></a>**/LogFilePath**
|
||||||
|
String value that represents the file path to the log where firewall logs dropped packets, successful connections and ignored rules. The merge law for this option is to let the value of the GroupPolicyRSoPStore win if it is configured, otherwise the MdmStore value wins if it is configured, otherwise the local store value is used. Default value is "%systemroot%\system32\LogFiles\Firewall\pfirewall.log". Supported operations are Get and Replace
|
||||||
|
|
||||||
<a href="" id="disableinboundnotifications"></a>**/DisableInboundNotifications**
|
<a href="" id="disableinboundnotifications"></a>**/DisableInboundNotifications**
|
||||||
Boolean value. If this value is false, the firewall MAY display a notification to the user when an application is blocked from listening on a port. If this value is on, the firewall MUST NOT display such a notification. The merge law for this option is to let the value of the GroupPolicyRSoPStore win if it's configured; otherwise, the local store value is used.
|
Boolean value. If this value is false, the firewall MAY display a notification to the user when an application is blocked from listening on a port. If this value is on, the firewall MUST NOT display such a notification. The merge law for this option is to let the value of the GroupPolicyRSoPStore win if it's configured; otherwise, the local store value is used.
|
||||||
Default value is false.
|
Default value is false.
|
||||||
@ -349,7 +383,7 @@ Value type is string. Supported operations are Add, Get, Replace, and Delete.
|
|||||||
|
|
||||||
|
|
||||||
<a href="" id="icmptypesandcodes"></a>**FirewallRules/_FirewallRuleName_/IcmpTypesAndCodes**
|
<a href="" id="icmptypesandcodes"></a>**FirewallRules/_FirewallRuleName_/IcmpTypesAndCodes**
|
||||||
ICMP types and codes applicable to the firewall rule. To specify all ICMP types and codes, use the “\*” character. For specific ICMP types and codes, use the “:” character to separate the type and code, for example, 3:4, 1:\*. The “\*” character can be used to represent any code. The “\*” character cannot be used to specify any type; examples such as “\*:4” or “\*:\*” are invalid.
|
Comma separated list of ICMP types and codes applicable to the firewall rule. To specify all ICMP types and codes, use the “\*” character. For specific ICMP types and codes, use the “:” character to separate the type and code, for example, 3:4, 1:\*. The “\*” character can be used to represent any code. The “\*” character cannot be used to specify any type; examples such as “\*:4” or “\*:\*” are invalid.
|
||||||
If not specified, the default is All.
|
If not specified, the default is All.
|
||||||
Value type is string. Supported operations are Add, Get, Replace, and Delete.
|
Value type is string. Supported operations are Add, Get, Replace, and Delete.
|
||||||
|
|
||||||
@ -431,6 +465,7 @@ Comma separated list of interface types. Valid values:
|
|||||||
- RemoteAccess
|
- RemoteAccess
|
||||||
- Wireless
|
- Wireless
|
||||||
- Lan
|
- Lan
|
||||||
|
- MBB (i.e. Mobile Broadband)
|
||||||
|
|
||||||
If not specified, the default is All.
|
If not specified, the default is All.
|
||||||
Value type is string. Supported operations are Get and Replace.
|
Value type is string. Supported operations are Get and Replace.
|
||||||
|
|||||||
@ -8,7 +8,7 @@ ms.topic: article
|
|||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-manage
|
ms.technology: itpro-manage
|
||||||
author: vinaypamnani-msft
|
author: vinaypamnani-msft
|
||||||
ms.date:
|
ms.date: 4/5/2022
|
||||||
---
|
---
|
||||||
|
|
||||||
# Device HealthAttestation CSP
|
# Device HealthAttestation CSP
|
||||||
|
|||||||
@ -702,11 +702,7 @@ ADMX Info:
|
|||||||
<!--Description-->
|
<!--Description-->
|
||||||
Set this policy to restrict peer selection to a specific source. Available options are: 1 = Active Directory Site, 2 = Authenticated domain SID, 3 = DHCP Option ID, 4 = DNS Suffix, 5 = Azure Active Directory.
|
Set this policy to restrict peer selection to a specific source. Available options are: 1 = Active Directory Site, 2 = Authenticated domain SID, 3 = DHCP Option ID, 4 = DNS Suffix, 5 = Azure Active Directory.
|
||||||
|
|
||||||
When set, the Group ID will be assigned automatically from the selected source.
|
When set, the Group ID is assigned automatically from the selected source. If you set this policy, the GroupID policy will be ignored. The default behavior, when neither the GroupID or GroupIDSource policies are set, is to determine the Group ID using AD Site (1), Authenticated domain SID (2) or AAD Tenant ID (5), in that order. If GroupIDSource is set to either DHCP Option ID (3) or DNS Suffix (4) and those methods fail, the default behavior is used instead. The option set in this policy only applies to Group (2) download mode. If Group (2) isn't set as Download mode, this policy will be ignored. If you set the value to anything other than 0-5, the policy is ignored.
|
||||||
|
|
||||||
If you set this policy, the GroupID policy will be ignored.
|
|
||||||
|
|
||||||
The options set in this policy only apply to Group (2) download mode. If Group (2) isn't set as Download mode, this policy will be ignored.
|
|
||||||
|
|
||||||
For option 3 - DHCP Option ID, the client will query DHCP Option ID 234 and use the returned GUID value as the Group ID.
|
For option 3 - DHCP Option ID, the client will query DHCP Option ID 234 and use the returned GUID value as the Group ID.
|
||||||
|
|
||||||
|
|||||||
@ -337,7 +337,7 @@ To exit the assigned access (kiosk) app, press **Ctrl + Alt + Del**, and then si
|
|||||||
|
|
||||||
If you press **Ctrl + Alt + Del** and do not sign in to another account, after a set time, assigned access will resume. The default time is 30 seconds, but you can change that in the following registry key:
|
If you press **Ctrl + Alt + Del** and do not sign in to another account, after a set time, assigned access will resume. The default time is 30 seconds, but you can change that in the following registry key:
|
||||||
|
|
||||||
`HKEY\_LOCAL\_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI`
|
`HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI`
|
||||||
|
|
||||||
To change the default time for assigned access to resume, add *IdleTimeOut* (DWORD) and enter the value data as milliseconds in hexadecimal.
|
To change the default time for assigned access to resume, add *IdleTimeOut* (DWORD) and enter the value data as milliseconds in hexadecimal.
|
||||||
|
|
||||||
|
|||||||
@ -1,4 +1,4 @@
|
|||||||
- name: Delivery Optimization for Windows client and Microsoft Connected Cache
|
- name: Delivery Optimization for Windows and Microsoft Connected Cache
|
||||||
href: index.yml
|
href: index.yml
|
||||||
- name: What's new
|
- name: What's new
|
||||||
href: whats-new-do.md
|
href: whats-new-do.md
|
||||||
@ -9,9 +9,9 @@
|
|||||||
href: waas-delivery-optimization.md
|
href: waas-delivery-optimization.md
|
||||||
- name: Delivery Optimization Frequently Asked Questions
|
- name: Delivery Optimization Frequently Asked Questions
|
||||||
href: waas-delivery-optimization-faq.yml
|
href: waas-delivery-optimization-faq.yml
|
||||||
- name: Configure Delivery Optimization for Windows clients
|
- name: Configure Delivery Optimization for Windows
|
||||||
items:
|
items:
|
||||||
- name: Windows client Delivery Optimization settings
|
- name: Windows Delivery Optimization settings
|
||||||
href: waas-delivery-optimization-setup.md#recommended-delivery-optimization-settings
|
href: waas-delivery-optimization-setup.md#recommended-delivery-optimization-settings
|
||||||
- name: Configure Delivery Optimization settings using Microsoft Intune
|
- name: Configure Delivery Optimization settings using Microsoft Intune
|
||||||
href: /mem/intune/configuration/delivery-optimization-windows
|
href: /mem/intune/configuration/delivery-optimization-windows
|
||||||
|
|||||||
@ -2,15 +2,14 @@
|
|||||||
title: Don't Remove images under do/images/elixir_ux - used by Azure portal Diagnose/Solve feature UI
|
title: Don't Remove images under do/images/elixir_ux - used by Azure portal Diagnose/Solve feature UI
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
description: Elixir images read me file
|
description: Elixir images read me file
|
||||||
keywords: updates, downloads, network, bandwidth
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: deploy
|
ms.mktglfcycl: deploy
|
||||||
audience: itpro
|
audience: itpro
|
||||||
author: nidos
|
author: nidos
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: nidos
|
ms.author: nidos
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Read Me
|
# Read Me
|
||||||
|
|||||||
@ -28,15 +28,15 @@ ms.localizationpriority: medium
|
|||||||
| TotalBytesDownloaded | The number of bytes from any source downloaded so far |
|
| TotalBytesDownloaded | The number of bytes from any source downloaded so far |
|
||||||
| PercentPeerCaching |The percentage of bytes downloaded from peers versus over HTTP |
|
| PercentPeerCaching |The percentage of bytes downloaded from peers versus over HTTP |
|
||||||
| BytesFromPeers | Total bytes downloaded from peer devices (sum of bytes downloaded from LAN, Group, and Internet Peers) |
|
| BytesFromPeers | Total bytes downloaded from peer devices (sum of bytes downloaded from LAN, Group, and Internet Peers) |
|
||||||
| BytesfromHTTP | Total number of bytes received over HTTP |
|
| BytesfromHTTP | Total number of bytes received over HTTP. This represents all HTTP sources, which includes BytesFromCacheServer |
|
||||||
| Status | Current state of the operation. Possible values are: **Downloading** (download in progress); **Complete** (download completed, but is not uploading yet); **Caching** (download completed successfully and is ready to upload or uploading); **Paused** (download/upload paused by caller) |
|
| Status | Current state of the operation. Possible values are: **Downloading** (download in progress); **Complete** (download completed, but is not uploading yet); **Caching** (download completed successfully and is ready to upload or uploading); **Paused** (download/upload paused by caller) |
|
||||||
| Priority | Priority of the download; values are **foreground** or **background** |
|
| Priority | Priority of the download; values are **foreground** or **background** |
|
||||||
| BytesFromCacheServer | Total number of bytes received from cache server |
|
| BytesFromCacheServer | Total number of bytes received from cache server (MCC) |
|
||||||
| BytesFromLanPeers | Total number of bytes received from peers found on the LAN |
|
| BytesFromLanPeers | Total number of bytes received from peers found on the LAN |
|
||||||
| BytesFromGroupPeers | Total number of bytes received from peers found in the group |
|
| BytesFromGroupPeers | Total number of bytes received from peers found in the group. (Note: Group mode is LAN + Group. If peers are found on the LAN, those bytes will be registered in 'BytesFromLANPeers'.) |
|
||||||
| BytesFromInternetPeers | Total number of bytes received from internet peers |
|
| BytesFromInternetPeers | Total number of bytes received from internet peers |
|
||||||
| BytesToLanPeers | Total number of bytes delivered from peers found on the LAN |
|
| BytesToLanPeers | Total number of bytes delivered from peers found on the LAN |
|
||||||
| BytesToGroupPeers | Total number of bytes delivered from peers found in the group |
|
| BytesToGroupPeers | Total number of bytes delivered from peers found in the group |
|
||||||
| BytesToInternetPeers | Total number of bytes delivered from peers found on the LAN |
|
| BytesToInternetPeers | Total number of bytes delivered from peers found on the LAN |
|
||||||
| DownloadDuration | Total download time in seconds |
|
| DownloadDuration | Total download time in seconds |
|
||||||
| HttpConnectionCount | |
|
| HttpConnectionCount | |
|
||||||
|
|||||||
@ -1,7 +1,7 @@
|
|||||||
### YamlMime:Landing
|
### YamlMime:Landing
|
||||||
|
|
||||||
title: Delivery Optimization # < 60 chars
|
title: Delivery Optimization # < 60 chars
|
||||||
summary: Set up peer to peer downloads for Windows Updates and learn about Microsoft Connected Cache. # < 160 chars
|
summary: Set up peer to peer downloads for Microsoft content supported by Delivery Optimization and learn about Microsoft Connected Cache. # < 160 chars
|
||||||
|
|
||||||
metadata:
|
metadata:
|
||||||
title: Delivery Optimization # Required; page title displayed in search results. Include the brand. < 60 chars.
|
title: Delivery Optimization # Required; page title displayed in search results. Include the brand. < 60 chars.
|
||||||
@ -36,7 +36,7 @@ landingContent:
|
|||||||
|
|
||||||
|
|
||||||
# Card (optional)
|
# Card (optional)
|
||||||
- title: Configure Delivery Optimization on Windows clients
|
- title: Configure Delivery Optimization on Windows
|
||||||
linkLists:
|
linkLists:
|
||||||
- linkListType: how-to-guide
|
- linkListType: how-to-guide
|
||||||
links:
|
links:
|
||||||
|
|||||||
@ -5,9 +5,9 @@ description: Appendix on Microsoft Connected Cache (MCC) for Enterprise and Educ
|
|||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
author: amymzhou
|
author: amymzhou
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Appendix
|
# Appendix
|
||||||
|
|||||||
@ -4,10 +4,10 @@ manager: dougeby
|
|||||||
description: How to deploy Microsoft Connected Cache (MCC) for Enterprise and Education cache node
|
description: How to deploy Microsoft Connected Cache (MCC) for Enterprise and Education cache node
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
author: amymzhou
|
author: amymzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Deploying your cache node
|
# Deploying your cache node
|
||||||
|
|||||||
@ -4,10 +4,10 @@ manager: dougeby
|
|||||||
description: Overview of requirements for Microsoft Connected Cache (MCC) for Enterprise and Education.
|
description: Overview of requirements for Microsoft Connected Cache (MCC) for Enterprise and Education.
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
author: amymzhou
|
author: amymzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Requirements of Microsoft Connected Cache for Enterprise and Education (early preview)
|
# Requirements of Microsoft Connected Cache for Enterprise and Education (early preview)
|
||||||
|
|||||||
@ -4,10 +4,10 @@ manager: dougeby
|
|||||||
description: Details on updating or uninstalling Microsoft Connected Cache (MCC) for Enterprise and Education.
|
description: Details on updating or uninstalling Microsoft Connected Cache (MCC) for Enterprise and Education.
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
author: amymzhou
|
author: amymzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
# Update or uninstall Microsoft Connected Cache for Enterprise and Education
|
# Update or uninstall Microsoft Connected Cache for Enterprise and Education
|
||||||
|
|
||||||
|
|||||||
@ -2,15 +2,12 @@
|
|||||||
title: Cache node configuration
|
title: Cache node configuration
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
description: Configuring a cache node on Azure portal
|
description: Configuring a cache node on Azure portal
|
||||||
keywords: updates, downloads, network, bandwidth
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: deploy
|
|
||||||
audience: itpro
|
|
||||||
author: amyzhou
|
author: amyzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Cache node configuration
|
# Cache node configuration
|
||||||
|
|||||||
@ -2,15 +2,12 @@
|
|||||||
title: Create, provision, and deploy the cache node in Azure portal
|
title: Create, provision, and deploy the cache node in Azure portal
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
description: Instructions for creating, provisioning, and deploying Microsoft Connected Cache for ISP on Azure portal
|
description: Instructions for creating, provisioning, and deploying Microsoft Connected Cache for ISP on Azure portal
|
||||||
keywords: updates, downloads, network, bandwidth
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: deploy
|
|
||||||
audience: itpro
|
|
||||||
author: nidos
|
author: nidos
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: nidos
|
ms.author: nidos
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Create, Configure, provision, and deploy the cache node in Azure portal
|
# Create, Configure, provision, and deploy the cache node in Azure portal
|
||||||
|
|||||||
@ -2,23 +2,19 @@
|
|||||||
metadata:
|
metadata:
|
||||||
title: Microsoft Connected Cache Frequently Asked Questions
|
title: Microsoft Connected Cache Frequently Asked Questions
|
||||||
description: The following article is a list of frequently asked questions for Microsoft Connected Cache.
|
description: The following article is a list of frequently asked questions for Microsoft Connected Cache.
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: amymzhou
|
author: amymzhou
|
||||||
ms.author: amymzhou
|
ms.author: amymzhou
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- M365-security-compliance
|
|
||||||
- highpri
|
- highpri
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 09/30/2022
|
ms.date: 09/30/2022
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
|
ms.technology: itpro-updates
|
||||||
title: Microsoft Connected Cache Frequently Asked Questions
|
title: Microsoft Connected Cache Frequently Asked Questions
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to**
|
**Applies to**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
|
||||||
|
|
||||||
sections:
|
sections:
|
||||||
- name: Ignored
|
- name: Ignored
|
||||||
@ -32,12 +28,18 @@ sections:
|
|||||||
- question: What are the prerequisites and hardware requirements?
|
- question: What are the prerequisites and hardware requirements?
|
||||||
answer: |
|
answer: |
|
||||||
- Azure subscription
|
- Azure subscription
|
||||||
- Hardware to host Microsoft Connected Cache:
|
- Hardware to host Microsoft Connected Cache
|
||||||
|
- Ubuntu 20.04 LTS on a physical server or VM of your choice.
|
||||||
|
|
||||||
|
> [!NOTE]
|
||||||
|
> The Microsoft Connected Cache is deployed and managed using Azure IoT Edge and Ubuntu 20.04 is an [Azure IoT Edge Tier 1 operating system](/azure/iot-edge/support?view=iotedge-2020-11#tier-1). Additionally, the Microsoft Connected Cache module is optimized for Ubuntu 20.04 LTS.
|
||||||
|
|
||||||
|
The following are recommended hardware configurations:
|
||||||
|
|
||||||
<!--Using include file, mcc-prerequisites.md, for shared content on DO monitoring-->
|
<!--Using include file, mcc-prerequisites.md, for shared content on DO monitoring-->
|
||||||
[!INCLUDE [Microsoft Connected Cache Prerequisites](includes/mcc-prerequisites.md)]
|
[!INCLUDE [Microsoft Connected Cache Prerequisites](includes/mcc-prerequisites.md)]
|
||||||
|
|
||||||
We have one customer who is able to achieve 40-Gbps egress rate using the following hardware specification:
|
We have one customer who is able to achieve mid-30s Gbps egress rate using the following hardware specification:
|
||||||
- Dell PowerEdge R330
|
- Dell PowerEdge R330
|
||||||
- 2 x Intel(R) Xeon(R) CPU E5-2630 v3 @ 2.40 GHz, total 32 core
|
- 2 x Intel(R) Xeon(R) CPU E5-2630 v3 @ 2.40 GHz, total 32 core
|
||||||
- 48 GB, Micron Technology 18ASF1G72PDZ-2G1A1, Speed: 2133 MT/s
|
- 48 GB, Micron Technology 18ASF1G72PDZ-2G1A1, Speed: 2133 MT/s
|
||||||
|
|||||||
@ -2,15 +2,14 @@
|
|||||||
title: Operator sign up and service onboarding
|
title: Operator sign up and service onboarding
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
description: Service onboarding for Microsoft Connected Cache for ISP
|
description: Service onboarding for Microsoft Connected Cache for ISP
|
||||||
keywords: updates, downloads, network, bandwidth
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: deploy
|
ms.mktglfcycl: deploy
|
||||||
audience: itpro
|
audience: itpro
|
||||||
author: nidos
|
author: nidos
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: nidos
|
ms.author: nidos
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Operator sign up and service onboarding for Microsoft Connected Cache
|
# Operator sign up and service onboarding for Microsoft Connected Cache
|
||||||
|
|||||||
@ -2,14 +2,13 @@
|
|||||||
title: Support and troubleshooting
|
title: Support and troubleshooting
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
description: Troubleshooting issues for Microsoft Connected Cache for ISP
|
description: Troubleshooting issues for Microsoft Connected Cache for ISP
|
||||||
keywords: updates, downloads, network, bandwidth
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
audience: itpro
|
audience: itpro
|
||||||
author: nidos
|
author: nidos
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: nidos
|
ms.author: nidos
|
||||||
ms.topic: reference
|
ms.topic: reference
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Support and troubleshooting
|
# Support and troubleshooting
|
||||||
|
|||||||
@ -2,15 +2,14 @@
|
|||||||
title: Update or uninstall your cache node
|
title: Update or uninstall your cache node
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
description: How to update or uninstall your cache node
|
description: How to update or uninstall your cache node
|
||||||
keywords: updates, downloads, network, bandwidth
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: deploy
|
ms.mktglfcycl: deploy
|
||||||
audience: itpro
|
audience: itpro
|
||||||
author: amyzhou
|
author: amyzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Update or uninstall your cache node
|
# Update or uninstall your cache node
|
||||||
|
|||||||
@ -4,13 +4,12 @@ manager: aaroncz
|
|||||||
description: How to verify the functionality of a cache node
|
description: How to verify the functionality of a cache node
|
||||||
keywords: updates, downloads, network, bandwidth
|
keywords: updates, downloads, network, bandwidth
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: deploy
|
|
||||||
audience: itpro
|
audience: itpro
|
||||||
author: amyzhou
|
author: amyzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
# Verify cache node functionality and monitor health and performance
|
# Verify cache node functionality and monitor health and performance
|
||||||
|
|||||||
@ -2,14 +2,11 @@
|
|||||||
title: Enhancing VM performance
|
title: Enhancing VM performance
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
description: How to enhance performance on a virtual machine used with Microsoft Connected Cache for ISPs
|
description: How to enhance performance on a virtual machine used with Microsoft Connected Cache for ISPs
|
||||||
keywords: updates, downloads, network, bandwidth
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: deploy
|
|
||||||
audience: itpro
|
|
||||||
author: amyzhou
|
author: amyzhou
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: amyzhou
|
ms.author: amyzhou
|
||||||
ms.topic: reference
|
ms.topic: reference
|
||||||
|
ms.technology: itpro-updates
|
||||||
ms.date: 12/31/2017
|
ms.date: 12/31/2017
|
||||||
---
|
---
|
||||||
|
|
||||||
|
|||||||
@ -2,28 +2,20 @@
|
|||||||
metadata:
|
metadata:
|
||||||
title: Delivery Optimization Frequently Asked Questions
|
title: Delivery Optimization Frequently Asked Questions
|
||||||
description: The following is a list of frequently asked questions for Delivery Optimization.
|
description: The following is a list of frequently asked questions for Delivery Optimization.
