Merge branch 'master' into wcf
@ -2,19 +2,19 @@
|
||||
|
||||
documentType: LandingData
|
||||
|
||||
title: Microsoft Edge group policies
|
||||
title: Microsoft Edge Legacy group policies
|
||||
|
||||
metadata:
|
||||
|
||||
document_id:
|
||||
|
||||
title: Microsoft Edge group policies
|
||||
title: Microsoft Edge Legacy group policies
|
||||
|
||||
description: Learn how to configure group policies in Microsoft Edge on Windows 10.
|
||||
description: Learn how to configure group policies in Microsoft Edge Legacy on Windows 10.
|
||||
|
||||
text: Some of the features in Microsoft Edge gives you the ability to set a custom URL for the New Tab page or Home button. Another new feature allows you to hide or show the Favorites bar, giving you more