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.reviewer: aaroncz
|
ms.reviewer: aaroncz
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: carmenf
|
author: carmenf
|
||||||
ms.author: carmenf
|
ms.author: carmenf
|
||||||
manager: dougeby
|
manager: dougeby
|
||||||
audience: ITPro
|
ms.technology: itpro-updates
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- M365-security-compliance
|
|
||||||
- highpri
|
- highpri
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 08/04/2022
|
ms.date: 08/04/2022
|
||||||
ms.custom: seo-marvel-apr2020
|
|
||||||
title: Delivery Optimization Frequently Asked Questions
|
title: Delivery Optimization Frequently Asked Questions
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to**
|
**Applies to**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
|
||||||
|
|
||||||
|
|
||||||
sections:
|
sections:
|
||||||
|
|||||||
@ -64,7 +64,7 @@ In MDM, the same settings are under **.Vendor/MSFT/Policy/Config/DeliveryOptimiz
|
|||||||
| [Delay foreground download cache server fallback (in secs)](#delay-foreground-download-cache-server-fallback-in-secs) | DelayCacheServerFallbackForeground | 1903 |
|
| [Delay foreground download cache server fallback (in secs)](#delay-foreground-download-cache-server-fallback-in-secs) | DelayCacheServerFallbackForeground | 1903 |
|
||||||
| [Delay background download cache server fallback (in secs)](#delay-background-download-cache-server-fallback-in-secs) | DelayCacheServerFallbackBackground | 1903 |
|
| [Delay background download cache server fallback (in secs)](#delay-background-download-cache-server-fallback-in-secs) | DelayCacheServerFallbackBackground | 1903 |
|
||||||
| [Cache Server Hostname](#cache-server-hostname) | DOCacheHost | 1809 |
|
| [Cache Server Hostname](#cache-server-hostname) | DOCacheHost | 1809 |
|
||||||
| [Cache Server Hostname Source](#cache-server-hostname-source) | DOCacheHostSource | 1809 |
|
| [Cache Server Hostname Source](#cache-server-hostname-source) | DOCacheHostSource | 2004 |
|
||||||
| [Maximum Foreground Download Bandwidth (in KB/s)](#maximum-background-download-bandwidth-in-kbs) | DOMaxForegroundDownloadBandwidth | 2004 |
|
| [Maximum Foreground Download Bandwidth (in KB/s)](#maximum-background-download-bandwidth-in-kbs) | DOMaxForegroundDownloadBandwidth | 2004 |
|
||||||
| [Maximum Background Download Bandwidth (in KB/s)](#maximum-background-download-bandwidth-in-kbs) | DOMaxBackgroundDownloadBandwidth | 2004 |
|
| [Maximum Background Download Bandwidth (in KB/s)](#maximum-background-download-bandwidth-in-kbs) | DOMaxBackgroundDownloadBandwidth | 2004 |
|
||||||
|
|
||||||
@ -146,7 +146,7 @@ Starting in Windows 10, version 1803, set this policy to restrict peer selection
|
|||||||
- 4 = DNS Suffix
|
- 4 = DNS Suffix
|
||||||
- 5 = Starting with Windows 10, version 1903, you can use the Azure Active Directory (AAD) Tenant ID as a means to define groups. To do this set the value for DOGroupIdSource to its new maximum value of 5.
|
- 5 = Starting with Windows 10, version 1903, you can use the Azure Active Directory (AAD) Tenant ID as a means to define groups. To do this set the value for DOGroupIdSource to its new maximum value of 5.
|
||||||
|
|
||||||
When set, the Group ID is assigned automatically from the selected source. If you set this policy, the GroupID policy will be ignored. The option set in this policy only applies to Group (2) download mode. If Group (2) isn't set as Download mode, this policy will be ignored. If you set the value to anything other than 0-5, the policy is ignored.
|
When set, the Group ID is assigned automatically from the selected source. If you set this policy, the GroupID policy will be ignored. The default behavior, when neither the GroupID or GroupIDSource policies are set, is to determine the Group ID using AD Site (1), Authenticated domain SID (2) or AAD Tenant ID (5), in that order. If GroupIDSource is set to either DHCP Option ID (3) or DNS Suffix (4) and those methods fail, the default behavior is used instead. The option set in this policy only applies to Group (2) download mode. If Group (2) isn't set as Download mode, this policy will be ignored. If you set the value to anything other than 0-5, the policy is ignored.
|
||||||
|
|
||||||
### Minimum RAM (inclusive) allowed to use Peer Caching
|
### Minimum RAM (inclusive) allowed to use Peer Caching
|
||||||
|
|
||||||
|
|||||||
@ -1,16 +1,15 @@
|
|||||||
---
|
---
|
||||||
title: Set up Delivery Optimization
|
title: Set up Delivery Optimization
|
||||||
ms.reviewer:
|
|
||||||
manager: dougeby
|
|
||||||
description: In this article, learn how to set up Delivery Optimization.
|
description: In this article, learn how to set up Delivery Optimization.
|
||||||
ms.prod: windows-client
|
|
||||||
author: carmenf
|
author: carmenf
|
||||||
ms.localizationpriority: medium
|
|
||||||
ms.author: carmenf
|
ms.author: carmenf
|
||||||
ms.topic: article
|
ms.reviewer: mstewart
|
||||||
ms.custom: seo-marvel-apr2020
|
manager: aaroncz
|
||||||
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-updates
|
ms.technology: itpro-updates
|
||||||
ms.date: 12/31/2017
|
ms.localizationpriority: medium
|
||||||
|
ms.topic: how-to
|
||||||
|
ms.date: 12/19/2022
|
||||||
---
|
---
|
||||||
|
|
||||||
# Set up Delivery Optimization for Windows
|
# Set up Delivery Optimization for Windows
|
||||||
@ -28,7 +27,7 @@ You can use Group Policy or an MDM solution like Intune to configure Delivery Op
|
|||||||
|
|
||||||
You will find the Delivery Optimization settings in Group Policy under **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization**.
|
You will find the Delivery Optimization settings in Group Policy under **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization**.
|
||||||
|
|
||||||
Starting with Microsoft Intune version 1902, you can set many Delivery Optimization policies as a profile, which you can then apply to groups of devices. For more information, see [Delivery Optimization settings in Microsoft Intune](/intune/delivery-optimization-windows).
|
Starting with Microsoft Intune version 1902, you can set many Delivery Optimization policies as a profile, which you can then apply to groups of devices. For more information, see [Delivery Optimization settings in Microsoft Intune](/mem/intune/configuration/delivery-optimization-windows).
|
||||||
|
|
||||||
**Starting with Windows 10, version 1903**, you can use the Azure Active Directory (Azure AD) Tenant ID as a means to define groups. To do this set the value for DOGroupIdSource to its new maximum value of 5.
|
**Starting with Windows 10, version 1903**, you can use the Azure Active Directory (Azure AD) Tenant ID as a means to define groups. To do this set the value for DOGroupIdSource to its new maximum value of 5.
|
||||||
|
|
||||||
@ -68,7 +67,7 @@ For this scenario, grouping devices by domain allows devices to be included in p
|
|||||||
|
|
||||||
To do this in Group Policy go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Download mode** to **2**.
|
To do this in Group Policy go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Download mode** to **2**.
|
||||||
|
|
||||||
To do this with MDM, go to **.Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set DODownloadMode to 1 or 2.
|
To do this with MDM, go to **./Device/Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set [DODownloadMode](/windows/client-management/mdm/policy-csp-deliveryoptimization#dodownloadmode) to 1 or 2.
|
||||||
|
|
||||||
### Hub and spoke topology with boundary groups
|
### Hub and spoke topology with boundary groups
|
||||||
|
|
||||||
@ -76,10 +75,10 @@ The default download mode setting is **1**; this means all devices breaking out
|
|||||||
|
|
||||||
To do this in Group Policy go to ****Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Download mode** to **2**.
|
To do this in Group Policy go to ****Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Download mode** to **2**.
|
||||||
|
|
||||||
To do this with MDM, go to **.Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set **DODownloadMode** to **2**.
|
To do this with MDM, go to **./Device/Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set [DODownloadMode](/windows/client-management/mdm/policy-csp-deliveryoptimization#dodownloadmode) to **2**.
|
||||||
|
|
||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> For more about using Delivery Optimization with Configuration Manager boundary groups, see [Delivery Optmization](/mem/configmgr/core/plan-design/hierarchy/fundamental-concepts-for-content-management#delivery-optimization).
|
> For more information about using Delivery Optimization with Configuration Manager boundary groups, see [Delivery Optmization](/mem/configmgr/core/plan-design/hierarchy/fundamental-concepts-for-content-management#delivery-optimization).
|
||||||
|
|
||||||
### Large number of mobile devices
|
### Large number of mobile devices
|
||||||
|
|
||||||
@ -87,17 +86,15 @@ If you have a mobile workforce with a great many mobile devices, set Delivery Op
|
|||||||
|
|
||||||
To do this in Group Policy, go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Allow uploads while the device is on battery while under set Battery level** to 60.
|
To do this in Group Policy, go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Allow uploads while the device is on battery while under set Battery level** to 60.
|
||||||
|
|
||||||
To do this with MDM, go to **.Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set **DOMinBatteryPercentageAllowedToUpload** to 60.
|
To do this with MDM, go to **./Device/Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set [DOMinBatteryPercentageAllowedToUpload](/windows/client-management/mdm/policy-csp-deliveryoptimization#dominbatterypercentageallowedtoupload) to 60.
|
||||||
|
|
||||||
### Plentiful free space and large numbers of devices
|
### Plentiful free space and large numbers of devices
|
||||||
|
|
||||||
Many devices now come with large internal drives. You can set Delivery Optimization to take better advantage of this space (especially if you have large numbers of devices) by changing the minimum file size to cache. If you have more than 30 devices in your local network or group, change it from the default 50 MB to 10 MB. If you have more than 100 devices (and are running Windows 10, version 1803 or later), set this value to 1 MB.
|
Many devices now come with large internal drives. You can set Delivery Optimization to take better advantage of this space (especially if you have large numbers of devices) by changing the minimum file size to cache. If you have more than 30 devices in your local network or group, change it from the default 50 MB to 10 MB. If you have more than 100 devices (and are running Windows 10, version 1803 or later), set this value to 1 MB.
|
||||||
|
|
||||||
[//]: # (default of 50 aimed at consumer)
|
|
||||||
|
|
||||||
To do this in Group Policy, go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Minimum Peer Caching Content File Size** to 10 (if you have more than 30 devices) or 1 (if you have more than 100 devices).
|
To do this in Group Policy, go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Minimum Peer Caching Content File Size** to 10 (if you have more than 30 devices) or 1 (if you have more than 100 devices).
|
||||||
|
|
||||||
To do this with MDM, go to **.Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set **DOMinFileSizeToCache** to 100 (if you have more than 30 devices) or 1 (if you have more than 100 devices).
|
To do this with MDM, go to **./Device/Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set [DOMinFileSizeToCache](/windows/client-management/mdm/policy-csp-deliveryoptimization#dominfilesizetocache) to 100 (if you have more than 30 devices) or 1 (if you have more than 100 devices).
|
||||||
|
|
||||||
### Lab scenario
|
### Lab scenario
|
||||||
|
|
||||||
@ -105,7 +102,7 @@ In a lab situation, you typically have a large number of devices that are plugge
|
|||||||
|
|
||||||
To do this in Group Policy, go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Max Cache Age** to **604800** (7 days) or more (up to 30 days).
|
To do this in Group Policy, go to **Computer Configuration\Administrative Templates\Windows Components\Delivery Optimization** and set **Max Cache Age** to **604800** (7 days) or more (up to 30 days).
|
||||||
|
|
||||||
To do this with MDM, go to **.Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set DOMaxCacheAge to 7 or more (up to 30 days).
|
To do this with MDM, go to **./Device/Vendor/MSFT/Policy/Config/DeliveryOptimization/** and set [DOMaxCacheAge](/windows/client-management/mdm/policy-csp-deliveryoptimization#domaxcacheage) to 7 or more (up to 30 days).
|
||||||
|
|
||||||
|
|
||||||
<!--Using include file, waas-delivery-optimization-monitor.md, for shared content on DO monitoring-->
|
<!--Using include file, waas-delivery-optimization-monitor.md, for shared content on DO monitoring-->
|
||||||
|
|||||||
@ -21,6 +21,7 @@ ms.date: 12/31/2017
|
|||||||
|
|
||||||
- Windows 10
|
- Windows 10
|
||||||
- Windows 11
|
- Windows 11
|
||||||
|
- Windows Server
|
||||||
|
|
||||||
## What is a servicing stack update?
|
## What is a servicing stack update?
|
||||||
Servicing stack updates provide fixes to the servicing stack, the component that installs Windows updates. Additionally, it contains the "component-based servicing stack" (CBS), which is a key underlying component for several elements of Windows deployment, such as DISM, SFC, changing Windows features or roles, and repairing components. The CBS is a small component that typically does not have updates released every month.
|
Servicing stack updates provide fixes to the servicing stack, the component that installs Windows updates. Additionally, it contains the "component-based servicing stack" (CBS), which is a key underlying component for several elements of Windows deployment, such as DISM, SFC, changing Windows features or roles, and repairing components. The CBS is a small component that typically does not have updates released every month.
|
||||||
@ -61,3 +62,5 @@ Typically, the improvements are reliability and performance improvements that do
|
|||||||
## Simplifying on-premises deployment of servicing stack updates
|
## Simplifying on-premises deployment of servicing stack updates
|
||||||
|
|
||||||
With the Windows Update experience, servicing stack updates and cumulative updates are deployed together to the device. The update stack automatically orchestrates the installation, so both are applied correctly. Starting in February 2021, the cumulative update will include the latest servicing stack updates, to provide a single cumulative update payload to both Windows Server Update Services (WSUS) and Microsoft Catalog. If you use an endpoint management tool backed by WSUS, such as Configuration Manager, you will only have to select and deploy the monthly cumulative update. The latest servicing stack updates will automatically be applied correctly. Release notes and file information for cumulative updates, including those related to the servicing stack, will be in a single KB article. The combined monthly cumulative update will be available on Windows 10, version 2004 and later starting with the 2021 2C release, KB4601382.
|
With the Windows Update experience, servicing stack updates and cumulative updates are deployed together to the device. The update stack automatically orchestrates the installation, so both are applied correctly. Starting in February 2021, the cumulative update will include the latest servicing stack updates, to provide a single cumulative update payload to both Windows Server Update Services (WSUS) and Microsoft Catalog. If you use an endpoint management tool backed by WSUS, such as Configuration Manager, you will only have to select and deploy the monthly cumulative update. The latest servicing stack updates will automatically be applied correctly. Release notes and file information for cumulative updates, including those related to the servicing stack, will be in a single KB article. The combined monthly cumulative update will be available on Windows 10, version 2004 and later starting with the 2021 2C release, KB4601382.
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
@ -8,7 +8,7 @@ author: mestew
|
|||||||
ms.author: mstewart
|
ms.author: mstewart
|
||||||
ms.localizationpriority: medium
|
ms.localizationpriority: medium
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
ms.date: 12/05/2022
|
ms.date: 12/22/2022
|
||||||
ms.technology: itpro-updates
|
ms.technology: itpro-updates
|
||||||
---
|
---
|
||||||
|
|
||||||
@ -27,7 +27,7 @@ This article is targeted at configuring devices enrolled to [Microsoft Intune](/
|
|||||||
|
|
||||||
## Create a configuration profile
|
## Create a configuration profile
|
||||||
|
|
||||||
Create a configuration profile that will set the required policies for Windows Update for Business reports. There are two profile types that can be used to create a configuration profile for Windows Update for Business reports:
|
Create a configuration profile that will set the required policies for Windows Update for Business reports. There are two profile types that can be used to create a configuration profile for Windows Update for Business reports (select one):
|
||||||
- The [settings catalog](#settings-catalog)
|
- The [settings catalog](#settings-catalog)
|
||||||
- [Template](#custom-oma-uri-based-profile) for a custom OMA URI-based profile
|
- [Template](#custom-oma-uri-based-profile) for a custom OMA URI-based profile
|
||||||
|
|
||||||
@ -45,9 +45,12 @@ Create a configuration profile that will set the required policies for Windows U
|
|||||||
- **Value**: Basic (*Basic is the minimum value, but it can be safely set to a higher value*)
|
- **Value**: Basic (*Basic is the minimum value, but it can be safely set to a higher value*)
|
||||||
- **Setting**: Allow Update Compliance Processing
|
- **Setting**: Allow Update Compliance Processing
|
||||||
- **Value**: Enabled
|
- **Value**: Enabled
|
||||||
|
1. Recommended settings, but not required:
|
||||||
|
- **Setting**: Configure Telemetry Opt In Settings Ux
|
||||||
|
- **Value**: Disabled (*By turning this setting on you are disabling the ability for a user to potentially override the diagnostic data level of devices such that data won't be available for those devices in Windows Update for Business reports*)
|
||||||
- **Setting**: Configure Telemetry Opt In Change Notification
|
- **Setting**: Configure Telemetry Opt In Change Notification
|
||||||
1. (*Recommended, but not required*) Allow device name to be sent in Windows Diagnostic Data. If this policy is disabled, the device name won't be sent and won't be visible in Windows Update for Business reports:
|
- **Value**: Disabled (*By turning this setting on you are disabling notifications of diagnostic data changes*)
|
||||||
- **Setting**: Allow device name to be sent in Windows diagnostic data
|
- **Setting**: Allow device name to be sent in Windows diagnostic data (*If this policy is disabled, the device name won't be sent and won't be visible in Windows Update for Business reports*)
|
||||||
- **Value**: Allowed
|
- **Value**: Allowed
|
||||||
|
|
||||||
1. Continue through the next set of tabs **Scope tags**, **Assignments**, and **Applicability Rules** to assign the configuration profile to devices you wish to enroll.
|
1. Continue through the next set of tabs **Scope tags**, **Assignments**, and **Applicability Rules** to assign the configuration profile to devices you wish to enroll.
|
||||||
|
|||||||
@ -203,6 +203,7 @@ The following table indicates which command-line options aren't compatible with
|
|||||||
|**/encrypt**|Required*|X|X||
|
|**/encrypt**|Required*|X|X||
|
||||||
|**/keyfile**|N/A||X||
|
|**/keyfile**|N/A||X||
|
||||||
|**/l**|||||
|
|**/l**|||||
|
||||||
|
|**/listfiles**|||X||
|
||||||
|**/progress**|||X||
|
|**/progress**|||X||
|
||||||
|**/r**|||X||
|
|**/r**|||X||
|
||||||
|**/w**|||X||
|
|**/w**|||X||
|
||||||
|
|||||||
@ -40,7 +40,7 @@ This article covers the following information:
|
|||||||
For more information on how to deploy Enterprise licenses, see [Deploy Windows Enterprise licenses](deploy-enterprise-licenses.md).
|
For more information on how to deploy Enterprise licenses, see [Deploy Windows Enterprise licenses](deploy-enterprise-licenses.md).
|
||||||
|
|
||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> Organizations that use the [Subscription Activation](/windows/deployment/windows-10-subscription-activation) feature to enable users to upgrade from one version of Windows to another might want to exclude the Universal Store Service APIs and Web Application, AppID 45a330b1-b1ec-4cc1-9161-9f03992aa49f, from their device compliance policy.
|
> Organizations that use the Subscription Activation feature to enable users to upgrade from one version of Windows to another might want to exclude the Universal Store Service APIs and Web Application, AppID 45a330b1-b1ec-4cc1-9161-9f03992aa49f, from their device compliance policy.
|
||||||
|
|
||||||
## Subscription activation for Enterprise
|
## Subscription activation for Enterprise
|
||||||
|
|
||||||
|
|||||||
@ -13,6 +13,7 @@ metadata:
|
|||||||
ms.date: 05/30/2022 #Required; mm/dd/yyyy format.
|
ms.date: 05/30/2022 #Required; mm/dd/yyyy format.
|
||||||
ms.custom: intro-hub-or-landing
|
ms.custom: intro-hub-or-landing
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
|
ms.technology: itpro-updates
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- highpri
|
- highpri
|
||||||
|
|
||||||
|
|||||||
@ -52,7 +52,24 @@ Windows Autopatch configures these policies differently across update rings to g
|
|||||||
|
|
||||||
:::image type="content" source="../media/release-process-timeline.png" alt-text="Release process timeline" lightbox="../media/release-process-timeline.png":::
|
:::image type="content" source="../media/release-process-timeline.png" alt-text="Release process timeline" lightbox="../media/release-process-timeline.png":::
|
||||||
|
|
||||||
## Expedited releases
|
## Release management
|
||||||
|
|
||||||
|
In the Release management blade, you can:
|
||||||
|
|
||||||
|
- Track the [Windows quality update schedule](#release-schedule) for devices in the [four deployment rings](windows-autopatch-update-management.md#windows-autopatch-deployment-rings).
|
||||||
|
- [Turn off expedited Windows quality updates](#turn-off-service-driven-expedited-quality-update-releases).
|
||||||
|
- Review release announcements and knowledge based articles for regular and [Out of Band (OOB) Windows quality updates](#out-of-band-releases).
|
||||||
|
|
||||||
|
### Release schedule
|
||||||
|
|
||||||
|
For each [deployment ring](windows-autopatch-update-management.md#windows-autopatch-deployment-rings), the **Release schedule** tab contains:
|
||||||
|
|
||||||
|
- The status of the update. Releases will appear as **Active**. The update schedule is based on the values of the [Windows 10 Update Ring policies](/mem/intune/protect/windows-update-for-business-configure), which have been configured on your behalf.
|
||||||
|
- The date the update is available.
|
||||||
|
- The target completion date of the update.
|
||||||
|
- In the **Release schedule** tab, you can either [**Pause** and/or **Resume**](#pausing-and-resuming-a-release) a Windows quality update release.
|
||||||
|
|
||||||
|
### Expedited releases
|
||||||
|
|
||||||
Threat and vulnerability information about a new revision of Windows becomes available on the second Tuesday of each month. Windows Autopatch assesses that information shortly afterwards. If the service determines that it's critical to security, it may be expedited. The quality update is also evaluated on an ongoing basis throughout the release and Windows Autopatch may choose to expedite at any time during the release.
|
Threat and vulnerability information about a new revision of Windows becomes available on the second Tuesday of each month. Windows Autopatch assesses that information shortly afterwards. If the service determines that it's critical to security, it may be expedited. The quality update is also evaluated on an ongoing basis throughout the release and Windows Autopatch may choose to expedite at any time during the release.
|
||||||
|
|
||||||
@ -63,10 +80,12 @@ When running an expedited release, the regular goal of 95% of devices in 21 days
|
|||||||
| Standard release | Test<p>First<p>Fast<p>Broad | 0<p>1<p>6<p>9 | 0<p>2<p>2<p>5 | 0<p>2<p>2<p>2 |
|
| Standard release | Test<p>First<p>Fast<p>Broad | 0<p>1<p>6<p>9 | 0<p>2<p>2<p>5 | 0<p>2<p>2<p>2 |
|
||||||
| Expedited release | All devices | 0 | 1 | 1 |
|
| Expedited release | All devices | 0 | 1 | 1 |
|
||||||
|
|
||||||
### Turn off service-driven expedited quality update releases
|
#### Turn off service-driven expedited quality update releases
|
||||||
|
|
||||||
Windows Autopatch provides the option to turn off of service-driven expedited quality updates.
|
Windows Autopatch provides the option to turn off of service-driven expedited quality updates.
|
||||||
|
|
||||||
|
By default, the service expedites quality updates as needed. For those organizations seeking greater control, you can disable expedited quality updates for Microsoft Managed Desktop-enrolled devices using Microsoft Intune.
|
||||||
|
|
||||||
**To turn off service-driven expedited quality updates:**
|
**To turn off service-driven expedited quality updates:**
|
||||||
|
|
||||||
1. Go to **[Microsoft Endpoint Manager portal](https://go.microsoft.com/fwlink/?linkid=2109431)** > **Devices**.
|
1. Go to **[Microsoft Endpoint Manager portal](https://go.microsoft.com/fwlink/?linkid=2109431)** > **Devices**.
|
||||||
@ -75,9 +94,9 @@ Windows Autopatch provides the option to turn off of service-driven expedited qu
|
|||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> Windows Autopatch doesn't allow customers to request expedited releases.
|
> Windows Autopatch doesn't allow customers to request expedited releases.
|
||||||
|
|
||||||
## Out of Band releases
|
### Out of Band releases
|
||||||
|
|
||||||
Windows Autopatch schedules and deploys required Out of Band (OOB) updates released outside of the normal schedule. You can view the deployed OOB quality updates in the **Release Management** blade in the **[Microsoft Endpoint Manager portal](https://go.microsoft.com/fwlink/?linkid=2109431)**.
|
Windows Autopatch schedules and deploys required Out of Band (OOB) updates released outside of the normal schedule.
|
||||||
|
|
||||||
**To view deployed Out of Band quality updates:**
|
**To view deployed Out of Band quality updates:**
|
||||||
|
|
||||||
@ -87,13 +106,18 @@ Windows Autopatch schedules and deploys required Out of Band (OOB) updates relea
|
|||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> Announcements will be **removed** from the Release announcements tab when the next quality update is released. Further, if quality updates are paused for a deployment ring, the OOB updates will also be paused.
|
> Announcements will be **removed** from the Release announcements tab when the next quality update is released. Further, if quality updates are paused for a deployment ring, the OOB updates will also be paused.
|
||||||
|
|
||||||
## Pausing and resuming a release
|
### Pausing and resuming a release
|
||||||
|
|
||||||
If Windows Autopatch detects a [significant issue with a release](../operate/windows-autopatch-wqu-signals.md), we may decide to pause that release.
|
If Windows Autopatch detects a [significant issue with a release](../operate/windows-autopatch-wqu-signals.md), we may decide to pause that release.
|
||||||
|
|
||||||
If we pause the release, a policy will be deployed which prevents devices from updating while the issue is investigated. Once the issue is resolved, the release will be resumed.
|
In the [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431) > **Release management** > in the **Release schedule** tab, you can pause or resume a Windows quality update.
|
||||||
|
|
||||||
You can pause or resume a Windows quality update from the **Release management** tab in the [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
There are two statuses associated with paused quality updates, **Service Paused** and **Customer Paused**.
|
||||||
|
|
||||||
|
| Status | Description |
|
||||||
|
| ----- | ------ |
|
||||||
|
| Service Paused | If the Microsoft Managed Desktop service has paused an update, the release will have the **Service Paused** status. You must [submit a support request](windows-autopatch-support-request.md) to resume the update. |
|
||||||
|
| Customer Paused | If you've paused an update, the release will have the **Customer Paused** status. The Microsoft Managed Desktop service can't overwrite a customer-initiated pause. You must select **Resume** to resume the update. |
|
||||||
|
|
||||||
## Incidents and outages
|
## Incidents and outages
|
||||||
|
|
||||||
|
|||||||
@ -11,6 +11,7 @@ metadata:
|
|||||||
author: tiaraquan
|
author: tiaraquan
|
||||||
ms.author: tiaraquan
|
ms.author: tiaraquan
|
||||||
ms.reviwer: hathind
|
ms.reviwer: hathind
|
||||||
|
ms.technology: itpro-updates
|
||||||
title: Frequently Asked Questions about Windows Autopatch
|
title: Frequently Asked Questions about Windows Autopatch
|
||||||
summary: This article answers frequently asked questions about Windows Autopatch.
|
summary: This article answers frequently asked questions about Windows Autopatch.
|
||||||
sections:
|
sections:
|
||||||
|
|||||||
@ -306,10 +306,16 @@
|
|||||||
items:
|
items:
|
||||||
- name: Overview
|
- name: Overview
|
||||||
href: identity.md
|
href: identity.md
|
||||||
- name: Windows Hello for Business
|
|
||||||
href: identity-protection/hello-for-business/index.yml
|
|
||||||
- name: Windows credential theft mitigation guide
|
- name: Windows credential theft mitigation guide
|
||||||
href: identity-protection/windows-credential-theft-mitigation-guide-abstract.md
|
href: identity-protection/windows-credential-theft-mitigation-guide-abstract.md
|
||||||
|
- name: Passwordless
|
||||||
|
items:
|
||||||
|
- name: Windows Hello for Business
|
||||||
|
href: identity-protection/hello-for-business/index.yml
|
||||||
|
- name: FIDO 2 security keys
|
||||||
|
href: /azure/active-directory/authentication/howto-authentication-passwordless-security-key?context=/windows/security/context/context
|
||||||
|
- name: Local Administrator Password Solution (LAPS)
|
||||||
|
href: /windows-server/identity/laps/laps-overview?context=/windows/security/context/context
|
||||||
- name: Enterprise Certificate Pinning
|
- name: Enterprise Certificate Pinning
|
||||||
href: identity-protection/enterprise-certificate-pinning.md
|
href: identity-protection/enterprise-certificate-pinning.md
|
||||||
- name: Credential Guard
|
- name: Credential Guard
|
||||||
|
|||||||
@ -10,3 +10,9 @@ items:
|
|||||||
- name: Security
|
- name: Security
|
||||||
tocHref: /windows-server/security/credentials-protection-and-management/
|
tocHref: /windows-server/security/credentials-protection-and-management/
|
||||||
topicHref: /windows/security/
|
topicHref: /windows/security/
|
||||||
|
- name: Security
|
||||||
|
tocHref: /windows-server/identity/laps/
|
||||||
|
topicHref: /windows/security/
|
||||||
|
- name: Security
|
||||||
|
tocHref: /azure/active-directory/authentication/
|
||||||
|
topicHref: /windows/security/
|
||||||
|
|||||||
4
windows/security/context/context.yml
Normal file
4
windows/security/context/context.yml
Normal file
@ -0,0 +1,4 @@
|
|||||||
|
### YamlMime: ContextObject
|
||||||
|
brand: windows
|
||||||
|
breadcrumb_path: ../breadcrumb/toc.yml
|
||||||
|
toc_rel: ../toc.yml
|
||||||
@ -11,9 +11,9 @@ appliesto:
|
|||||||
|
|
||||||
# Deploy certificates for remote desktop (RDP) sign-in
|
# Deploy certificates for remote desktop (RDP) sign-in
|
||||||
|
|
||||||
This document describes Windows Hello for Business functionalities or scenarios that apply to:\
|
This document describes Windows Hello for Business functionalities or scenarios that apply to:
|
||||||
- **Deployment type:** [!INCLUDE [hybrid](../../includes/hello-deployment-hybrid.md)]
|
- **Deployment type:** [!INCLUDE [hybrid](../../includes/hello-deployment-hybrid.md)]
|
||||||
- **Trust type:** [!INCLUDE [cloud-kerberos](../../includes/hello-trust-cloud-kerberos.md)],[!INCLUDE [key](../../includes/hello-trust-key.md)]
|
- **Trust type:** [!INCLUDE [cloud-kerberos](../../includes/hello-trust-cloud-kerberos.md)], [!INCLUDE [key](../../includes/hello-trust-key.md)]
|
||||||
- **Join type:** [!INCLUDE [hello-join-aadj](../../includes/hello-join-aad.md)], [!INCLUDE [hello-join-hybrid](../../includes/hello-join-hybrid.md)]
|
- **Join type:** [!INCLUDE [hello-join-aadj](../../includes/hello-join-aad.md)], [!INCLUDE [hello-join-hybrid](../../includes/hello-join-hybrid.md)]
|
||||||
---
|
---
|
||||||
|
|
||||||
|
|||||||
@ -1,7 +1,7 @@
|
|||||||
### YamlMime:FAQ
|
### YamlMime:FAQ
|
||||||
metadata:
|
metadata:
|
||||||
title: Windows Hello for Business Frequently Asked Questions (FAQ)
|
title: Windows Hello for Business Frequently Asked Questions (FAQ)
|
||||||
description: Use these frequently asked questions (FAQ) to learn important details about Windows Hello for Business.
|
description: Use these frequently asked questions (FAQ) to learn important details about Windows Hello for Business.
|
||||||
keywords: identity, PIN, biometric, Hello, passport
|
keywords: identity, PIN, biometric, Hello, passport
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
@ -13,7 +13,6 @@ metadata:
|
|||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.reviewer: prsriva
|
ms.reviewer: prsriva
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- M365-identity-device-management
|
|
||||||
- highpri
|
- highpri
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
localizationpriority: medium
|
localizationpriority: medium
|
||||||
@ -30,16 +29,16 @@ sections:
|
|||||||
|
|
||||||
- question: What is Windows Hello for Business cloud Kerberos trust?
|
- question: What is Windows Hello for Business cloud Kerberos trust?
|
||||||
answer: |
|
answer: |
|
||||||
Windows Hello for Business cloud Kerberos trust is a new trust model that is currently in preview. This trust model will enable Windows Hello for Business deployment using the infrastructure introduced for supporting [security key sign-in on Hybrid Azure AD-joined devices and on-premises resource access on Azure AD Joined devices](/azure/active-directory/authentication/howto-authentication-passwordless-security-key-on-premises). cloud Kerberos trust is the preferred deployment model if you do not need to support certificate authentication scenarios. For more information, see [Hybrid cloud Kerberos trust Deployment (Preview)](/windows/security/identity-protection/hello-for-business/hello-hybrid-cloud-kerberos-trust).
|
Windows Hello for Business *cloud Kerberos trust* is a **trust model** that enables Windows Hello for Business deployment using the infrastructure introduced for supporting [security key sign-in on Hybrid Azure AD-joined devices and on-premises resource access on Azure AD Joined devices](/azure/active-directory/authentication/howto-authentication-passwordless-security-key-on-premises). Cloud Kerberos trust is the preferred deployment model if you do not need to support certificate authentication scenarios. For more information, see [cloud Kerberos trust deployment](/windows/security/identity-protection/hello-for-business/hello-hybrid-cloud-kerberos-trust).
|
||||||
|
|
||||||
|
|
||||||
- question: What about virtual smart cards?
|
- question: What about virtual smart cards?
|
||||||
answer: |
|
answer: |
|
||||||
Windows Hello for Business is the modern, two-factor credential for Windows 10. Microsoft will be deprecating virtual smart cards in the future, but no date is set at this time. Customers using Windows 10 and virtual smart cards should move to Windows Hello for Business. Microsoft will publish the date early to ensure customers have adequate lead time to move to Windows Hello for Business. Microsoft recommends that new Windows 10 deployments use Windows Hello for Business. Virtual smart cards remain supported for Windows 7 and Windows 8.
|
Windows Hello for Business is the modern, two-factor credential for Windows. Microsoft will be deprecating virtual smart cards in the future, but no date is set at this time. Customers using virtual smart cards should move to Windows Hello for Business. Microsoft will publish the date early to ensure customers have adequate lead time to move to Windows Hello for Business. Microsoft recommends that new Windows deployments use Windows Hello for Business.
|
||||||
|
|
||||||
- question: What about convenience PIN?
|
- question: What about convenience PIN?
|
||||||
answer: |
|
answer: |
|
||||||
Microsoft is committed to its vision of a <u>world without passwords.</u> We recognize the *convenience* provided by convenience PIN, but it stills uses a password for authentication. Microsoft recommends that customers using Windows 10 and convenience PINs should move to Windows Hello for Business. New Windows 10 deployments should deploy Windows Hello for Business and not convenience PINs. Microsoft will be deprecating convenience PINs in the future and will publish the date early to ensure customers have adequate lead time to deploy Windows Hello for Business.
|
While *convenience PIN* provides a convenient way to sign in to Windows, it stills uses a password for authentication. Customers using *convenience PINs* should move to **Windows Hello for Business**. New Windows deployments should deploy Windows Hello for Business and not convenience PINs. Microsoft will be deprecating convenience PINs in the future and will publish the date early to ensure customers have adequate lead time to deploy Windows Hello for Business.
|
||||||
|
|
||||||
- question: Can I use Windows Hello for Business key trust and RDP?
|
- question: Can I use Windows Hello for Business key trust and RDP?
|
||||||
answer: |
|
answer: |
|
||||||
@ -57,10 +56,14 @@ sections:
|
|||||||
- question: How many users can enroll for Windows Hello for Business on a single Windows 10 computer?
|
- question: How many users can enroll for Windows Hello for Business on a single Windows 10 computer?
|
||||||
answer: |
|
answer: |
|
||||||
The maximum number of supported enrollments on a single Windows 10 computer is 10. This lets 10 users each enroll their face and up to 10 fingerprints. For devices with more than 10 users, we strongly encourage the use of FIDO2 security keys.
|
The maximum number of supported enrollments on a single Windows 10 computer is 10. This lets 10 users each enroll their face and up to 10 fingerprints. For devices with more than 10 users, we strongly encourage the use of FIDO2 security keys.
|
||||||
|
|
||||||
|
- question: Can I use Windows Hello for Business credentials in private browser mode or "incognito" mode?
|
||||||
|
answer: |
|
||||||
|
Windows Hello for Business credentials need access to device state, which is not available in private browser mode or incognito mode. Hence it can't be used in private browser or Incognito mode.
|
||||||
|
|
||||||
- question: How can a PIN be more secure than a password?
|
- question: How can a PIN be more secure than a password?
|
||||||
answer: |
|
answer: |
|
||||||
When using Windows Hello for Business, the PIN isn't a symmetric key, whereas the password is a symmetric key. With passwords, there's a server that has some representation of the password. With Windows Hello for Business, the PIN is user-provided entropy used to load the private key in the Trusted Platform Module (TPM). The server doesn't have a copy of the PIN. For that matter, the Windows client doesn't have a copy of the current PIN either. The user must provide the entropy, the TPM-protected key, and the TPM that generated that key in order to successfully access the private key.
|
When using Windows Hello for Business, the PIN isn't a symmetric key, whereas the password is a symmetric key. With passwords, there's a server that has some representation of the password. With Windows Hello for Business, the PIN is user-provided entropy used to load the private key in the Trusted Platform Module (TPM). The server doesn't have a copy of the PIN. For that matter, the Windows client doesn't have a copy of the current PIN either. The user must provide the entropy, the TPM-protected key, and the TPM that generated that key in order to successfully access the private key.
|
||||||
The statement "PIN is stronger than Password" is not directed at the strength of the entropy used by the PIN. It's about the difference between providing entropy versus continuing the use of a symmetric key (the password). The TPM has anti-hammering features that thwart brute-force PIN attacks (an attacker's continuous attempt to try all combination of PINs). Some organizations may worry about shoulder surfing. For those organizations, rather than increase the complexity of the PIN, implement the [Multifactor Unlock](feature-multifactor-unlock.md) feature.
|
The statement "PIN is stronger than Password" is not directed at the strength of the entropy used by the PIN. It's about the difference between providing entropy versus continuing the use of a symmetric key (the password). The TPM has anti-hammering features that thwart brute-force PIN attacks (an attacker's continuous attempt to try all combination of PINs). Some organizations may worry about shoulder surfing. For those organizations, rather than increase the complexity of the PIN, implement the [Multifactor Unlock](feature-multifactor-unlock.md) feature.
|
||||||
|
|
||||||
- question: What's a container?
|
- question: What's a container?
|
||||||
@ -91,7 +94,7 @@ sections:
|
|||||||
|
|
||||||
- question: Can I use a convenience PIN with Azure Active Directory?
|
- question: Can I use a convenience PIN with Azure Active Directory?
|
||||||
answer: |
|
answer: |
|
||||||
It's currently possible to set a convenience PIN on Azure Active Directory Joined or Hybrid Active Directory Joined devices. Convenience PIN isn't supported for Azure Active Directory user accounts (synchronized identities included). It's only supported for on-premises Domain Joined users and local account users.
|
It's currently possible to set a convenience PIN on Azure Active Directory Joined or Hybrid Active Directory Joined devices. However, convenience PIN isn't supported for Azure Active Directory user accounts (synchronized identities included). It's only supported for on-premises Domain Joined users and local account users.
|
||||||
|
|
||||||
- question: Can I use an external Windows Hello compatible camera when my computer has a built-in Windows Hello compatible camera?
|
- question: Can I use an external Windows Hello compatible camera when my computer has a built-in Windows Hello compatible camera?
|
||||||
answer: |
|
answer: |
|
||||||
@ -166,7 +169,7 @@ sections:
|
|||||||
|
|
||||||
- question: Where is Windows Hello biometrics data stored?
|
- question: Where is Windows Hello biometrics data stored?
|
||||||
answer: |
|
answer: |
|
||||||
When you enroll in Windows Hello, a representation of your face called an enrollment profile is created more information can be found on [Windows Hello face authentication](/windows-hardware/design/device-experiences/windows-hello-face-authentication). This enrollment profile biometrics data is device specific, is stored locally on the device, and does not leave the device or roam with the user. Some external fingerprint sensors store biometric data on the fingerprint module itself rather than on Windows device. Even in this case, the biometrics data is stored locally on those modules, is device specific, doesn't roam, never leaves the module, and is never sent to Microsoft cloud or external server. For more details, see [Windows Hello biometrics in the enterprise](/windows/security/identity-protection/hello-for-business/hello-biometrics-in-enterprise#where-is-windows-hello-data-stored).
|
When you enroll in Windows Hello, a representation of your face called an enrollment profile is created more information can be found on [Windows Hello face authentication](/windows-hardware/design/device-experiences/windows-hello-face-authentication). This enrollment profile biometrics data is device specific, is stored locally on the device, and does not leave the device or roam with the user. Some external fingerprint sensors store biometric data on the fingerprint module itself rather than on Windows device. Even in this case, the biometrics data is stored locally on those modules, is device specific, doesn't roam, never leaves the module, and is never sent to Microsoft cloud or external server. For more details, see [Windows Hello biometrics in the enterprise](/windows/security/identity-protection/hello-for-business/hello-biometrics-in-enterprise#where-is-windows-hello-data-stored).
|
||||||
|
|
||||||
- question: What is the format used to store Windows Hello biometrics data on the device?
|
- question: What is the format used to store Windows Hello biometrics data on the device?
|
||||||
answer: |
|
answer: |
|
||||||
@ -230,9 +233,9 @@ sections:
|
|||||||
|
|
||||||
- question: How does PIN caching work with Windows Hello for Business?
|
- question: How does PIN caching work with Windows Hello for Business?
|
||||||
answer: |
|
answer: |
|
||||||
Windows Hello for Business provides a PIN caching user experience by using a ticketing system. Rather than caching a PIN, processes cache a ticket they can use to request private key operations. Azure AD and Active Directory sign-in keys are cached under lock. This means the keys remain available for use without prompting, as long as the user is interactively signed-in. Microsoft Account sign-in keys are transactional keys, which means the user is always prompted when accessing the key.
|
Windows Hello for Business provides a PIN caching user experience by using a ticketing system. Rather than caching a PIN, processes cache a ticket they can use to request private key operations. Azure AD and Active Directory sign-in keys are cached under lock. This means the keys remain available for use without prompting, as long as the user is interactively signed-in. Microsoft Account sign-in keys are transactional keys, which means the user is always prompted when accessing the key.
|
||||||
|
|
||||||
Beginning with Windows 10, version 1709, Windows Hello for Business used as a smart card (smart card emulation that is enabled by default) provides the same user experience of default smart card PIN caching. Each process requesting a private key operation will prompt the user for the PIN on first use. Subsequent private key operations won't prompt the user for the PIN.
|
Beginning with Windows 10, version 1709, Windows Hello for Business used as a smart card (smart card emulation that is enabled by default) provides the same user experience of default smart card PIN caching. Each process requesting a private key operation will prompt the user for the PIN on first use. Subsequent private key operations won't prompt the user for the PIN.
|
||||||
|
|
||||||
The smart card emulation feature of Windows Hello for Business verifies the PIN and then discards the PIN in exchange for a ticket. The process doesn't receive the PIN, but rather the ticket that grants them private key operations. Windows 10 doesn't provide any Group Policy settings to adjust this caching.
|
The smart card emulation feature of Windows Hello for Business verifies the PIN and then discards the PIN in exchange for a ticket. The process doesn't receive the PIN, but rather the ticket that grants them private key operations. Windows 10 doesn't provide any Group Policy settings to adjust this caching.
|
||||||
|
|
||||||
|
|||||||
@ -45,9 +45,9 @@ Windows stores biometric data that is used to implement Windows Hello securely o
|
|||||||
|
|
||||||
## The difference between Windows Hello and Windows Hello for Business
|
## The difference between Windows Hello and Windows Hello for Business
|
||||||
|
|
||||||
- Individuals can create a PIN or biometric gesture on their personal devices for convenient sign-in. This use of Windows Hello is unique to the device on which it's set up, but can use a password hash depending on an individual's account type. This configuration is referred to as Windows Hello convenience PIN and it's not backed by asymmetric (public/private key) or certificate-based authentication.
|
- Individuals can create a PIN or biometric gesture on their personal devices for convenient sign-in. This use of Windows Hello is unique to the device on which it's set up, but can use a password hash depending on an individual's account type. This configuration is referred to as *Windows Hello convenience PIN* and it's not backed by asymmetric (public/private key) or certificate-based authentication.
|
||||||
|
|
||||||
- **Windows Hello for Business**, which is configured by group policy or mobile device management (MDM) policy, always uses key-based or certificate-based authentication. This behavior makes it more secure than **Windows Hello convenience PIN**.
|
- *Windows Hello for Business*, which is configured by group policy or mobile device management (MDM) policy, always uses key-based or certificate-based authentication. This behavior makes it more secure than *Windows Hello convenience PIN*.
|
||||||
|
|
||||||
## Benefits of Windows Hello
|
## Benefits of Windows Hello
|
||||||
|
|
||||||
|
|||||||
@ -15,7 +15,6 @@ metadata:
|
|||||||
ms.reviewer: prsriva
|
ms.reviewer: prsriva
|
||||||
ms.date: 01/22/2021
|
ms.date: 01/22/2021
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- M365-identity-device-management
|
|
||||||
- highpri
|
- highpri
|
||||||
|
|
||||||
# linkListType: architecture | concept | deploy | download | get-started | how-to-guide | learn | overview | quickstart | reference | tutorial | whats-new
|
# linkListType: architecture | concept | deploy | download | get-started | how-to-guide | learn | overview | quickstart | reference | tutorial | whats-new
|
||||||
|
|||||||
@ -1,26 +0,0 @@
|
|||||||
---
|
|
||||||
title: Microsoft-compatible security key
|
|
||||||
description: Learn how a Microsoft-compatible security key for Windows is different (and better) than any other FIDO2 security key.
|
|
||||||
ms.date: 11/14/2018
|
|
||||||
appliesto:
|
|
||||||
- ✅ <a href=https://learn.microsoft.com/windows/release-health/supported-versions-windows-client target=_blank>Windows 10 and later</a>
|
|
||||||
ms.topic: article
|
|
||||||
---
|
|
||||||
# What is a Microsoft-compatible security key?
|
|
||||||
|
|
||||||
> [!Warning]
|
|
||||||
> Some information relates to pre-released product that may change before it is commercially released. Microsoft makes no warranties, express or implied, with respect to the information provided here.
|
|
||||||
|
|
||||||
|
|
||||||
Microsoft has been aligned with the [FIDO Alliance](https://fidoalliance.org/) with a mission to replace passwords with an easy to use, strong 2FA credential. We have been working with our partners to extensively test and deliver a seamless and secure authentication experience to end users. See [FIDO2 security keys features and providers](/azure/active-directory/authentication/concept-authentication-passwordless#fido2-security-keys).
|
|
||||||
|
|
||||||
The [FIDO2 CTAP specification](https://fidoalliance.org/specs/fido-v2.0-id-20180227/fido-client-to-authenticator-protocol-v2.0-id-20180227.html) contains a few optional features and extensions which are crucial to provide that seamless and secure experience.
|
|
||||||
|
|
||||||
A security key **MUST** implement the following features and extensions from the FIDO2 CTAP protocol to be Microsoft-compatible:
|
|
||||||
|
|
||||||
| #</br> | Feature / Extension trust</br> | Why is this required? </br> |
|
|
||||||
| --- | --- | --- |
|
|
||||||
| 1 | Resident key | This feature enables the security key to be portable, where your credential is stored on the security key |
|
|
||||||
| 2 | Client pin | This feature enables you to protect your credentials with a second factor and applies to security keys that do not have a user interface|
|
|
||||||
| 3 | hmac-secret | This extension ensures you can sign-in to your device when it's off-line or in airplane mode |
|
|
||||||
| 4 | Multiple accounts per RP | This feature ensures you can use the same security key across multiple services like Microsoft Account (MSA) and Azure Active Directory (AAD) |
|
|
||||||
@ -1,30 +0,0 @@
|
|||||||
---
|
|
||||||
title: Reset-security-key
|
|
||||||
description: Windows 10 and Windows 11 enables users to sign in to their device using a security key. How to reset a security key
|
|
||||||
ms.date: 11/14/2018
|
|
||||||
appliesto:
|
|
||||||
- ✅ <a href=https://learn.microsoft.com/windows/release-health/supported-versions-windows-client target=_blank>Windows 10 and later</a>
|
|
||||||
ms.topic: article
|
|
||||||
---
|
|
||||||
# How to reset a Microsoft-compatible security key?
|
|
||||||
> [!Warning]
|
|
||||||
> Some information relates to pre-released product that may change before it is commercially released. Microsoft makes no warranties, express or implied, with respect to the information provided here.
|
|
||||||
|
|
||||||
>[!IMPORTANT]
|
|
||||||
>This operation will wipe everything from your security key and reset it to factory defaults.</br> **All data and credentials will be cleared.**
|
|
||||||
|
|
||||||
|
|
||||||
A [Microsoft-compatible security key](./microsoft-compatible-security-key.md) can be reset via Settings app (Settings > Accounts > Sign-in options > Security key).
|
|
||||||
</br>
|
|
||||||
Follow the instructions in the Settings app and look for specific instructions based on your security key manufacturer below:
|
|
||||||
|
|
||||||
|
|
||||||
|Security key manufacturer</br> | Reset instructions </br> |
|
|
||||||
| --- | --- |
|
|
||||||
|Yubico | **USB:** Remove and reinsert the security key. When the LED on the security key begins flashing, touch the metal contact <br> **NFC:** Tap the security key on the reader <br>|
|
|
||||||
|Feitian | Touch the blinking fingerprint sensor twice to reset the key|
|
|
||||||
|HID | Tap the card on the reader twice to reset it |
|
|
||||||
|
|
||||||
>[!NOTE]
|
|
||||||
>The steps to reset your security key may vary based on the security key manufacturer.</br>
|
|
||||||
>If your security key is not listed here, please reach out to your security key manufacturer for reset instructions.
|
|
||||||
@ -16,7 +16,7 @@ Starting in **Windows 11, version 22H2**, WebAuthn APIs support ECC algorithms.
|
|||||||
|
|
||||||
## What does this mean?
|
## What does this mean?
|
||||||
|
|
||||||
By using WebAuthn APIs, developer partners and the developer community can use [Windows Hello](./index.yml) or [FIDO2 Security Keys](./microsoft-compatible-security-key.md) to implement passwordless multi-factor authentication for their applications on Windows devices.
|
By using WebAuthn APIs, developer partners and the developer community can use [Windows Hello](./index.yml) or [FIDO2 Security Keys](/azure/active-directory/authentication/howto-authentication-passwordless-security-key) to implement passwordless multi-factor authentication for their applications on Windows devices.
|
||||||
|
|
||||||
Users of these apps or sites can use any browser that supports WebAuthn APIs for passwordless authentication. Users will have a familiar and consistent experience on Windows, no matter which browser they use.
|
Users of these apps or sites can use any browser that supports WebAuthn APIs for passwordless authentication. Users will have a familiar and consistent experience on Windows, no matter which browser they use.
|
||||||
|
|
||||||
|
|||||||
@ -1,9 +1,9 @@
|
|||||||
---
|
---
|
||||||
title: How to use Single Sign-On (SSO) over VPN and Wi-Fi connections (Windows 10 and Windows 11)
|
title: How to use Single Sign-On (SSO) over VPN and Wi-Fi connections
|
||||||
description: Explains requirements to enable Single Sign-On (SSO) to on-premises domain resources over WiFi or VPN connections.
|
description: Explains requirements to enable Single Sign-On (SSO) to on-premises domain resources over WiFi or VPN connections.
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
author: paolomatarazzo
|
author: paolomatarazzo
|
||||||
ms.date: 03/22/2022
|
ms.date: 12/28/2022
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.author: paoloma
|
ms.author: paoloma
|
||||||
ms.reviewer: pesmith
|
ms.reviewer: pesmith
|
||||||
@ -18,47 +18,49 @@ ms.topic: how-to
|
|||||||
|
|
||||||
This article explains requirements to enable Single Sign-On (SSO) to on-premises domain resources over WiFi or VPN connections. The following scenarios are typically used:
|
This article explains requirements to enable Single Sign-On (SSO) to on-premises domain resources over WiFi or VPN connections. The following scenarios are typically used:
|
||||||
|
|
||||||
- Connecting to a network using Wi-Fi or VPN.
|
- Connecting to a network using Wi-Fi or VPN
|
||||||
- Use credentials for WiFi or VPN authentication to also authenticate requests to access a domain resource without being prompted for your domain credentials.
|
- Use credentials for Wi-Fi or VPN authentication to also authenticate requests to access domain resources, without being prompted for domain credentials
|
||||||
|
|
||||||
For example, you want to connect to a corporate network and access an internal website that requires Windows integrated authentication.
|
For example, you want to connect to a corporate network and access an internal website that requires Windows integrated authentication.
|
||||||
|
|
||||||
The credentials that are used for the connection authentication are placed in Credential Manager as the default credentials for the logon session. Credential Manager stores credentials that can be used for specific domain resources. These are based on the target name of the resource:
|
The credentials that are used for the connection authentication are placed in *Credential Manager* as the default credentials for the **logon session**. Credential Manager stores credentials that can be used for specific domain resources. These are based on the target name of the resource:
|
||||||
- For VPN, the VPN stack saves its credential as the session default.
|
|
||||||
- For WiFi, Extensible Authentication Protocol (EAP) provides support.
|
|
||||||
|
|
||||||
The credentials are placed in Credential Manager as a "\*Session" credential.
|
- For VPN, the VPN stack saves its credential as the **session default**
|
||||||
A "\*Session" credential implies that it is valid for the current user session.
|
- For WiFi, Extensible Authentication Protocol (EAP) provides support
|
||||||
The credentials are also cleaned up when the WiFi or VPN connection is disconnected.
|
|
||||||
|
The credentials are placed in Credential Manager as a *session credential*:
|
||||||
|
|
||||||
|
- A *session credential* implies that it is valid for the current user session
|
||||||
|
- The credentials are cleaned up when the WiFi or VPN connection is disconnected
|
||||||
|
|
||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> In Windows 10, version 21h2 and later, the "\*Session" credential is not visible in Credential Manager.
|
> In Windows 10, version 21H2 and later, the *session credential* is not visible in Credential Manager.
|
||||||
|
|
||||||
For example, if someone using Microsoft Edge tries to access a domain resource, Microsoft Edge has the right Enterprise Authentication capability. This allows [WinInet](/windows/win32/wininet/wininet-reference) to release the credentials that it gets from the Credential Manager to the SSP that is requesting it.
|
For example, if someone using Microsoft Edge tries to access a domain resource, Microsoft Edge has the right Enterprise Authentication capability. This allows [WinInet](/windows/win32/wininet/wininet-reference) to release the credentials that it gets from Credential Manager to the SSP that is requesting it.
|
||||||
For more information about the Enterprise Authentication capability, see [App capability declarations](/windows/uwp/packaging/app-capability-declarations).
|
For more information about the Enterprise Authentication capability, see [App capability declarations](/windows/uwp/packaging/app-capability-declarations).
|
||||||
|
|
||||||
The local security authority will look at the device application to determine if it has the right capability. This includes items such as a Universal Windows Platform (UWP) application.
|
The local security authority will look at the device application to determine if it has the right capability. This includes items such as a Universal Windows Platform (UWP) application.
|
||||||
If the app isn't a UWP, it doesn't matter.
|
If the app isn't a UWP, it doesn't matter.
|
||||||
But if the application is a UWP app, it will evaluate at the device capability for Enterprise Authentication.
|
But, if the application is a UWP app, it will evaluate at the device capability for Enterprise Authentication.
|
||||||
If it does have that capability and if the resource that you're trying to access is in the Intranet zone in the Internet Options (ZoneMap), then the credential will be released.
|
If it does have that capability and if the resource that you're trying to access is in the Intranet zone in the Internet Options (ZoneMap), then the credential will be released.
|
||||||
This behavior helps prevent credentials from being misused by untrusted third parties.
|
This behavior helps prevent credentials from being misused by untrusted third parties.
|
||||||
|
|
||||||
## Intranet zone
|
## Intranet zone
|
||||||
|
|
||||||
For the Intranet zone, by default it only allows single-label names, such as Http://finance.
|
For the Intranet zone, by default it only allows single-label names, such as *http://finance*.
|
||||||
If the resource that needs to be accessed has multiple domain labels, then the workaround is to use the [Registry CSP](/windows/client-management/mdm/registry-csp).
|
If the resource that needs to be accessed has multiple domain labels, then the workaround is to use the [Registry CSP](/windows/client-management/mdm/registry-csp).
|
||||||
|
|
||||||
### Setting the ZoneMap
|
### Setting the ZoneMap
|
||||||
|
|
||||||
The ZoneMap is controlled using a registry that can be set through MDM.
|
The ZoneMap is controlled using a registry that can be set through MDM.
|
||||||
By default, single-label names such as http://finance are already in the intranet zone.
|
By default, single-label names such as *http://finance* are already in the intranet zone.
|
||||||
For multi-label names, such as http://finance.net, the ZoneMap needs to be updated.
|
For multi-label names, such as *http://finance.net*, the ZoneMap needs to be updated.
|
||||||
|
|
||||||
## MDM Policy
|
## MDM Policy
|
||||||
|
|
||||||
OMA URI example:
|
OMA URI example:
|
||||||
|
|
||||||
./Vendor/MSFT/Registry/HKU/S-1-5-21-2702878673-795188819-444038987-2781/Software/Microsoft/Windows/CurrentVersion/Internet%20Settings/ZoneMap/Domains/`<domain name>`/* as an Integer Value of 1 for each of the domains that you want to SSO into from your device. This adds the specified domains to the Intranet Zone of the Microsoft Edge browser.
|
`./Vendor/MSFT/Registry/HKU/S-1-5-21-2702878673-795188819-444038987-2781/Software/Microsoft/Windows/CurrentVersion/Internet%20Settings/ZoneMap/Domains/<domain name>` as an `Integer` value of `1` for each of the domains that you want to SSO into from your device. This adds the specified domains to the Intranet Zone of the Microsoft Edge browser.
|
||||||
|
|
||||||
## Credential requirements
|
## Credential requirements
|
||||||
|
|
||||||
@ -66,10 +68,10 @@ For VPN, the following types of credentials will be added to credential manager
|
|||||||
|
|
||||||
- Username and password
|
- Username and password
|
||||||
- Certificate-based authentication:
|
- Certificate-based authentication:
|
||||||
- TPM Key Storage Provider (KSP) Certificate
|
- TPM Key Storage Provider (KSP) Certificate
|
||||||
- Software Key Storage Provider (KSP) Certificates
|
- Software Key Storage Provider (KSP) Certificates
|
||||||
- Smart Card Certificate
|
- Smart Card Certificate
|
||||||
- Windows Hello for Business Certificate
|
- Windows Hello for Business Certificate
|
||||||
|
|
||||||
The username should also include a domain that can be reached over the connection (VPN or WiFi).
|
The username should also include a domain that can be reached over the connection (VPN or WiFi).
|
||||||
|
|
||||||
@ -79,10 +81,10 @@ If the credentials are certificate-based, then the elements in the following tab
|
|||||||
|
|
||||||
| Template element | Configuration |
|
| Template element | Configuration |
|
||||||
|------------------|---------------|
|
|------------------|---------------|
|
||||||
| SubjectName | The user’s distinguished name (DN) where the domain components of the distinguished name reflect the internal DNS namespace when the SubjectAlternativeName does not have the fully qualified UPN required to find the domain controller. </br>This requirement is relevant in multi-forest environments as it ensures a domain controller can be located. |
|
| SubjectName | The user's distinguished name (DN) where the domain components of the distinguished name reflect the internal DNS namespace when the SubjectAlternativeName does not have the fully qualified UPN required to find the domain controller. </br>This requirement is relevant in multi-forest environments as it ensures a domain controller can be located. |
|
||||||
| SubjectAlternativeName | The user’s fully qualified UPN where a domain name component of the user’s UPN matches the organizations internal domain’s DNS namespace. </br>This requirement is relevant in multi-forest environments as it ensures a domain controller can be located when the SubjectName does not have the DN required to find the domain controller. |
|
| SubjectAlternativeName | The user's fully qualified UPN where a domain name component of the user's UPN matches the organizations internal domain's DNS namespace. </br>This requirement is relevant in multi-forest environments as it ensures a domain controller can be located when the SubjectName does not have the DN required to find the domain controller. |
|
||||||
| Key Storage Provider (KSP) | If the device is joined to Azure AD, a discrete SSO certificate is used. |
|
| Key Storage Provider (KSP) | If the device is joined to Azure AD, a discrete SSO certificate is used. |
|
||||||
| EnhancedKeyUsage | One or more of the following EKUs is required: </br>- Client Authentication (for the VPN) </br>- EAP Filtering OID (for Windows Hello for Business)</br>- SmartCardLogon (for Azure AD-joined devices) </br>If the domain controllers require smart card EKU either:</br>- SmartCardLogon</br>- id-pkinit-KPClientAuth (1.3.6.1.5.2.3.4) <br>Otherwise:</br>- TLS/SSL Client Authentication (1.3.6.1.5.5.7.3.2) |
|
| EnhancedKeyUsage | One or more of the following EKUs is required: </br><ul><li>Client Authentication (for the VPN)</li><li>EAP Filtering OID (for Windows Hello for Business)</li><li>SmartCardLogon (for Azure AD-joined devices)</li></ul>If the domain controllers require smart card EKU either:<ul><li>SmartCardLogon</li><li>id-pkinit-KPClientAuth (1.3.6.1.5.2.3.4) </li></ul>Otherwise:</br><ul><li>TLS/SSL Client Authentication (1.3.6.1.5.5.7.3.2)</li></ul> |
|
||||||
|
|
||||||
## NDES server configuration
|
## NDES server configuration
|
||||||
|
|
||||||
|
|||||||
@ -1,22 +1,19 @@
|
|||||||
### YamlMime:Landing
|
### YamlMime:Landing
|
||||||
|
|
||||||
title: Windows security # < 60 chars
|
title: Windows security
|
||||||
summary: Built with Zero Trust principles at the core to safeguard data and access anywhere, keeping you protected and productive. # < 160 chars
|
summary: Built with Zero Trust principles at the core to safeguard data and access anywhere, keeping you protected and productive.
|
||||||
|
|
||||||
metadata:
|
metadata:
|
||||||
title: Windows security # Required; page title displayed in search results. Include the brand. < 60 chars.
|
title: Windows security
|
||||||
description: Learn about Windows security # Required; article description that is displayed in search results. < 160 chars.
|
description: Learn about Windows security technologies and how to use them to protect your data and devices.
|
||||||
ms.topic: landing-page
|
ms.topic: landing-page
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- m365-security-compliance
|
|
||||||
- highpri
|
- highpri
|
||||||
ms.custom: intro-hub-or-landing
|
|
||||||
author: paolomatarazzo
|
author: paolomatarazzo
|
||||||
ms.author: paoloma
|
ms.author: paoloma
|
||||||
ms.date: 09/20/2021
|
ms.date: 12/19/2022
|
||||||
localization_priority: Priority
|
|
||||||
|
|
||||||
# linkListType: architecture | concept | deploy | download | get-started | how-to-guide | learn | overview | quickstart | reference | tutorial | video | whats-new
|
# linkListType: architecture | concept | deploy | download | get-started | how-to-guide | learn | overview | quickstart | reference | tutorial | video | whats-new
|
||||||
|
|
||||||
|
|||||||
@ -2,19 +2,13 @@
|
|||||||
metadata:
|
metadata:
|
||||||
title: BitLocker and Active Directory Domain Services (AD DS) FAQ (Windows 10)
|
title: BitLocker and Active Directory Domain Services (AD DS) FAQ (Windows 10)
|
||||||
description: Learn more about how BitLocker and Active Directory Domain Services (AD DS) can work together to keep devices secure.
|
description: Learn more about how BitLocker and Active Directory Domain Services (AD DS) can work together to keep devices secure.
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
audience: ITPro
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- M365-security-compliance
|
|
||||||
- highpri
|
- highpri
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
@ -22,9 +16,8 @@ metadata:
|
|||||||
title: BitLocker and Active Directory Domain Services (AD DS) FAQ
|
title: BitLocker and Active Directory Domain Services (AD DS) FAQ
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
@ -2,28 +2,19 @@
|
|||||||
metadata:
|
metadata:
|
||||||
title: BitLocker deployment and administration FAQ (Windows 10)
|
title: BitLocker deployment and administration FAQ (Windows 10)
|
||||||
description: Browse frequently asked questions about BitLocker deployment and administration, such as, "Can BitLocker deployment be automated in an enterprise environment?"
|
description: Browse frequently asked questions about BitLocker deployment and administration, such as, "Can BitLocker deployment be automated in an enterprise environment?"
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.reviewer:
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
ms.custom: bitlocker
|
ms.custom: bitlocker
|
||||||
title: BitLocker frequently asked questions (FAQ)
|
title: BitLocker frequently asked questions (FAQ)
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
|
|
||||||
sections:
|
sections:
|
||||||
|
|||||||
@ -2,20 +2,13 @@
|
|||||||
metadata:
|
metadata:
|
||||||
title: BitLocker FAQ (Windows 10)
|
title: BitLocker FAQ (Windows 10)
|
||||||
description: Find the answers you need by exploring this brief hub page listing FAQ pages for various aspects of BitLocker.
|
description: Find the answers you need by exploring this brief hub page listing FAQ pages for various aspects of BitLocker.
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.reviewer:
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
audience: ITPro
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- M365-security-compliance
|
|
||||||
- highpri
|
- highpri
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
@ -23,9 +16,8 @@ metadata:
|
|||||||
title: BitLocker frequently asked questions (FAQ) resources
|
title: BitLocker frequently asked questions (FAQ) resources
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
This article links to frequently asked questions about BitLocker. BitLocker is a data protection feature that encrypts drives on computers to help prevent data theft or exposure. BitLocker-protected computers can also delete data more securely when they're decommissioned because it's much more difficult to recover deleted data from an encrypted drive than from a non-encrypted drive.
|
This article links to frequently asked questions about BitLocker. BitLocker is a data protection feature that encrypts drives on computers to help prevent data theft or exposure. BitLocker-protected computers can also delete data more securely when they're decommissioned because it's much more difficult to recover deleted data from an encrypted drive than from a non-encrypted drive.
|
||||||
|
|
||||||
|
|||||||
@ -2,27 +2,20 @@
|
|||||||
metadata:
|
metadata:
|
||||||
title: BitLocker Key Management FAQ (Windows 10)
|
title: BitLocker Key Management FAQ (Windows 10)
|
||||||
description: Browse frequently asked questions concerning the requirements to use, upgrade, deploy and administer, and key management policies for BitLocker.
|
description: Browse frequently asked questions concerning the requirements to use, upgrade, deploy and administer, and key management policies for BitLocker.
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
audience: ITPro
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
ms.custom: bitlocker
|
ms.custom: bitlocker
|
||||||
title: BitLocker Key Management FAQ
|
title: BitLocker Key Management FAQ
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
|
|
||||||
sections:
|
sections:
|
||||||
|
|||||||
@ -35,6 +35,11 @@ Starting with Windows 10 version 1703, the enablement of BitLocker can be trigge
|
|||||||
|
|
||||||
For hardware that is compliant with Modern Standby and HSTI, when using either of these features, [BitLocker Device Encryption](bitlocker-device-encryption-overview-windows-10.md#bitlocker-device-encryption) is automatically turned on whenever the user joins a device to Azure AD. Azure AD provides a portal where recovery keys are also backed up, so users can retrieve their own recovery key for self-service, if necessary. For older devices that aren't yet encrypted, beginning with Windows 10 version 1703, admins can use the [BitLocker CSP](/windows/client-management/mdm/bitlocker-csp/) to trigger encryption and store the recovery key in Azure AD. This process and feature is applicable to Azure Hybrid AD as well.
|
For hardware that is compliant with Modern Standby and HSTI, when using either of these features, [BitLocker Device Encryption](bitlocker-device-encryption-overview-windows-10.md#bitlocker-device-encryption) is automatically turned on whenever the user joins a device to Azure AD. Azure AD provides a portal where recovery keys are also backed up, so users can retrieve their own recovery key for self-service, if necessary. For older devices that aren't yet encrypted, beginning with Windows 10 version 1703, admins can use the [BitLocker CSP](/windows/client-management/mdm/bitlocker-csp/) to trigger encryption and store the recovery key in Azure AD. This process and feature is applicable to Azure Hybrid AD as well.
|
||||||
|
|
||||||
|
> [!NOTE]
|
||||||
|
> To manage Bitlocker, except to enable and disable it, one of the following licenses must be assigned to your users:
|
||||||
|
> - Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, and E5).
|
||||||
|
> - Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 and A5).
|
||||||
|
|
||||||
## Managing workplace-joined PCs and phones
|
## Managing workplace-joined PCs and phones
|
||||||
|
|
||||||
For Windows PCs and Windows Phones that are enrolled using **Connect to work or school account**, BitLocker Device Encryption is managed over MDM, the same as devices joined to Azure AD.
|
For Windows PCs and Windows Phones that are enrolled using **Connect to work or school account**, BitLocker Device Encryption is managed over MDM, the same as devices joined to Azure AD.
|
||||||
|
|||||||
@ -4,15 +4,10 @@ metadata:
|
|||||||
description: Familiarize yourself with BitLocker Network Unlock. Learn how it can make desktop and server management easier within domain environments.
|
description: Familiarize yourself with BitLocker Network Unlock. Learn how it can make desktop and server management easier within domain environments.
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
audience: ITPro
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
ms.reviewer:
|
ms.reviewer:
|
||||||
|
|||||||
@ -2,19 +2,13 @@
|
|||||||
metadata:
|
metadata:
|
||||||
title: BitLocker overview and requirements FAQ (Windows 10)
|
title: BitLocker overview and requirements FAQ (Windows 10)
|
||||||
description: This article for IT professionals answers frequently asked questions concerning the requirements to use BitLocker.
|
description: This article for IT professionals answers frequently asked questions concerning the requirements to use BitLocker.
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
audience: ITPro
|
||||||
ms.collection:
|
ms.collection:
|
||||||
- M365-security-compliance
|
|
||||||
- highpri
|
- highpri
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
@ -22,9 +16,8 @@ metadata:
|
|||||||
title: BitLocker Overview and Requirements FAQ
|
title: BitLocker Overview and Requirements FAQ
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
|
|
||||||
sections:
|
sections:
|
||||||
|
|||||||
@ -1,28 +1,21 @@
|
|||||||
### YamlMime:FAQ
|
### YamlMime:FAQ
|
||||||
metadata:
|
metadata:
|
||||||
title: BitLocker Security FAQ (Windows 10)
|
title: BitLocker Security FAQ
|
||||||
description: Learn more about how BitLocker security works. Browse frequently asked questions, such as, "What form of encryption does BitLocker use?"
|
description: Learn more about how BitLocker security works. Browse frequently asked questions, such as, "What form of encryption does BitLocker use?"
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
audience: ITPro
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
ms.custom: bitlocker
|
ms.custom: bitlocker
|
||||||
title: BitLocker Security FAQ
|
title: BitLocker Security FAQ
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
@ -1,19 +1,13 @@
|
|||||||
### YamlMime:FAQ
|
### YamlMime:FAQ
|
||||||
metadata:
|
metadata:
|
||||||
title: BitLocker To Go FAQ (Windows 10)
|
title: BitLocker To Go FAQ
|
||||||
description: "Learn more about BitLocker To Go"
|
description: "Learn more about BitLocker To Go"
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
ms.mktglfcycl: deploy
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
audience: ITPro
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
ms.custom: bitlocker
|
ms.custom: bitlocker
|
||||||
|
|||||||
@ -1,18 +1,12 @@
|
|||||||
### YamlMime:FAQ
|
### YamlMime:FAQ
|
||||||
metadata:
|
metadata:
|
||||||
title: BitLocker Upgrading FAQ (Windows 10)
|
title: BitLocker Upgrading FAQ
|
||||||
description: Learn more about upgrading systems that have BitLocker enabled. Find frequently asked questions, such as, "Can I upgrade to Windows 10 with BitLocker enabled?"
|
description: Learn more about upgrading systems that have BitLocker enabled. Find frequently asked questions, such as, "Can I upgrade to Windows 10 with BitLocker enabled?"
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
ms.reviewer:
|
ms.reviewer:
|
||||||
@ -20,9 +14,8 @@ metadata:
|
|||||||
title: BitLocker Upgrading FAQ
|
title: BitLocker Upgrading FAQ
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
|
|
||||||
sections:
|
sections:
|
||||||
|
|||||||
@ -1,28 +1,19 @@
|
|||||||
### YamlMime:FAQ
|
### YamlMime:FAQ
|
||||||
metadata:
|
metadata:
|
||||||
title: Using BitLocker with other programs FAQ (Windows 10)
|
title: Using BitLocker with other programs FAQ
|
||||||
description: Learn how to integrate BitLocker with other software on a device.
|
description: Learn how to integrate BitLocker with other software on a device.
|
||||||
ms.assetid: c40f87ac-17d3-47b2-afc6-6c641f72ecee
|
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.mktglfcycl: explore
|
|
||||||
ms.sitesec: library
|
|
||||||
ms.pagetype: security
|
|
||||||
ms.localizationpriority: medium
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
audience: ITPro
|
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 11/08/2022
|
ms.date: 11/08/2022
|
||||||
ms.custom: bitlocker
|
|
||||||
title: Using BitLocker with other programs FAQ
|
title: Using BitLocker with other programs FAQ
|
||||||
summary: |
|
summary: |
|
||||||
**Applies to:**
|
**Applies to:**
|
||||||
- Windows 10
|
- Windows 10 and later
|
||||||
- Windows 11
|
- Windows Server 2016 and later
|
||||||
- Windows Server 2016 and above
|
|
||||||
|
|
||||||
|
|
||||||
sections:
|
sections:
|
||||||
|
|||||||
@ -3,16 +3,17 @@ title: Configure Personal Data Encryption (PDE) in Intune
|
|||||||
description: Configuring and enabling Personal Data Encryption (PDE) required and recommended policies in Intune
|
description: Configuring and enabling Personal Data Encryption (PDE) required and recommended policies in Intune
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
ms.reviewer: rafals
|
ms.reviewer: rhonnegowda
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.topic: how-to
|
ms.topic: how-to
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.localizationpriority: medium
|
ms.localizationpriority: medium
|
||||||
ms.date: 09/22/2022
|
ms.date: 12/13/2022
|
||||||
---
|
---
|
||||||
|
|
||||||
<!-- Max 5963468 OS 32516487 -->
|
<!-- Max 5963468 OS 32516487 -->
|
||||||
|
<!-- Max 6946251 -->
|
||||||
|
|
||||||
# Configure Personal Data Encryption (PDE) policies in Intune
|
# Configure Personal Data Encryption (PDE) policies in Intune
|
||||||
|
|
||||||
@ -20,104 +21,243 @@ ms.date: 09/22/2022
|
|||||||
|
|
||||||
### Enable Personal Data Encryption (PDE)
|
### Enable Personal Data Encryption (PDE)
|
||||||
|
|
||||||
1. Sign into the Intune
|
1. Sign into [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
||||||
|
|
||||||
2. Navigate to **Devices** > **Configuration Profiles**
|
2. Navigate to **Devices** > **Configuration Profiles**
|
||||||
|
|
||||||
3. Select **Create profile**
|
3. Select **Create profile**
|
||||||
|
|
||||||
4. Under **Platform**, select **Windows 10 and later**
|
4. Under **Platform**, select **Windows 10 and later**
|
||||||
|
|
||||||
5. Under **Profile type**, select **Templates**
|
5. Under **Profile type**, select **Templates**
|
||||||
|
|
||||||
6. Under **Template name**, select **Custom**, and then select **Create**
|
6. Under **Template name**, select **Custom**, and then select **Create**
|
||||||
7. On the ****Basics** tab:
|
|
||||||
|
7. In **Basics**:
|
||||||
|
|
||||||
1. Next to **Name**, enter **Personal Data Encryption**
|
1. Next to **Name**, enter **Personal Data Encryption**
|
||||||
2. Next to **Description**, enter a description
|
2. Next to **Description**, enter a description
|
||||||
|
|
||||||
8. Select **Next**
|
8. Select **Next**
|
||||||
9. On the **Configuration settings** tab, select **Add**
|
|
||||||
10. In the **Add Row** window:
|
9. In **Configuration settings**, select **Add**
|
||||||
|
|
||||||
|
10. In **Add Row**:
|
||||||
|
|
||||||
1. Next to **Name**, enter **Personal Data Encryption**
|
1. Next to **Name**, enter **Personal Data Encryption**
|
||||||
2. Next to **Description**, enter a description
|
2. Next to **Description**, enter a description
|
||||||
3. Next to **OMA-URI**, enter in **./User/Vendor/MSFT/PDE/EnablePersonalDataEncryption**
|
3. Next to **OMA-URI**, enter in **./User/Vendor/MSFT/PDE/EnablePersonalDataEncryption**
|
||||||
4. Next to **Data type**, select **Integer**
|
4. Next to **Data type**, select **Integer**
|
||||||
5. Next to **Value**, enter in **1**
|
5. Next to **Value**, enter in **1**
|
||||||
|
|
||||||
11. Select **Save**, and then select **Next**
|
11. Select **Save**, and then select **Next**
|
||||||
12. On the **Assignments** tab:
|
|
||||||
|
12. In **Assignments**:
|
||||||
|
|
||||||
1. Under **Included groups**, select **Add groups**
|
1. Under **Included groups**, select **Add groups**
|
||||||
2. Select the groups that the PDE policy should be deployed to
|
2. Select the groups that the PDE policy should be deployed to
|
||||||
3. Select **Select**
|
3. Select **Select**
|
||||||
4. Select **Next**
|
4. Select **Next**
|
||||||
13. On the **Applicability Rules** tab, configure if necessary and then select **Next**
|
|
||||||
14. On the **Review + create** tab, review the configuration to make sure everything is configured correctly, and then select **Create**
|
|
||||||
|
|
||||||
#### Disable Winlogon automatic restart sign-on (ARSO)
|
13. In **Applicability Rules**, configure if necessary and then select **Next**
|
||||||
|
|
||||||
|
14. In **Review + create**, review the configuration to make sure everything is configured correctly, and then select **Create**
|
||||||
|
|
||||||
|
### Disable Winlogon automatic restart sign-on (ARSO)
|
||||||
|
|
||||||
|
1. Sign into [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
||||||
|
|
||||||
1. Sign into the Intune
|
|
||||||
2. Navigate to **Devices** > **Configuration Profiles**
|
2. Navigate to **Devices** > **Configuration Profiles**
|
||||||
|
|
||||||
3. Select **Create profile**
|
3. Select **Create profile**
|
||||||
|
|
||||||
4. Under **Platform**, select **Windows 10 and later**
|
4. Under **Platform**, select **Windows 10 and later**
|
||||||
|
|
||||||
5. Under **Profile type**, select **Templates**
|
5. Under **Profile type**, select **Templates**
|
||||||
|
|
||||||
6. Under **Template name**, select **Administrative templates**, and then select **Create**
|
6. Under **Template name**, select **Administrative templates**, and then select **Create**
|
||||||
7. On the ****Basics** tab:
|
|
||||||
|
7. In **Basics**:
|
||||||
|
|
||||||
1. Next to **Name**, enter **Disable ARSO**
|
1. Next to **Name**, enter **Disable ARSO**
|
||||||
2. Next to **Description**, enter a description
|
2. Next to **Description**, enter a description
|
||||||
|
|
||||||
8. Select **Next**
|
8. Select **Next**
|
||||||
9. On the **Configuration settings** tab, under **Computer Configuration**, navigate to **Windows Components** > **Windows Logon Options**
|
|
||||||
|
9. In **Configuration settings**, under **Computer Configuration**, navigate to **Windows Components** > **Windows Logon Options**
|
||||||
|
|
||||||
10. Select **Sign-in and lock last interactive user automatically after a restart**
|
10. Select **Sign-in and lock last interactive user automatically after a restart**
|
||||||
|
|
||||||
11. In the **Sign-in and lock last interactive user automatically after a restart** window that opens, select **Disabled**, and then select **OK**
|
11. In the **Sign-in and lock last interactive user automatically after a restart** window that opens, select **Disabled**, and then select **OK**
|
||||||
|
|
||||||
12. Select **Next**
|
12. Select **Next**
|
||||||
13. On the **Scope tags** tab, configure if necessary and then select **Next**
|
|
||||||
12. On the **Assignments** tab:
|
13. In **Scope tags**, configure if necessary and then select **Next**
|
||||||
|
|
||||||
|
14. In **Assignments**:
|
||||||
|
|
||||||
1. Under **Included groups**, select **Add groups**
|
1. Under **Included groups**, select **Add groups**
|
||||||
2. Select the groups that the ARSO policy should be deployed to
|
2. Select the groups that the ARSO policy should be deployed to
|
||||||
3. Select **Select**
|
3. Select **Select**
|
||||||
4. Select **Next**
|
4. Select **Next**
|
||||||
13. On the **Review + create** tab, review the configuration to make sure everything is configured correctly, and then select **Create**
|
|
||||||
|
|
||||||
## Recommended prerequisites
|
15. In **Review + create**, review the configuration to make sure everything is configured correctly, and then select **Create**
|
||||||
|
|
||||||
#### Disable crash dumps
|
## Security hardening recommendations
|
||||||
|
|
||||||
|
### Disable kernel-mode crash dumps and live dumps
|
||||||
|
|
||||||
|
1. Sign into [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
||||||
|
|
||||||
1. Sign into the Intune
|
|
||||||
2. Navigate to **Devices** > **Configuration Profiles**
|
2. Navigate to **Devices** > **Configuration Profiles**
|
||||||
|
|
||||||
3. Select **Create profile**
|
3. Select **Create profile**
|
||||||
|
|
||||||
4. Under **Platform**, select **Windows 10 and later**
|
4. Under **Platform**, select **Windows 10 and later**
|
||||||
|
|
||||||
5. Under **Profile type**, select **Settings catalog**, and then select **Create**
|
5. Under **Profile type**, select **Settings catalog**, and then select **Create**
|
||||||
6. On the ****Basics** tab:
|
|
||||||
1. Next to **Name**, enter **Disable Hibernation**
|
6. In **Basics**:
|
||||||
|
|
||||||
|
1. Next to **Name**, enter **Disable Kernel-Mode Crash Dumps**
|
||||||
2. Next to **Description**, enter a description
|
2. Next to **Description**, enter a description
|
||||||
|
|
||||||
7. Select **Next**
|
7. Select **Next**
|
||||||
8. On the **Configuration settings** tab, select **Add settings**
|
|
||||||
9. In the **Settings picker** windows, select **Memory Dump**
|
8. In **Configuration settings**, select **Add settings**
|
||||||
10. When the settings appear in the lower pane, under **Setting name**, select both **Allow Crash Dump** and **Allow Live Dump**, and then select the **X** in the top right corner of the **Settings picker** window to close the window
|
|
||||||
|
9. In the **Settings picker** window, under **Browse by category**, select **Memory Dump**
|
||||||
|
|
||||||
|
10. When the settings appear under **Setting name**, select both **Allow Crash Dump** and **Allow Live Dump**, and then select the **X** in the top right corner of the **Settings picker** window to close the window
|
||||||
|
|
||||||
11. Change both **Allow Live Dump** and **Allow Crash Dump** to **Block**, and then select **Next**
|
11. Change both **Allow Live Dump** and **Allow Crash Dump** to **Block**, and then select **Next**
|
||||||
12. On the **Scope tags** tab, configure if necessary and then select **Next**
|
|
||||||
13. On the **Assignments** tab:
|
12. In **Scope tags**, configure if necessary and then select **Next**
|
||||||
|
|
||||||
|
13. In **Assignments**:
|
||||||
|
|
||||||
1. Under **Included groups**, select **Add groups**
|
1. Under **Included groups**, select **Add groups**
|
||||||
2. Select the groups that the crash dumps policy should be deployed to
|
2. Select the groups that the disable crash dumps policy should be deployed to
|
||||||
3. Select **Select**
|
3. Select **Select**
|
||||||
4. Select **Next**
|
4. Select **Next**
|
||||||
14. On the **Review + create** tab, review the configuration to make sure everything is configured correctly, and then select **Create**
|
|
||||||
|
|
||||||
#### Disable hibernation
|
14. In **Review + create**, review the configuration to make sure everything is configured correctly, and then select **Create**
|
||||||
|
|
||||||
|
### Disable Windows Error Reporting (WER)/Disable user-mode crash dumps
|
||||||
|
|
||||||
|
1. Sign into [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
||||||
|
|
||||||
1. Sign into the Intune
|
|
||||||
2. Navigate to **Devices** > **Configuration Profiles**
|
2. Navigate to **Devices** > **Configuration Profiles**
|
||||||
|
|
||||||
3. Select **Create profile**
|
3. Select **Create profile**
|
||||||
|
|
||||||
4. Under **Platform**, select **Windows 10 and later**
|
4. Under **Platform**, select **Windows 10 and later**
|
||||||
|
|
||||||
5. Under **Profile type**, select **Settings catalog**, and then select **Create**
|
5. Under **Profile type**, select **Settings catalog**, and then select **Create**
|
||||||
6. On the ****Basics** tab:
|
|
||||||
|
6. In **Basics**:
|
||||||
|
|
||||||
|
1. Next to **Name**, enter **Disable Windows Error Reporting (WER)**
|
||||||
|
2. Next to **Description**, enter a description
|
||||||
|
|
||||||
|
7. Select **Next**
|
||||||
|
|
||||||
|
8. In **Configuration settings**, select **Add settings**
|
||||||
|
|
||||||
|
9. In the **Settings picker** window, under **Browse by category**, expand to **Administrative Templates** > **Windows Components**, and then select **Windows Error Reporting**
|
||||||
|
|
||||||
|
10. When the settings appear under **Setting name**, select **Disable Windows Error Reporting**, and then select the **X** in the top right corner of the **Settings picker** window to close the window
|
||||||
|
|
||||||
|
11. Change **Disable Windows Error Reporting** to **Enabled**, and then select **Next**
|
||||||
|
|
||||||
|
12. In **Scope tags**, configure if necessary and then select **Next**
|
||||||
|
|
||||||
|
13. In **Assignments**:
|
||||||
|
|
||||||
|
1. Under **Included groups**, select **Add groups**
|
||||||
|
2. Select the groups that the disable WER dumps policy should be deployed to
|
||||||
|
3. Select **Select**
|
||||||
|
4. Select **Next**
|
||||||
|
|
||||||
|
14. In **Review + create**, review the configuration to make sure everything is configured correctly, and then select **Create**
|
||||||
|
|
||||||
|
### Disable hibernation
|
||||||
|
|
||||||
|
1. Sign into [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
||||||
|
|
||||||
|
2. Navigate to **Devices** > **Configuration Profiles**
|
||||||
|
|
||||||
|
3. Select **Create profile**
|
||||||
|
|
||||||
|
4. Under **Platform**, select **Windows 10 and later**
|
||||||
|
|
||||||
|
5. Under **Profile type**, select **Settings catalog**, and then select **Create**
|
||||||
|
|
||||||
|
6. In **Basics**:
|
||||||
|
|
||||||
1. Next to **Name**, enter **Disable Hibernation**
|
1. Next to **Name**, enter **Disable Hibernation**
|
||||||
2. Next to **Description**, enter a description
|
2. Next to **Description**, enter a description
|
||||||
|
|
||||||
7. Select **Next**
|
7. Select **Next**
|
||||||
8. On the **Configuration settings** tab, select **Add settings**
|
|
||||||
9. In the **Settings picker** windows, select **Power**
|
8. In **Configuration settings**, select **Add settings**
|
||||||
10. When the settings appear in the lower pane, under **Setting name**, select **Allow Hibernate**, and then select the **X** in the top right corner of the **Settings picker** window to close the window
|
|
||||||
|
9. In the **Settings picker** window, under **Browse by category**, select **Power**
|
||||||
|
|
||||||
|
10. When the settings appear under **Setting name**, select **Allow Hibernate**, and then select the **X** in the top right corner of the **Settings picker** window to close the window
|
||||||
|
|
||||||
11. Change **Allow Hibernate** to **Block**, and then select **Next**
|
11. Change **Allow Hibernate** to **Block**, and then select **Next**
|
||||||
12. On the **Scope tags** tab, configure if necessary and then select **Next**
|
|
||||||
13. On the **Assignments** tab:
|
12. In **Scope tags**, configure if necessary and then select **Next**
|
||||||
|
|
||||||
|
13. In **Assignments**:
|
||||||
|
|
||||||
1. Under **Included groups**, select **Add groups**
|
1. Under **Included groups**, select **Add groups**
|
||||||
2. Select the groups that the hibernation policy should be deployed to
|
2. Select the groups that the disable hibernation policy should be deployed to
|
||||||
3. Select **Select**
|
3. Select **Select**
|
||||||
4. Select **Next**
|
4. Select **Next**
|
||||||
14. On the **Review + create** tab, review the configuration to make sure everything is configured correctly, and then select **Create**
|
|
||||||
|
14. In **Review + create**, review the configuration to make sure everything is configured correctly, and then select **Create**
|
||||||
|
|
||||||
|
### Disable allowing users to select when a password is required when resuming from connected standby
|
||||||
|
|
||||||
|
1. Sign into [Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
||||||
|
|
||||||
|
2. Navigate to **Devices** > **Configuration Profiles**
|
||||||
|
|
||||||
|
3. Select **Create profile**
|
||||||
|
|
||||||
|
4. Under **Platform**, select **Windows 10 and later**
|
||||||
|
|
||||||
|
5. Under **Profile type**, select **Settings catalog**, and then select **Create**
|
||||||
|
|
||||||
|
6. In **Basics**:
|
||||||
|
|
||||||
|
1. Next to **Name**, enter **Disable allowing users to select when a password is required when resuming from connected standby**
|
||||||
|
2. Next to **Description**, enter a description
|
||||||
|
|
||||||
|
7. Select **Next**
|
||||||
|
|
||||||
|
8. In **Configuration settings**, select **Add settings**
|
||||||
|
|
||||||
|
9. In the **Settings picker** window, under **Browse by category**, expand to **Administrative Templates** > **System**, and then select **Logon**
|
||||||
|
|
||||||
|
10. When the settings appear under **Setting name**, select **Allow users to select when a password is required when resuming from connected standby**, and then select the **X** in the top right corner of the **Settings picker** window to close the window
|
||||||
|
|
||||||
|
11. Make sure that **Allow users to select when a password is required when resuming from connected standby** is left at the default of **Disabled**, and then select **Next**
|
||||||
|
|
||||||
|
12. In **Scope tags**, configure if necessary and then select **Next**
|
||||||
|
|
||||||
|
13. In **Assignments**:
|
||||||
|
|
||||||
|
1. Under **Included groups**, select **Add groups**
|
||||||
|
2. Select the groups that the disable Allow users to select when a password is required when resuming from connected standby policy should be deployed to
|
||||||
|
3. Select **Select**
|
||||||
|
4. Select **Next**
|
||||||
|
|
||||||
|
14. In **Review + create**, review the configuration to make sure everything is configured correctly, and then select **Create**
|
||||||
|
|
||||||
## See also
|
## See also
|
||||||
|
|
||||||
- [Personal Data Encryption (PDE)](overview-pde.md)
|
- [Personal Data Encryption (PDE)](overview-pde.md)
|
||||||
- [Personal Data Encryption (PDE) FAQ](faq-pde.yml)
|
- [Personal Data Encryption (PDE) FAQ](faq-pde.yml)
|
||||||
|
|||||||
@ -5,13 +5,16 @@ metadata:
|
|||||||
description: Answers to common questions regarding Personal Data Encryption (PDE).
|
description: Answers to common questions regarding Personal Data Encryption (PDE).
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
ms.reviewer: rafals
|
ms.reviewer: rhonnegowda
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.localizationpriority: medium
|
ms.localizationpriority: medium
|
||||||
ms.date: 09/22/2022
|
ms.date: 12/13/2022
|
||||||
|
|
||||||
|
# Max 5963468 OS 32516487
|
||||||
|
# Max 6946251
|
||||||
|
|
||||||
title: Frequently asked questions for Personal Data Encryption (PDE)
|
title: Frequently asked questions for Personal Data Encryption (PDE)
|
||||||
summary: |
|
summary: |
|
||||||
@ -22,53 +25,58 @@ sections:
|
|||||||
questions:
|
questions:
|
||||||
- question: Can PDE encrypt entire volumes or drives?
|
- question: Can PDE encrypt entire volumes or drives?
|
||||||
answer: |
|
answer: |
|
||||||
No. PDE only encrypts specified files.
|
No. PDE only encrypts specified files and content.
|
||||||
|
|
||||||
- question: Is PDE a replacement for BitLocker?
|
- question: Is PDE a replacement for BitLocker?
|
||||||
answer: |
|
answer: |
|
||||||
No. It's still recommended to encrypt all volumes with BitLocker Drive Encryption for increased security.
|
No. It's still recommended to encrypt all volumes with BitLocker Drive Encryption for increased security.
|
||||||
|
|
||||||
- question: Can an IT admin specify which files should be encrypted?
|
- question: How are files and content protected by PDE selected?
|
||||||
answer: |
|
answer: |
|
||||||
Yes, but it can only be done using the [PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager).
|
[PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager) are used to select which files and content are protected using PDE.
|
||||||
|
|
||||||
- question: Do I need to use OneDrive as my backup provider?
|
- question: Do I need to use OneDrive in Microsoft 365 as my backup provider?
|
||||||
answer: |
|
answer: |
|
||||||
No. PDE doesn't have a requirement for a backup provider including OneDrive. However, backups are strongly recommended in case the keys used by PDE to decrypt files are lost. OneDrive is a recommended backup provider.
|
No. PDE doesn't have a requirement for a backup provider, including OneDrive in Microsoft 365. However, backups are recommended in case the keys used by PDE to protect files are lost. OneDrive in Microsoft 365 is a recommended backup provider.
|
||||||
|
|
||||||
- question: What is the relation between Windows Hello for Business and PDE?
|
- question: What is the relation between Windows Hello for Business and PDE?
|
||||||
answer: |
|
answer: |
|
||||||
During user sign-on, Windows Hello for Business unlocks the keys that PDE uses to decrypt files.
|
During user sign-on, Windows Hello for Business unlocks the keys that PDE uses to protect content.
|
||||||
|
|
||||||
- question: Can a file be encrypted with both PDE and EFS at the same time?
|
- question: Can a file be protected with both PDE and EFS at the same time?
|
||||||
answer: |
|
answer: |
|
||||||
No. PDE and EFS are mutually exclusive.
|
No. PDE and EFS are mutually exclusive.
|
||||||
|
|
||||||
- question: Can PDE encrypted files be accessed after signing on via a Remote Desktop connection (RDP)?
|
- question: Can PDE protected content be accessed after signing on via a Remote Desktop connection (RDP)?
|
||||||
answer: |
|
answer: |
|
||||||
No. Accessing PDE encrypted files over RDP isn't currently supported.
|
No. Accessing PDE protected content over RDP isn't currently supported.
|
||||||
|
|
||||||
- question: Can PDE encrypted files be access via a network share?
|
- question: Can PDE protected content be accessed via a network share?
|
||||||
answer: |
|
answer: |
|
||||||
No. PDE encrypted files can only be accessed after signing on locally to Windows with Windows Hello for Business credentials.
|
No. PDE protected content can only be accessed after signing on locally to Windows with Windows Hello for Business credentials.
|
||||||
|
|
||||||
- question: How can it be determined if a file is encrypted with PDE?
|
- question: How can it be determined if a file is protected with PDE?
|
||||||
answer: |
|
answer: |
|
||||||
Encrypted files will show a padlock on the file's icon. Additionally, `cipher.exe` can be used to show the encryption state of the file.
|
- Files protected with PDE and EFS will both show a padlock on the file's icon. To verify whether a file is protected with PDE vs. EFS:
|
||||||
|
1. In the properties of the file, navigate to **General** > **Advanced**. The option **Encrypt contents to secure data** should be selected.
|
||||||
|
2. Select the **Details** button.
|
||||||
|
3. If the file is protected with PDE, under **Protection status:**, the item **Personal Data Encryption is:** will be marked as **On**.
|
||||||
|
- [`cipher.exe`](/windows-server/administration/windows-commands/cipher) can also be used to show the encryption state of the file.
|
||||||
|
|
||||||
- question: Can users manually encrypt and decrypt files with PDE?
|
- question: Can users manually encrypt and decrypt files with PDE?
|
||||||
answer: |
|
answer: |
|
||||||
Currently users can decrypt files manually but they can't encrypt files manually.
|
Currently users can decrypt files manually but they can't encrypt files manually. For information on how a user can manually decrypt a file, see the section **Disable PDE and decrypt files** in [Personal Data Encryption (PDE)](overview-pde.md).
|
||||||
|
|
||||||
- question: If a user signs into Windows with a password instead of Windows Hello for Business, will they be able to access their PDE encrypted files?
|
- question: If a user signs into Windows with a password instead of Windows Hello for Business, will they be able to access their PDE protected content?
|
||||||
answer: |
|
answer: |
|
||||||
No. The keys used by PDE to decrypt files are protected by Windows Hello for Business credentials and will only be unlocked when signing on with Windows Hello for Business PIN or biometrics.
|
No. The keys used by PDE to protect content are protected by Windows Hello for Business credentials and will only be unlocked when signing on with Windows Hello for Business PIN or biometrics.
|
||||||
|
|
||||||
- question: What encryption method and strength does PDE use?
|
- question: What encryption method and strength does PDE use?
|
||||||
answer: |
|
answer: |
|
||||||
PDE uses AES-CBC with a 256-bit key to encrypt files
|
PDE uses AES-CBC with a 256-bit key to encrypt content.
|
||||||
|
|
||||||
additionalContent: |
|
additionalContent: |
|
||||||
## See also
|
## See also
|
||||||
- [Personal Data Encryption (PDE)](overview-pde.md)
|
- [Personal Data Encryption (PDE)](overview-pde.md)
|
||||||
- [Configure Personal Data Encryption (PDE) polices in Intune](configure-pde-in-intune.md)
|
- [Configure Personal Data Encryption (PDE) polices in Intune](configure-pde-in-intune.md)
|
||||||
|
|
||||||
|
|||||||
@ -4,24 +4,25 @@ description: Personal Data Encryption (PDE) description include file
|
|||||||
|
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
ms.reviewer: rafals
|
ms.reviewer: rhonnegowda
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.topic: how-to
|
ms.topic: how-to
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.localizationpriority: medium
|
ms.localizationpriority: medium
|
||||||
ms.date: 09/22/2022
|
ms.date: 12/13/2022
|
||||||
---
|
---
|
||||||
|
|
||||||
<!-- Max 5963468 OS 32516487 -->
|
<!-- Max 5963468 OS 32516487 -->
|
||||||
|
<!-- Max 6946251 -->
|
||||||
|
|
||||||
Personal data encryption (PDE) is a security feature introduced in Windows 11, version 22H2 that provides additional encryption features to Windows. PDE differs from BitLocker in that it encrypts individual files instead of whole volumes and disks. PDE occurs in addition to other encryption methods such as BitLocker.
|
Personal data encryption (PDE) is a security feature introduced in Windows 11, version 22H2 that provides additional encryption features to Windows. PDE differs from BitLocker in that it encrypts individual files and content instead of whole volumes and disks. PDE occurs in addition to other encryption methods such as BitLocker.
|
||||||
|
|
||||||
PDE utilizes Windows Hello for Business to link data encryption keys with user credentials. This feature can minimize the number of credentials the user has to remember to gain access to files. For example, when using BitLocker with PIN, a user would need to authenticate twice - once with the BitLocker PIN and a second time with Windows credentials. This requirement requires users to remember two different credentials. With PDE, users only need to enter one set of credentials via Windows Hello for Business.
|
PDE utilizes Windows Hello for Business to link data encryption keys with user credentials. This feature can minimize the number of credentials the user has to remember to gain access to content. For example, when using BitLocker with PIN, a user would need to authenticate twice - once with the BitLocker PIN and a second time with Windows credentials. This requirement requires users to remember two different credentials. With PDE, users only need to enter one set of credentials via Windows Hello for Business.
|
||||||
|
|
||||||
PDE is also accessibility friendly. For example, The BitLocker PIN entry screen doesn't have accessibility options. PDE however uses Windows Hello for Business, which does have accessibility features.
|
Because PDE utilizes Windows Hello for Business, PDE is also accessibility friendly due to the accessibility features available when using Windows Hello for Business.
|
||||||
|
|
||||||
Unlike BitLocker that releases data encryption keys at boot, PDE doesn't release data encryption keys until a user signs in using Windows Hello for Business. Users will only be able to access their PDE encrypted files once they've signed into Windows using Windows Hello for Business. Additionally, PDE has the ability to also discard the encryption keys when the device is locked.
|
Unlike BitLocker that releases data encryption keys at boot, PDE doesn't release data encryption keys until a user signs in using Windows Hello for Business. Users will only be able to access their PDE protected content once they've signed into Windows using Windows Hello for Business. Additionally, PDE has the ability to also discard the encryption keys when the device is locked.
|
||||||
|
|
||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> PDE is currently only available to developers via [PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager). There is no user interface in Windows to either enable PDE or encrypt files via PDE. Also, although there is an MDM policy that can enable PDE, there are no MDM policies that can be used to encrypt files via PDE.
|
> PDE can be enabled using MDM policies. The content to be protected by PDE can be specified using [PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager). There is no user interface in Windows to either enable PDE or protect content using PDE.
|
||||||
|
|||||||
@ -3,75 +3,123 @@ title: Personal Data Encryption (PDE)
|
|||||||
description: Personal Data Encryption unlocks user encrypted files at user sign-in instead of at boot.
|
description: Personal Data Encryption unlocks user encrypted files at user sign-in instead of at boot.
|
||||||
author: frankroj
|
author: frankroj
|
||||||
ms.author: frankroj
|
ms.author: frankroj
|
||||||
ms.reviewer: rafals
|
ms.reviewer: rhonnegowda
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.topic: how-to
|
ms.topic: how-to
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: itpro-security
|
ms.technology: itpro-security
|
||||||
ms.localizationpriority: medium
|
ms.localizationpriority: medium
|
||||||
ms.date: 09/22/2022
|
ms.date: 12/13/2022
|
||||||
---
|
---
|
||||||
|
|
||||||
<!-- Max 5963468 OS 32516487 -->
|
<!-- Max 5963468 OS 32516487 -->
|
||||||
|
<!-- Max 6946251 -->
|
||||||
|
|
||||||
# Personal Data Encryption (PDE)
|
# Personal Data Encryption (PDE)
|
||||||
|
|
||||||
(*Applies to: Windows 11, version 22H2 and later Enterprise and Education editions*)
|
**Applies to:**
|
||||||
|
|
||||||
|
- Windows 11, version 22H2 and later Enterprise and Education editions
|
||||||
|
|
||||||
[!INCLUDE [Personal Data Encryption (PDE) description](includes/pde-description.md)]
|
[!INCLUDE [Personal Data Encryption (PDE) description](includes/pde-description.md)]
|
||||||
|
|
||||||
## Prerequisites
|
## Prerequisites
|
||||||
|
|
||||||
### **Required**
|
### Required
|
||||||
- [Azure AD joined device](/azure/active-directory/devices/concept-azure-ad-join)
|
|
||||||
- [Windows Hello for Business](../../identity-protection/hello-for-business/hello-overview.md)
|
|
||||||
- Windows 11, version 22H2 and later Enterprise and Education editions
|
|
||||||
|
|
||||||
### **Not supported with PDE**
|
- [Azure AD joined device](/azure/active-directory/devices/concept-azure-ad-join)
|
||||||
- [FIDO/security key authentication](../../identity-protection/hello-for-business/microsoft-compatible-security-key.md)
|
- [Windows Hello for Business](../../identity-protection/hello-for-business/hello-overview.md)
|
||||||
- [Winlogon automatic restart sign-on (ARSO)](/windows-server/identity/ad-ds/manage/component-updates/winlogon-automatic-restart-sign-on--arso-)
|
- Windows 11, version 22H2 and later Enterprise and Education editions
|
||||||
- For information on disabling ARSO via Intune, see [Disable Winlogon automatic restart sign-on (ARSO)](configure-pde-in-intune.md#disable-winlogon-automatic-restart-sign-on-arso)).
|
|
||||||
- [Windows Information Protection (WIP)](../windows-information-protection/protect-enterprise-data-using-wip.md)
|
|
||||||
- [Hybrid Azure AD joined devices](/azure/active-directory/devices/concept-azure-ad-join-hybrid)
|
|
||||||
- Remote Desktop connections
|
|
||||||
|
|
||||||
### **Highly recommended**
|
### Not supported with PDE
|
||||||
- [BitLocker Drive Encryption](../bitlocker/bitlocker-overview.md) enabled
|
|
||||||
- Although PDE will work without BitLocker, it's recommended to also enable BitLocker. PDE is meant to supplement BitLocker and not replace it.
|
- [FIDO/security key authentication](/azure/active-directory/authentication/howto-authentication-passwordless-security-key)
|
||||||
- Backup solution such as [OneDrive](/onedrive/onedrive)
|
- [Winlogon automatic restart sign-on (ARSO)](/windows-server/identity/ad-ds/manage/component-updates/winlogon-automatic-restart-sign-on--arso-)
|
||||||
- In certain scenarios such as TPM resets or destructive PIN resets, the keys used by PDE to decrypt files can be lost. In such scenarios, any file encrypted with PDE will no longer be accessible. The only way to recover such files would be from backup.
|
- For information on disabling ARSO via Intune, see [Disable Winlogon automatic restart sign-on (ARSO)](configure-pde-in-intune.md#disable-winlogon-automatic-restart-sign-on-arso)).
|
||||||
- [Windows Hello for Business PIN reset service](../../identity-protection/hello-for-business/hello-feature-pin-reset.md)
|
- [Windows Information Protection (WIP)](../windows-information-protection/protect-enterprise-data-using-wip.md)
|
||||||
- Destructive PIN resets will cause keys used by PDE to decrypt files to be lost. The destructive PIN reset will make any file encrypted with PDE no longer accessible after a destructive PIN reset. Files encrypted with PDE will need to be recovered from a backup after a destructive PIN reset. For this reason Windows Hello for Business PIN reset service is recommended since it provides non-destructive PIN resets.
|
- [Hybrid Azure AD joined devices](/azure/active-directory/devices/concept-azure-ad-join-hybrid)
|
||||||
- [Windows Hello Enhanced Sign-in Security](/windows-hardware/design/device-experiences/windows-hello-enhanced-sign-in-security)
|
- Remote Desktop connections
|
||||||
- Provides additional security when authenticating with Windows Hello for Business via biometrics or PIN
|
|
||||||
- [Kernel and user mode crash dumps disabled](/windows/client-management/mdm/policy-csp-memorydump)
|
### Security hardening recommendations
|
||||||
- Crash dumps can potentially cause the keys used by PDE decrypt files to be exposed. For greatest security, disable kernel and user mode crash dumps. For information on disabling crash dumbs via Intune, see [Disable crash dumps](configure-pde-in-intune.md#disable-crash-dumps).
|
|
||||||
- [Hibernation disabled](/windows/client-management/mdm/policy-csp-power#power-allowhibernate)
|
- [Kernel-mode crash dumps and live dumps disabled](/windows/client-management/mdm/policy-csp-memorydump#memorydump-policies)
|
||||||
- Hibernation files can potentially cause the keys used by PDE to decrypt files to be exposed. For greatest security, disable hibernation. For information on disabling crash dumbs via Intune, see [Disable hibernation](configure-pde-in-intune.md#disable-hibernation).
|
|
||||||
|
Kernel-mode crash dumps and live dumps can potentially cause the keys used by PDE to protect content to be exposed. For greatest security, disable kernel-mode crash dumps and live dumps. For information on disabling crash dumps and live dumps via Intune, see [Disable kernel-mode crash dumps and live dumps](configure-pde-in-intune.md#disable-kernel-mode-crash-dumps-and-live-dumps).
|
||||||
|
|
||||||
|
- [Windows Error Reporting (WER) disabled/User-mode crash dumps disabled](/windows/client-management/mdm/policy-csp-errorreporting#errorreporting-disablewindowserrorreporting)
|
||||||
|
|
||||||
|
Disabling Windows Error Reporting prevents user-mode crash dumps. User-mode crash dumps can potentially cause the keys used by PDE to protect content to be exposed. For greatest security, disable user-mode crash dumps. For more information on disabling crash dumps via Intune, see [Disable Windows Error Reporting (WER)/Disable user-mode crash dumps](configure-pde-in-intune.md#disable-windows-error-reporting-werdisable-user-mode-crash-dumps).
|
||||||
|
|
||||||
|
- [Hibernation disabled](/windows/client-management/mdm/policy-csp-power#power-allowhibernate)
|
||||||
|
|
||||||
|
Hibernation files can potentially cause the keys used by PDE to protect content to be exposed. For greatest security, disable hibernation. For more information on disabling crash dumps via Intune, see [Disable hibernation](configure-pde-in-intune.md#disable-hibernation).
|
||||||
|
|
||||||
|
- [Allowing users to select when a password is required when resuming from connected standby disabled](/windows/client-management/mdm/policy-csp-admx-credentialproviders#admx-credentialproviders-allowdomaindelaylock)
|
||||||
|
|
||||||
|
When this policy isn't configured, the outcome between on-premises Active Directory joined devices and workgroup devices, including native Azure Active Directory joined devices, is different:
|
||||||
|
|
||||||
|
- On-premises Active Directory joined devices:
|
||||||
|
|
||||||
|
- A user can't change the amount of time after the device´s screen turns off before a password is required when waking the device.
|
||||||
|
|
||||||
|
- A password is required immediately after the screen turns off.
|
||||||
|
|
||||||
|
The above is the desired outcome, but PDE isn't supported with on-premises Active Directory joined devices.
|
||||||
|
|
||||||
|
- Workgroup devices, including native Azure AD joined devices:
|
||||||
|
|
||||||
|
- A user on a Connected Standby device can change the amount of time after the device´s screen turns off before a password is required to wake the device.
|
||||||
|
|
||||||
|
- During the time when the screen turns off but a password isn't required, the keys used by PDE to protect content could potentially be exposed. This outcome isn't a desired outcome.
|
||||||
|
|
||||||
|
Because of this undesired outcome, it's recommended to explicitly disable this policy on native Azure AD joined devices instead of leaving it at the default of not configured.
|
||||||
|
|
||||||
|
For information on disabling this policy via Intune, see [Disable allowing users to select when a password is required when resuming from connected standby](configure-pde-in-intune.md#disable-allowing-users-to-select-when-a-password-is-required-when-resuming-from-connected-standby).
|
||||||
|
|
||||||
|
### Highly recommended
|
||||||
|
|
||||||
|
- [BitLocker Drive Encryption](../bitlocker/bitlocker-overview.md) enabled
|
||||||
|
|
||||||
|
Although PDE will work without BitLocker, it's recommended to also enable BitLocker. PDE is meant to work alongside BitLocker for increased security. PDE isn't a replacement for BitLocker.
|
||||||
|
|
||||||
|
- Backup solution such as [OneDrive in Microsoft 365](/sharepoint/onedrive-overview)
|
||||||
|
|
||||||
|
In certain scenarios such as TPM resets or destructive PIN resets, the keys used by PDE to protect content will be lost. In such scenarios, any content protected with PDE will no longer be accessible. The only way to recover such content would be from backup.
|
||||||
|
|
||||||
|
- [Windows Hello for Business PIN reset service](../../identity-protection/hello-for-business/hello-feature-pin-reset.md)
|
||||||
|
|
||||||
|
Destructive PIN resets will cause keys used by PDE to protect content to be lost. The destructive PIN reset will make any content protected with PDE no longer accessible after a destructive PIN reset. Content protected with PDE will need to be recovered from a backup after a destructive PIN reset. For this reason Windows Hello for Business PIN reset service is recommended since it provides non-destructive PIN resets.
|
||||||
|
|
||||||
|
- [Windows Hello Enhanced Sign-in Security](/windows-hardware/design/device-experiences/windows-hello-enhanced-sign-in-security)
|
||||||
|
|
||||||
|
Provides additional security when authenticating with Windows Hello for Business via biometrics or PIN
|
||||||
|
|
||||||
## PDE protection levels
|
## PDE protection levels
|
||||||
|
|
||||||
PDE uses AES-CBC with a 256-bit key to encrypt files and offers two levels of protection. The level of protection is determined based on the organizational needs. These levels can be set via the [PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager).
|
PDE uses AES-CBC with a 256-bit key to protect content and offers two levels of protection. The level of protection is determined based on the organizational needs. These levels can be set via the [PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager).
|
||||||
|
|
||||||
| Item | Level 1 | Level 2 |
|
| Item | Level 1 | Level 2 |
|
||||||
|---|---|---|
|
|---|---|---|
|
||||||
| Data is accessible when user is signed in | Yes | Yes |
|
| PDE protected data accessible when user has signed in via Windows Hello for Business | Yes | Yes |
|
||||||
| Data is accessible when user has locked their device | Yes | No |
|
| PDE protected data is accessible at Windows lock screen | Yes | Data is accessible for one minute after lock, then it's no longer available |
|
||||||
| Data is accessible after user signs out | No | No |
|
| PDE protected data is accessible after user signs out of Windows | No | No |
|
||||||
| Data is accessible when device is shut down | No | No |
|
| PDE protected data is accessible when device is shut down | No | No |
|
||||||
| Decryption keys discarded | After user signs out | After user locks device or signs out |
|
| PDE protected data is accessible via UNC paths | No | No |
|
||||||
|
| PDE protected data is accessible when signing with Windows password instead of Windows Hello for Business | No | No |
|
||||||
|
| PDE protected data is accessible via Remote Desktop session | No | No |
|
||||||
|
| Decryption keys used by PDE discarded | After user signs out of Windows | One minute after Windows lock screen is engaged or after user signs out of Windows |
|
||||||
|
|
||||||
## PDE encrypted files accessibility
|
## PDE protected content accessibility
|
||||||
|
|
||||||
When a file is encrypted with PDE, its icon will show a padlock. If the user hasn't signed in locally with Windows Hello for Business or an unauthorized user attempts to access a PDE encrypted file, they'll be denied access to the file.
|
When a file is protected with PDE, its icon will show a padlock. If the user hasn't signed in locally with Windows Hello for Business or an unauthorized user attempts to access PDE protected content, they'll be denied access to the content.
|
||||||
|
|
||||||
Scenarios where a user will be denied access to a PDE encrypted file include:
|
Scenarios where a user will be denied access to PDE protected content include:
|
||||||
|
|
||||||
- User has signed into Windows via a password instead of signing in with Windows Hello for Business biometric or PIN.
|
- User has signed into Windows via a password instead of signing in with Windows Hello for Business biometric or PIN.
|
||||||
- If specified via level 2 protection, when the device is locked.
|
- If protected via level 2 protection, when the device is locked.
|
||||||
- When trying to access files on the device remotely. For example, UNC network paths.
|
- When trying to access content on the device remotely. For example, UNC network paths.
|
||||||
- Remote Desktop sessions.
|
- Remote Desktop sessions.
|
||||||
- Other users on the device who aren't owners of the file, even if they're signed in via Windows Hello for Business and have permissions to navigate to the PDE encrypted files.
|
- Other users on the device who aren't owners of the content, even if they're signed in via Windows Hello for Business and have permissions to navigate to the PDE protected content.
|
||||||
|
|
||||||
## How to enable PDE
|
## How to enable PDE
|
||||||
|
|
||||||
@ -85,55 +133,83 @@ To enable PDE on devices, push an MDM policy to the devices with the following p
|
|||||||
There's also a [PDE CSP](/windows/client-management/mdm/personaldataencryption-csp) available for MDM solutions that support it.
|
There's also a [PDE CSP](/windows/client-management/mdm/personaldataencryption-csp) available for MDM solutions that support it.
|
||||||
|
|
||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> Enabling the PDE policy on devices only enables the PDE feature. It does not encrypt any files. To encrypt files, use the [PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager) to create custom applications and scripts to specify which files to encrypt and at what level to encrypt the files. Additionally, files will not encrypt via the APIs until this policy has been enabled.
|
> Enabling the PDE policy on devices only enables the PDE feature. It does not protect any content. To protect content via PDE, use the [PDE APIs](/uwp/api/windows.security.dataprotection.userdataprotectionmanager). The PDE APIs can be used to create custom applications and scripts to specify which content to protect and at what level to protect the content. Additionally, the PDE APIs can't be used to protect content until the PDE policy has been enabled.
|
||||||
|
|
||||||
For information on enabling PDE via Intune, see [Enable Personal Data Encryption (PDE)](configure-pde-in-intune.md#enable-personal-data-encryption-pde).
|
For information on enabling PDE via Intune, see [Enable Personal Data Encryption (PDE)](configure-pde-in-intune.md#enable-personal-data-encryption-pde).
|
||||||
|
|
||||||
## Differences between PDE and BitLocker
|
## Differences between PDE and BitLocker
|
||||||
|
|
||||||
|
PDE is meant to work alongside BitLocker. PDE isn't a replacement for BitLocker, nor is BitLocker a replacement for PDE. Using both features together provides better security than using either BitLocker or PDE alone. However there are differences between BitLocker and PDE and how they work. These differences are why using them together offers better security.
|
||||||
|
|
||||||
| Item | PDE | BitLocker |
|
| Item | PDE | BitLocker |
|
||||||
|--|--|--|
|
|--|--|--|
|
||||||
| Release of key | At user sign-in via Windows Hello for Business | At boot |
|
| Release of decryption key | At user sign-in via Windows Hello for Business | At boot |
|
||||||
| Keys discarded | At user sign-out | At reboot |
|
| Decryption keys discarded | When user signs out of Windows or one minute after Windows lock screen is engaged | At reboot |
|
||||||
| Files encrypted | Individual specified files | Entire volume/drive |
|
| Files protected | Individual specified files | Entire volume/drive |
|
||||||
| Authentication to access encrypted file | Windows Hello for Business | When BitLocker with PIN is enabled, BitLocker PIN plus Windows sign in |
|
| Authentication to access protected content | Windows Hello for Business | When BitLocker with TPM + PIN is enabled, BitLocker PIN plus Windows sign-in |
|
||||||
| Accessibility | Windows Hello for Business is accessibility friendly | BitLocker with PIN doesn't have accessibility features |
|
|
||||||
|
|
||||||
## Differences between PDE and EFS
|
## Differences between PDE and EFS
|
||||||
|
|
||||||
The main difference between encrypting files with PDE instead of EFS is the method they use to encrypt the file. PDE uses Windows Hello for Business to secure the keys to decrypt the files. EFS uses certificates to secure and encrypt the files.
|
The main difference between protecting files with PDE instead of EFS is the method they use to protect the file. PDE uses Windows Hello for Business to secure the keys that protect the files. EFS uses certificates to secure and protect the files.
|
||||||
|
|
||||||
To see if a file is encrypted with PDE or EFS:
|
To see if a file is protected with PDE or with EFS:
|
||||||
|
|
||||||
1. Open the properties of the file
|
1. Open the properties of the file
|
||||||
2. Under the **General** tab, select **Advanced...**
|
2. Under the **General** tab, select **Advanced...**
|
||||||
3. In the **Advanced Attributes** windows, select **Details**
|
3. In the **Advanced Attributes** windows, select **Details**
|
||||||
|
|
||||||
For PDE encrypted files, under **Protection status:** there will be an item listed as **Personal Data Encryption is:** and it will have the attribute of **On**.
|
For PDE protected files, under **Protection status:** there will be an item listed as **Personal Data Encryption is:** and it will have the attribute of **On**.
|
||||||
|
|
||||||
For EFS encrypted files, under **Users who can access this file:**, there will be a **Certificate thumbprint** next to the users with access to the file. There will also be a section at the bottom labeled **Recovery certificates for this file as defined by recovery policy:**.
|
For EFS protected files, under **Users who can access this file:**, there will be a **Certificate thumbprint** next to the users with access to the file. There will also be a section at the bottom labeled **Recovery certificates for this file as defined by recovery policy:**.
|
||||||
|
|
||||||
Encryption information including what encryption method is being used can be obtained with the command line `cipher.exe /c` command.
|
Encryption information including what encryption method is being used to protect the file can be obtained with the [cipher.exe /c](/windows-server/administration/windows-commands/cipher) command.
|
||||||
|
|
||||||
## Disable PDE and decrypt files
|
## Disable PDE and decrypt content
|
||||||
|
|
||||||
Currently there's no method to disable PDE via MDM policy. However, in certain scenarios PDE encrypted files can be decrypted using `cipher.exe` using the following steps:
|
Once PDE is enabled, it isn't recommended to disable it. However if PDE does need to be disabled, it can be done so via the MDM policy described in the section [How to enable PDE](#how-to-enable-pde). The value of the OMA-URI needs to be changed from **`1`** to **`0`** as follows:
|
||||||
|
|
||||||
|
- Name: **Personal Data Encryption**
|
||||||
|
- OMA-URI: **./User/Vendor/MSFT/PDE/EnablePersonalDataEncryption**
|
||||||
|
- Data type: **Integer**
|
||||||
|
- Value: **0**
|
||||||
|
|
||||||
|
Disabling PDE doesn't decrypt any PDE protected content. It only prevents the PDE API from being able to protect any additional content. PDE protected files can be manually decrypted using the following steps:
|
||||||
|
|
||||||
1. Open the properties of the file
|
1. Open the properties of the file
|
||||||
2. Under the **General** tab, select **Advanced...**
|
2. Under the **General** tab, select **Advanced...**
|
||||||
3. Uncheck the option **Encrypt contents to secure data**
|
3. Uncheck the option **Encrypt contents to secure data**
|
||||||
4. Select **OK**, and then **OK** again
|
4. Select **OK**, and then **OK** again
|
||||||
|
|
||||||
> [!Important]
|
PDE protected files can also be decrypted using [cipher.exe](/windows-server/administration/windows-commands/cipher). Using `cipher.exe` can be helpful to decrypt files in the following scenarios:
|
||||||
> Once a user selects to manually decrypt a file, they will not be able to manually encrypt the file again.
|
|
||||||
|
- Decrypting a large number of files on a device
|
||||||
|
- Decrypting files on a large number of devices.
|
||||||
|
|
||||||
|
To decrypt files on a device using `cipher.exe`:
|
||||||
|
|
||||||
|
- Decrypt all files under a directory including subdirectories:
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
cipher.exe /d /s:<path_to_directory>
|
||||||
|
```
|
||||||
|
|
||||||
|
- Decrypt a single file or all of the files in the specified directory, but not any subdirectories:
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
cipher.exe /d <path_to_file_or_directory>
|
||||||
|
```
|
||||||
|
|
||||||
|
> [!IMPORTANT]
|
||||||
|
> Once a user selects to manually decrypt a file, the user will not be able to manually protect the file again using PDE.
|
||||||
|
|
||||||
## Windows out of box applications that support PDE
|
## Windows out of box applications that support PDE
|
||||||
|
|
||||||
Certain Windows applications support PDE out of the box. If PDE is enabled on a device, these applications will utilize PDE.
|
Certain Windows applications support PDE out of the box. If PDE is enabled on a device, these applications will utilize PDE.
|
||||||
|
|
||||||
- Mail
|
- Mail
|
||||||
- Supports encrypting both email bodies and attachments
|
- Supports protecting both email bodies and attachments
|
||||||
|
|
||||||
## See also
|
## See also
|
||||||
|
|
||||||
- [Personal Data Encryption (PDE) FAQ](faq-pde.yml)
|
- [Personal Data Encryption (PDE) FAQ](faq-pde.yml)
|
||||||
- [Configure Personal Data Encryption (PDE) polices in Intune](configure-pde-in-intune.md)
|
- [Configure Personal Data Encryption (PDE) polices in Intune](configure-pde-in-intune.md)
|
||||||
|
|||||||
@ -20,8 +20,9 @@ ms.date: 12/31/2017
|
|||||||
**Applies to**
|
**Applies to**
|
||||||
- Windows 11
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
- Windows Server 2016
|
- Windows Server 2022
|
||||||
- Windows Server 2019
|
- Windows Server 2019
|
||||||
|
- Windows Server 2016
|
||||||
|
|
||||||
This topic for the IT professional describes the Trusted Platform Module (TPM) and how Windows uses it for access control and authentication.
|
This topic for the IT professional describes the Trusted Platform Module (TPM) and how Windows uses it for access control and authentication.
|
||||||
|
|
||||||
@ -74,15 +75,14 @@ Some things that you can check on the device are:
|
|||||||
- Is SecureBoot supported and enabled?
|
- Is SecureBoot supported and enabled?
|
||||||
|
|
||||||
> [!NOTE]
|
> [!NOTE]
|
||||||
> Windows 11, Windows 10, Windows Server 2016, and Windows Server 2019 support Device Health Attestation with TPM 2.0. Support for TPM 1.2 was added beginning with Windows version 1607 (RS1). TPM 2.0 requires UEFI firmware. A computer with legacy BIOS and TPM 2.0 won't work as expected.
|
> Windows 11, Windows 10, Windows Server 2016, and Windows Server 2019 support Device Health Attestation with TPM 2.0. Support for TPM 1.2 was added beginning with Windows 10, version 1607. TPM 2.0 requires UEFI firmware. A computer with legacy BIOS and TPM 2.0 won't work as expected.
|
||||||
|
|
||||||
## Supported versions for device health attestation
|
## Supported versions for device health attestation
|
||||||
|
|
||||||
| TPM version | Windows 11 | Windows 10 | Windows Server 2016 | Windows Server 2019 |
|
| TPM version | Windows 11 | Windows 10 | Windows Server 2022 | Windows Server 2019 | Windows Server 2016 |
|
||||||
|-------------|-------------|-------------|---------------------|---------------------|
|
|-------------|-------------|-------------|---------------------|---------------------|---------------------|
|
||||||
| TPM 1.2 | | >= ver 1607 | >= ver 1607 | Yes |
|
| TPM 1.2 | | >= ver 1607 | | Yes | >= ver 1607 |
|
||||||
| TPM 2.0 | Yes | Yes | Yes | Yes |
|
| TPM 2.0 | **Yes** | **Yes** | **Yes** | **Yes** | **Yes** |
|
||||||
|
|
||||||
|
|
||||||
## Related topics
|
## Related topics
|
||||||
|
|
||||||
|
|||||||
@ -3,7 +3,6 @@ title: Windows security foundations
|
|||||||
description: Get an overview of security foundations, including the security development lifecycle, common criteria, and the bug bounty program.
|
description: Get an overview of security foundations, including the security development lifecycle, common criteria, and the bug bounty program.
|
||||||
ms.reviewer:
|
ms.reviewer:
|
||||||
ms.topic: article
|
ms.topic: article
|
||||||
manager: aaroncz
|
|
||||||
ms.author: paoloma
|
ms.author: paoloma
|
||||||
author: paolomatarazzo
|
author: paolomatarazzo
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
@ -15,9 +14,9 @@ ms.date: 12/31/2017
|
|||||||
|
|
||||||
Microsoft is committed to continuously invest in improving our software development process, building highly secure-by-design software, and addressing security compliance requirements. At Microsoft, we embed security and privacy considerations from the earliest life-cycle phases of all our software development processes. We build in security from the ground for powerful defense in today’s threat environment.
|
Microsoft is committed to continuously invest in improving our software development process, building highly secure-by-design software, and addressing security compliance requirements. At Microsoft, we embed security and privacy considerations from the earliest life-cycle phases of all our software development processes. We build in security from the ground for powerful defense in today’s threat environment.
|
||||||
|
|
||||||
Our strong security foundation uses Microsoft Security Development Lifecycle (SDL) Bug Bounty, support for product security standards and certifications, and Azure Code signing. As a result, we improve security by producing software with fewer defects and vulnerabilities instead of relying on applying updates after vulnerabilities have been identified.
|
Our strong security foundation uses Microsoft Security Development Lifecycle (SDL) Bug Bounty, support for product security standards and certifications, and Azure Code signing. As a result, we improve security by producing software with fewer defects and vulnerabilities instead of relying on applying updates after vulnerabilities have been identified.
|
||||||
|
|
||||||
Use the links in the following table to learn more about the security foundations:<br/><br/>
|
Use the links in the following table to learn more about the security foundations:
|
||||||
|
|
||||||
| Concept | Description |
|
| Concept | Description |
|
||||||
|:---|:---|
|
|:---|:---|
|
||||||
@ -25,6 +24,3 @@ Use the links in the following table to learn more about the security foundation
|
|||||||
| Common Criteria Certifications | Microsoft supports the Common Criteria certification program, ensures that products incorporate the features and functions required by relevant Common Criteria Protection Profiles, and completes Common Criteria certifications of Microsoft Windows products. <br/><br/>Learn more about [Common Criteria Certifications](threat-protection/windows-platform-common-criteria.md). |
|
| Common Criteria Certifications | Microsoft supports the Common Criteria certification program, ensures that products incorporate the features and functions required by relevant Common Criteria Protection Profiles, and completes Common Criteria certifications of Microsoft Windows products. <br/><br/>Learn more about [Common Criteria Certifications](threat-protection/windows-platform-common-criteria.md). |
|
||||||
| Microsoft Security Development Lifecycle | The Security Development Lifecycle (SDL) is a security assurance process that is focused on software development. The SDL has played a critical role in embedding security and privacy in software and culture at Microsoft.<br/><br/>Learn more about [Microsoft SDL](threat-protection/msft-security-dev-lifecycle.md).|
|
| Microsoft Security Development Lifecycle | The Security Development Lifecycle (SDL) is a security assurance process that is focused on software development. The SDL has played a critical role in embedding security and privacy in software and culture at Microsoft.<br/><br/>Learn more about [Microsoft SDL](threat-protection/msft-security-dev-lifecycle.md).|
|
||||||
| Microsoft Bug Bounty Program | If you find a vulnerability in a Microsoft product, service, or device, we want to hear from you! If your vulnerability report affects a product or service that is within scope of one of our bounty programs below, you could receive a bounty award according to the program descriptions.<br/><br/>Learn more about the [Microsoft Bug Bounty Program](https://www.microsoft.com/en-us/msrc/bounty?rtc=1). |
|
| Microsoft Bug Bounty Program | If you find a vulnerability in a Microsoft product, service, or device, we want to hear from you! If your vulnerability report affects a product or service that is within scope of one of our bounty programs below, you could receive a bounty award according to the program descriptions.<br/><br/>Learn more about the [Microsoft Bug Bounty Program](https://www.microsoft.com/en-us/msrc/bounty?rtc=1). |
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
@ -171,4 +171,8 @@ Resource SACLs are also useful for diagnostic scenarios. For example, administra
|
|||||||
|
|
||||||
This category includes the following subcategories:
|
This category includes the following subcategories:
|
||||||
- [File System (Global Object Access Auditing)](file-system-global-object-access-auditing.md)
|
- [File System (Global Object Access Auditing)](file-system-global-object-access-auditing.md)
|
||||||
- [Registry (Global Object Access Auditing)](registry-global-object-access-auditing.md)
|
- [Registry (Global Object Access Auditing)](registry-global-object-access-auditing.md)
|
||||||
|
|
||||||
|
## Related topics
|
||||||
|
|
||||||
|
- [Basic security audit policy settings](basic-security-audit-policy-settings.md)
|
||||||
|
|||||||
@ -1,17 +1,14 @@
|
|||||||
### YamlMime:FAQ
|
### YamlMime:FAQ
|
||||||
metadata:
|
metadata:
|
||||||
title: Advanced security auditing FAQ (Windows 10)
|
title: Advanced security auditing FAQ
|
||||||
description: This article lists common questions and answers about understanding, deploying, and managing security audit policies.
|
description: This article lists common questions and answers about understanding, deploying, and managing security audit policies.
|
||||||
ms.prod: windows-client
|
ms.prod: windows-client
|
||||||
ms.technology: mde
|
author: vinaypamnani-msft
|
||||||
ms.localizationpriority: none
|
ms.author: vinpa
|
||||||
author: dansimp
|
|
||||||
ms.author: dansimp
|
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.reviewer:
|
|
||||||
ms.collection: M365-security-compliance
|
|
||||||
ms.topic: faq
|
ms.topic: faq
|
||||||
ms.date: 05/24/2022
|
ms.date: 05/24/2022
|
||||||
|
ms.technology: itpro-security
|
||||||
|
|
||||||
title: Advanced security auditing FAQ
|
title: Advanced security auditing FAQ
|
||||||
|
|
||||||
|
|||||||
@ -38,6 +38,6 @@ Basic security audit policy settings are found under Computer Configuration\\Win
|
|||||||
|
|
||||||
## Related topics
|
## Related topics
|
||||||
|
|
||||||
- [Basic security audit policy settings](basic-security-audit-policy-settings.md)
|
- [Advanced security audit policy settings](advanced-security-audit-policy-settings.md)
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
@ -158,15 +158,15 @@ This event generates only if Success auditing is enabled for the [Audit Handle M
|
|||||||
|
|
||||||
**Access Request Information:**
|
**Access Request Information:**
|
||||||
|
|
||||||
- **Transaction ID** \[Type = GUID\]: unique GUID of the transaction. This field can help you correlate this event with other events that might contain the same the **Transaction ID**, such as “[4660](event-4660.md)(S): An object was deleted.”
|
- **Transaction ID** \[Type = GUID\]: unique GUID of the transaction. This field can help you correlate this event with other events that might contain the same **Transaction ID**, such as “[4660](event-4660.md)(S): An object was deleted.”
|
||||||
|
|
||||||
This parameter might not be captured in the event, and in that case appears as “{00000000-0000-0000-0000-000000000000}”.
|
This parameter might not be captured in the event, and in that case appears as “{00000000-0000-0000-0000-000000000000}”.
|
||||||
|
|
||||||
> **Note** **GUID** is an acronym for 'Globally Unique Identifier'. It is a 128-bit integer number used to identify resources, activities or instances.
|
> **Note** **GUID** is an acronym for 'Globally Unique Identifier'. It is a 128-bit integer number used to identify resources, activities or instances.
|
||||||
|
|
||||||
- **Accesses** \[Type = UnicodeString\]: the list of access rights which were requested by **Subject\\Security ID**. These access rights depend on **Object Type**. See “Table 13. File access codes.” for more information about file access rights. For information about SAM object access right use <https://technet.microsoft.com/> or other informational resources.
|
- **Accesses** \[Type = UnicodeString\]: the list of access rights which were requested by **Subject\\Security ID**. These access rights depend on **Object Type**. For more information about file access rights, see [Table of file access codes](/windows/security/threat-protection/auditing/event-5145#table-of-file-access-codes). For information about SAM object access right use <https://technet.microsoft.com/> or other informational resources.
|
||||||
|
|
||||||
- **Access Mask** \[Type = HexInt32\]: hexadecimal mask for the operation that was requested or performed. See “Table 13. File access codes.” for more information about file access rights. For information about SAM object access right use <https://technet.microsoft.com/> or other informational resources.
|
- **Access Mask** \[Type = HexInt32\]: hexadecimal mask for the operation that was requested or performed. For more information about file access rights, see [Table of file access codes](/windows/security/threat-protection/auditing/event-5145#table-of-file-access-codes). For information about SAM object access right use <https://technet.microsoft.com/> or other informational resources.
|
||||||
|
|
||||||
- **Privileges Used for Access Check** \[Type = UnicodeString\]: the list of user privileges which were used during the operation, for example, SeBackupPrivilege. This parameter might not be captured in the event, and in that case appears as “-”. See full list of user privileges in the table below:
|
- **Privileges Used for Access Check** \[Type = UnicodeString\]: the list of user privileges which were used during the operation, for example, SeBackupPrivilege. This parameter might not be captured in the event, and in that case appears as “-”. See full list of user privileges in the table below:
|
||||||
|
|
||||||
@ -218,4 +218,4 @@ For 4661(S, F): A handle to an object was requested.
|
|||||||
|
|
||||||
> **Important** For this event, also see [Appendix A: Security monitoring recommendations for many audit events](appendix-a-security-monitoring-recommendations-for-many-audit-events.md).
|
> **Important** For this event, also see [Appendix A: Security monitoring recommendations for many audit events](appendix-a-security-monitoring-recommendations-for-many-audit-events.md).
|
||||||
|
|
||||||
- You can get almost the same information from “[4662](event-4662.md): An operation was performed on an object.” There are no additional recommendations for this event in this document.
|
- You can get almost the same information from “[4662](event-4662.md): An operation was performed on an object.” There are no additional recommendations for this event in this document.
|
||||||
|
|||||||
@ -126,12 +126,12 @@ These events are generated for [ALPC Ports](/windows/win32/etw/alpc) access requ
|
|||||||
|
|
||||||
**Access Request Information:**
|
**Access Request Information:**
|
||||||
|
|
||||||
- **Accesses** \[Type = UnicodeString\]: the list of access rights which were requested by **Subject\\Security ID**. These access rights depend on **Object Type**. “Table 13. File access codes.” contains information about the most common access rights for file system objects. For information about ALPC ports access rights, use <https://technet.microsoft.com/> or other informational resources.
|
- **Accesses** \[Type = UnicodeString\]: the list of access rights which were requested by **Subject\\Security ID**. These access rights depend on **Object Type**. [Table of file access codes](/windows/security/threat-protection/auditing/event-5145#table-of-file-access-codes) contains information about the most common access rights for file system objects. For information about ALPC ports access rights, use <https://technet.microsoft.com/> or other informational resources.
|
||||||
|
|
||||||
- **Access Mask** \[Type = HexInt32\]: hexadecimal mask for the operation that was requested or performed. See “Table 13. File access codes.” for more information about file access rights. For information about ALPC ports access rights, use <https://technet.microsoft.com/> or other informational resources.
|
- **Access Mask** \[Type = HexInt32\]: hexadecimal mask for the operation that was requested or performed. For more information about file access rights, see [Table of file access codes](/windows/security/threat-protection/auditing/event-5145#table-of-file-access-codes). For information about ALPC ports access rights, use <https://technet.microsoft.com/> or other informational resources.
|
||||||
|
|
||||||
## Security Monitoring Recommendations
|
## Security Monitoring Recommendations
|
||||||
|
|
||||||
For 4691(S): Indirect access to an object was requested.
|
For 4691(S): Indirect access to an object was requested.
|
||||||
|
|
||||||
- Typically this event has little to no security relevance and is hard to parse or analyze. There is no recommendation for this event, unless you know exactly what you need to monitor with ALPC Ports.
|
- Typically this event has little to no security relevance and is hard to parse or analyze. There is no recommendation for this event, unless you know exactly what you need to monitor with ALPC Ports.
|
||||||
|
|||||||
@ -220,7 +220,7 @@ The most common values:
|
|||||||
| 0x14 | KDC\_ERR\_TGT\_REVOKED | TGT has been revoked | Since the remote KDC may change its PKCROSS key while there are PKCROSS tickets still active, it SHOULD cache the old PKCROSS keys until the last issued PKCROSS ticket expires. Otherwise, the remote KDC will respond to a client with a KRB-ERROR message of type KDC\_ERR\_TGT\_REVOKED. See [RFC1510](https://www.ietf.org/proceedings/49/I-D/draft-ietf-cat-kerberos-pk-cross-07.txt) for more details. |
|
| 0x14 | KDC\_ERR\_TGT\_REVOKED | TGT has been revoked | Since the remote KDC may change its PKCROSS key while there are PKCROSS tickets still active, it SHOULD cache the old PKCROSS keys until the last issued PKCROSS ticket expires. Otherwise, the remote KDC will respond to a client with a KRB-ERROR message of type KDC\_ERR\_TGT\_REVOKED. See [RFC1510](https://www.ietf.org/proceedings/49/I-D/draft-ietf-cat-kerberos-pk-cross-07.txt) for more details. |
|
||||||
| 0x15 | KDC\_ERR\_CLIENT\_NOTYET | Client not yet valid—try again later | No information. |
|
| 0x15 | KDC\_ERR\_CLIENT\_NOTYET | Client not yet valid—try again later | No information. |
|
||||||
| 0x16 | KDC\_ERR\_SERVICE\_NOTYET | Server not yet valid—try again later | No information. |
|
| 0x16 | KDC\_ERR\_SERVICE\_NOTYET | Server not yet valid—try again later | No information. |
|
||||||
| 0x17 | KDC\_ERR\_KEY\_EXPIRED | Password has expired—change password to reset | The user’s password has expired.<br>This error code cannot occur in event “[4768](event-4768.md). A Kerberos authentication ticket (TGT) was requested”. It occurs in “[4771](event-4771.md). Kerberos pre-authentication failed” event. |
|
| 0x17 | KDC\_ERR\_KEY\_EXPIRED | Password has expired—change password to reset | The user’s password has expired. |
|
||||||
| 0x18 | KDC\_ERR\_PREAUTH\_FAILED | Pre-authentication information was invalid | The wrong password was provided.<br>This error code cannot occur in event “[4768](event-4768.md). A Kerberos authentication ticket (TGT) was requested”. It occurs in “[4771](event-4771.md). Kerberos pre-authentication failed” event. |
|
| 0x18 | KDC\_ERR\_PREAUTH\_FAILED | Pre-authentication information was invalid | The wrong password was provided.<br>This error code cannot occur in event “[4768](event-4768.md). A Kerberos authentication ticket (TGT) was requested”. It occurs in “[4771](event-4771.md). Kerberos pre-authentication failed” event. |
|
||||||
| 0x19 | KDC\_ERR\_PREAUTH\_REQUIRED | Additional pre-authentication required | This error often occurs in UNIX interoperability scenarios. MIT-Kerberos clients do not request pre-authentication when they send a KRB\_AS\_REQ message. If pre-authentication is required (the default), Windows systems will send this error. Most MIT-Kerberos clients will respond to this error by giving the pre-authentication, in which case the error can be ignored, but some clients might not respond in this way. |
|
| 0x19 | KDC\_ERR\_PREAUTH\_REQUIRED | Additional pre-authentication required | This error often occurs in UNIX interoperability scenarios. MIT-Kerberos clients do not request pre-authentication when they send a KRB\_AS\_REQ message. If pre-authentication is required (the default), Windows systems will send this error. Most MIT-Kerberos clients will respond to this error by giving the pre-authentication, in which case the error can be ignored, but some clients might not respond in this way. |
|
||||||
| 0x1A | KDC\_ERR\_SERVER\_NOMATCH | KDC does not know about the requested server | No information. |
|
| 0x1A | KDC\_ERR\_SERVER\_NOMATCH | KDC does not know about the requested server | No information. |
|
||||||
|
|||||||
@ -133,7 +133,7 @@ This event generates once per session, when first access attempt was made.
|
|||||||
|
|
||||||
**Access Request Information:**
|
**Access Request Information:**
|
||||||
|
|
||||||
- **Access Mask** \[Type = HexInt32\]: the sum of hexadecimal values of requested access rights. See “Table 13. File access codes.” for different hexadecimal values for access rights. Has always “**0x1**” value for this event.
|
- **Access Mask** \[Type = HexInt32\]: the sum of hexadecimal values of requested access rights. See [Table of file access codes](/windows/security/threat-protection/auditing/event-5145#table-of-file-access-codes) for different hexadecimal values for access rights. It always has “**0x1**” value for this event.
|
||||||
|
|
||||||
- **Accesses** \[Type = UnicodeString\]: the list of access rights that were requested by **Subject\\Security ID**. These access rights depend on **Object Type**. Has always “**ReadData (or ListDirectory)**” value for this event.
|
- **Accesses** \[Type = UnicodeString\]: the list of access rights that were requested by **Subject\\Security ID**. These access rights depend on **Object Type**. Has always “**ReadData (or ListDirectory)**” value for this event.
|
||||||
|
|
||||||
|
|||||||
@ -135,7 +135,7 @@ This event generates every time network share object (file or folder) was access
|
|||||||
|
|
||||||
**Access Request Information:**
|
**Access Request Information:**
|
||||||
|
|
||||||
- **Access Mask** \[Type = HexInt32\]: the sum of hexadecimal values of requested access rights. See “Table 13. File access codes.” for different hexadecimal values for access rights.
|
- **Access Mask** \[Type = HexInt32\]: the sum of hexadecimal values of requested access rights. See [Table of file access codes](/windows/security/threat-protection/auditing/event-5145#table-of-file-access-codes) for different hexadecimal values for access rights.
|
||||||
|
|
||||||
- **Accesses** \[Type = UnicodeString\]: the list of access rights that were requested by **Subject\\Security ID**. These access rights depend on **Object Type**.
|
- **Accesses** \[Type = UnicodeString\]: the list of access rights that were requested by **Subject\\Security ID**. These access rights depend on **Object Type**.
|
||||||
|
|
||||||
@ -319,4 +319,4 @@ For 5145(S, F): A network share object was checked to see whether client can be
|
|||||||
|
|
||||||
- WRITE\_DAC
|
- WRITE\_DAC
|
||||||
|
|
||||||
- WRITE\_OWNER
|
- WRITE\_OWNER
|
||||||
|
|||||||
@ -8,7 +8,7 @@ ms.pagetype: security
|
|||||||
ms.localizationpriority: medium
|
ms.localizationpriority: medium
|
||||||
author: vinaypamnani-msft
|
author: vinaypamnani-msft
|
||||||
ms.author: vinpa
|
ms.author: vinpa
|
||||||
ms.date: 09/09/2021
|
ms.date: 11/30/2022
|
||||||
ms.reviewer:
|
ms.reviewer:
|
||||||
manager: aaroncz
|
manager: aaroncz
|
||||||
ms.custom: asr
|
ms.custom: asr
|
||||||
@ -28,10 +28,12 @@ ms.topic: how-to
|
|||||||
## Review system requirements
|
## Review system requirements
|
||||||
|
|
||||||
See [System requirements for Microsoft Defender Application Guard](./reqs-md-app-guard.md) to review the hardware and software installation requirements for Microsoft Defender Application Guard.
|
See [System requirements for Microsoft Defender Application Guard](./reqs-md-app-guard.md) to review the hardware and software installation requirements for Microsoft Defender Application Guard.
|
||||||
>[!NOTE]
|
|
||||||
>Microsoft Defender Application Guard is not supported on VMs and VDI environment. For testing and automation on non-production machines, you may enable WDAG on a VM by enabling Hyper-V nested virtualization on the host.
|
> [!NOTE]
|
||||||
|
> Microsoft Defender Application Guard is not supported on VMs and VDI environment. For testing and automation on non-production machines, you may enable WDAG on a VM by enabling Hyper-V nested virtualization on the host.
|
||||||
|
|
||||||
## Prepare for Microsoft Defender Application Guard
|
## Prepare for Microsoft Defender Application Guard
|
||||||
|
|
||||||
Before you can install and use Microsoft Defender Application Guard, you must determine which way you intend to use it in your enterprise. You can use Application Guard in either **Standalone** or **Enterprise-managed** mode.
|
Before you can install and use Microsoft Defender Application Guard, you must determine which way you intend to use it in your enterprise. You can use Application Guard in either **Standalone** or **Enterprise-managed** mode.
|
||||||
|
|
||||||
### Standalone mode
|
### Standalone mode
|
||||||
@ -52,6 +54,7 @@ Applies to:
|
|||||||
You and your security department can define your corporate boundaries by explicitly adding trusted domains and by customizing the Application Guard experience to meet and enforce your needs on employee devices. Enterprise-managed mode also automatically redirects any browser requests to add non-enterprise domain(s) in the container.
|
You and your security department can define your corporate boundaries by explicitly adding trusted domains and by customizing the Application Guard experience to meet and enforce your needs on employee devices. Enterprise-managed mode also automatically redirects any browser requests to add non-enterprise domain(s) in the container.
|
||||||
|
|
||||||
The following diagram shows the flow between the host PC and the isolated container.
|
The following diagram shows the flow between the host PC and the isolated container.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## Install Application Guard
|
## Install Application Guard
|
||||||
@ -60,29 +63,29 @@ Application Guard functionality is turned off by default. However, you can quick
|
|||||||
|
|
||||||
### To install by using the Control Panel
|
### To install by using the Control Panel
|
||||||
|
|
||||||
1. Open the **Control Panel**, click **Programs,** and then click **Turn Windows features on or off**.
|
1. Open the **Control Panel**, click **Programs,** and then select **Turn Windows features on or off**.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
2. Select the check box next to **Microsoft Defender Application Guard** and then click **OK**.
|
2. Select the check box next to **Microsoft Defender Application Guard** and then select **OK**.
|
||||||
|
|
||||||
Application Guard and its underlying dependencies are all installed.
|
Application Guard and its underlying dependencies are all installed.
|
||||||
|
|
||||||
### To install by using PowerShell
|
### To install by using PowerShell
|
||||||
|
|
||||||
>[!NOTE]
|
> [!NOTE]
|
||||||
>Ensure your devices have met all system requirements prior to this step. PowerShell will install the feature without checking system requirements. If your devices don't meet the system requirements, Application Guard may not work. This step is recommended for enterprise managed scenarios only.
|
> Ensure your devices have met all system requirements prior to this step. PowerShell will install the feature without checking system requirements. If your devices don't meet the system requirements, Application Guard may not work. This step is recommended for enterprise managed scenarios only.
|
||||||
|
|
||||||
1. Click the **Search** or **Cortana** icon in the Windows 10 or Windows 11 taskbar and type **PowerShell**.
|
1. Select the **Search** or **Cortana** icon in the Windows 10 or Windows 11 taskbar and type **PowerShell**.
|
||||||
|
|
||||||
2. Right-click **Windows PowerShell**, and then click **Run as administrator**.
|
2. Right-click **Windows PowerShell**, and then select **Run as administrator**.
|
||||||
|
|
||||||
Windows PowerShell opens with administrator credentials.
|
Windows PowerShell opens with administrator credentials.
|
||||||
|
|
||||||
3. Type the following command:
|
3. Type the following command:
|
||||||
|
|
||||||
```
|
```
|
||||||
Enable-WindowsOptionalFeature -online -FeatureName Windows-Defender-ApplicationGuard
|
Enable-WindowsOptionalFeature -Online -FeatureName Windows-Defender-ApplicationGuard
|
||||||
```
|
```
|
||||||
4. Restart the device.
|
4. Restart the device.
|
||||||
|
|
||||||
@ -95,17 +98,15 @@ Application Guard functionality is turned off by default. However, you can quick
|
|||||||
|
|
||||||
:::image type="content" source="images/MDAG-EndpointMgr-newprofile.jpg" alt-text="Enroll devices in Intune.":::
|
:::image type="content" source="images/MDAG-EndpointMgr-newprofile.jpg" alt-text="Enroll devices in Intune.":::
|
||||||
|
|
||||||
1. Sign in to the [Microsoft Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431).
|
1. In the [Microsoft Endpoint Manager admin center](https://go.microsoft.com/fwlink/?linkid=2109431), choose **Devices** > **Configuration profiles** > **+ Create profile**, and do the following: <br/>
|
||||||
|
|
||||||
1. Choose **Devices** > **Configuration profiles** > **+ Create profile**, and do the following: <br/>
|
|
||||||
|
|
||||||
1. In the **Platform** list, select **Windows 10 and later**.
|
1. In the **Platform** list, select **Windows 10 and later**.
|
||||||
|
|
||||||
1. In the **Profile** list, select **Endpoint protection**.
|
2. In the **Profile** type, choose **Templates** and select **Endpoint protection**.
|
||||||
|
|
||||||
1. Choose **Create**.
|
3. Choose **Create**.
|
||||||
|
|
||||||
1. Specify the following settings for the profile:
|
2. Specify the following settings for the profile:
|
||||||
|
|
||||||
- **Name** and **Description**
|
- **Name** and **Description**
|
||||||
|
|
||||||
@ -115,16 +116,16 @@ Application Guard functionality is turned off by default. However, you can quick
|
|||||||
|
|
||||||
- Choose your preferences for **Clipboard behavior**, **External content**, and the remaining settings.
|
- Choose your preferences for **Clipboard behavior**, **External content**, and the remaining settings.
|
||||||
|
|
||||||
1. Choose **OK**, and then choose **OK** again.
|
3. Choose **OK**, and then choose **OK** again.
|
||||||
|
|
||||||
1. Review your settings, and then choose **Create**.
|
4. Review your settings, and then choose **Create**.
|
||||||
|
|
||||||
1. Choose **Assignments**, and then do the following:
|
5. Choose **Assignments**, and then do the following:
|
||||||
|
|
||||||
1. On the **Include** tab, in the **Assign to** list, choose an option.
|
1. On the **Include** tab, in the **Assign to** list, choose an option.
|
||||||
|
|
||||||
1. If you have any devices or users you want to exclude from this endpoint protection profile, specify those on the **Exclude** tab.
|
2. If you have any devices or users you want to exclude from this endpoint protection profile, specify those on the **Exclude** tab.
|
||||||
|
|
||||||
1. Click **Save**.
|
3. Select **Save**.
|
||||||
|
|
||||||
After the profile is created, any devices to which the policy should apply will have Microsoft Defender Application Guard enabled. Users might have to restart their devices in order for protection to be in place.
|
After the profile is created, any devices to which the policy should apply will have Microsoft Defender Application Guard enabled. Users might have to restart their devices in order for protection to be in place.
|
||||||
|
|||||||
@ -22,6 +22,7 @@ ms.technology: itpro-security
|
|||||||
# Account lockout duration
|
# Account lockout duration
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Account lockout duration** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Account lockout duration** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Account Lockout Policy
|
# Account Lockout Policy
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the Account Lockout Policy settings and links to information about each policy setting.
|
Describes the Account Lockout Policy settings and links to information about each policy setting.
|
||||||
|
|||||||
@ -22,6 +22,7 @@ ms.technology: itpro-security
|
|||||||
# Account lockout threshold
|
# Account lockout threshold
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Account lockout threshold** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Account lockout threshold** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Account Policies
|
# Account Policies
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
An overview of account policies in Windows and provides links to policy descriptions.
|
An overview of account policies in Windows and provides links to policy descriptions.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Accounts: Administrator account status
|
# Accounts: Administrator account status
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Accounts: Administrator account status** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Accounts: Administrator account status** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Accounts: Block Microsoft accounts
|
# Accounts: Block Microsoft accounts
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, management, and security considerations for the **Accounts: Block Microsoft accounts** security policy setting.
|
Describes the best practices, location, values, management, and security considerations for the **Accounts: Block Microsoft accounts** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Accounts: Guest account status - security policy setting
|
# Accounts: Guest account status - security policy setting
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Accounts: Guest account status** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Accounts: Guest account status** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Accounts: Limit local account use of blank passwords to console logon only
|
# Accounts: Limit local account use of blank passwords to console logon only
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Accounts: Limit local account use of blank passwords to console logon only** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Accounts: Limit local account use of blank passwords to console logon only** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Accounts: Rename administrator account
|
# Accounts: Rename administrator account
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
This security policy reference topic for the IT professional describes the best practices, location, values, and security considerations for this policy setting.
|
This security policy reference topic for the IT professional describes the best practices, location, values, and security considerations for this policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Accounts: Rename guest account - security policy setting
|
# Accounts: Rename guest account - security policy setting
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Accounts: Rename guest account** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Accounts: Rename guest account** security policy setting.
|
||||||
|
|||||||
@ -94,7 +94,7 @@ The Security Compliance Manager is a downloadable tool that helps you plan, depl
|
|||||||
|
|
||||||
**To administer security policies by using the Security Compliance Manager**
|
**To administer security policies by using the Security Compliance Manager**
|
||||||
|
|
||||||
1. Download the most recent version. You can find out more info on the [Microsoft Security Guidance](/archive/blogs/secguide/) blog.
|
1. Download the most recent version. You can find more info on the [Microsoft Security Baselines](https://techcommunity.microsoft.com/t5/microsoft-security-baselines/bg-p/Microsoft-Security-Baselines) blog.
|
||||||
1. Read the relevant security baseline documentation that is included in this tool.
|
1. Read the relevant security baseline documentation that is included in this tool.
|
||||||
1. Download and import the relevant security baselines. The installation process steps you through baseline selection.
|
1. Download and import the relevant security baselines. The installation process steps you through baseline selection.
|
||||||
1. Open the Help and follow instructions how to customize, compare, or merge your security baselines before deploying those baselines.
|
1. Open the Help and follow instructions how to customize, compare, or merge your security baselines before deploying those baselines.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Audit: Audit the use of Backup and Restore privilege
|
# Audit: Audit the use of Backup and Restore privilege
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Audit: Audit the use of Backup and Restore privilege** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Audit: Audit the use of Backup and Restore privilege** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings
|
# Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Audit Policy
|
# Audit Policy
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Provides information about basic audit policies that are available in Windows and links to information about each setting.
|
Provides information about basic audit policies that are available in Windows and links to information about each setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Audit: Shut down system immediately if unable to log security audits
|
# Audit: Shut down system immediately if unable to log security audits
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, management practices, and security considerations for the **Audit: Shut down system immediately if unable to log security audits** security policy setting.
|
Describes the best practices, location, values, management practices, and security considerations for the **Audit: Shut down system immediately if unable to log security audits** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# DCOM: Machine Launch Restrictions in Security Descriptor Definition Language (SDDL) syntax
|
# DCOM: Machine Launch Restrictions in Security Descriptor Definition Language (SDDL) syntax
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **DCOM: Machine Launch Restrictions in Security Descriptor Definition Language (SDDL) syntax** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **DCOM: Machine Launch Restrictions in Security Descriptor Definition Language (SDDL) syntax** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Devices: Allow undock without having to log on
|
# Devices: Allow undock without having to log on
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Devices: Allow undock without having to log on** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Devices: Allow undock without having to log on** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Devices: Allowed to format and eject removable media
|
# Devices: Allowed to format and eject removable media
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Devices: Allowed to format and eject removable media** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Devices: Allowed to format and eject removable media** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Devices: Prevent users from installing printer drivers
|
# Devices: Prevent users from installing printer drivers
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Devices: Prevent users from installing printer drivers** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Devices: Prevent users from installing printer drivers** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Devices: Restrict CD-ROM access to locally logged-on user only
|
# Devices: Restrict CD-ROM access to locally logged-on user only
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Devices: Restrict CD-ROM access to locally logged-on user only** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Devices: Restrict CD-ROM access to locally logged-on user only** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Enforce password history
|
# Enforce password history
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, policy management, and security considerations for the **Enforce password history** security policy setting.
|
Describes the best practices, location, values, policy management, and security considerations for the **Enforce password history** security policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Maximum password age
|
# Maximum password age
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, policy management, and security considerations for the **Maximum password age** security policy setting.
|
Describes the best practices, location, values, policy management, and security considerations for the **Maximum password age** security policy setting.
|
||||||
|
|||||||
@ -19,6 +19,7 @@ ms.topic: conceptual
|
|||||||
# Minimum password age
|
# Minimum password age
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, policy management, and security considerations for the **Minimum password age** security policy setting.
|
Describes the best practices, location, values, policy management, and security considerations for the **Minimum password age** security policy setting.
|
||||||
@ -90,4 +91,4 @@ If you set a password for a user but want that user to change the password when
|
|||||||
|
|
||||||
## Related topics
|
## Related topics
|
||||||
|
|
||||||
- [Password Policy](password-policy.md)
|
- [Password Policy](password-policy.md)
|
||||||
|
|||||||
@ -22,6 +22,7 @@ ms.technology: itpro-security
|
|||||||
# Minimum password length
|
# Minimum password length
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
This article describes the recommended practices, location, values, policy management, and security considerations for the **Minimum password length** security policy setting.
|
This article describes the recommended practices, location, values, policy management, and security considerations for the **Minimum password length** security policy setting.
|
||||||
|
|||||||
@ -22,6 +22,7 @@ ms.date: 12/31/2017
|
|||||||
# Password must meet complexity requirements
|
# Password must meet complexity requirements
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Password must meet complexity requirements** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Password must meet complexity requirements** security policy setting.
|
||||||
|
|||||||
@ -22,6 +22,7 @@ ms.technology: itpro-security
|
|||||||
# Password Policy
|
# Password Policy
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
An overview of password policies for Windows and links to information for each policy setting.
|
An overview of password policies for Windows and links to information for each policy setting.
|
||||||
|
|||||||
@ -20,6 +20,7 @@ ms.technology: itpro-security
|
|||||||
# Reset account lockout counter after
|
# Reset account lockout counter after
|
||||||
|
|
||||||
**Applies to**
|
**Applies to**
|
||||||
|
- Windows 11
|
||||||
- Windows 10
|
- Windows 10
|
||||||
|
|
||||||
Describes the best practices, location, values, and security considerations for the **Reset account lockout counter after** security policy setting.
|
Describes the best practices, location, values, and security considerations for the **Reset account lockout counter after** security policy setting.
|
||||||
@ -76,4 +77,4 @@ If you don't configure this policy setting or if the value is configured to an i
|
|||||||
|
|
||||||
## Related topics
|
## Related topics
|
||||||
|
|
||||||
- [Account Lockout Policy](account-lockout-policy.md)
|
- [Account Lockout Policy](account-lockout-policy.md)
|
||||||
|
|||||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
x
Reference in New Issue
Block a user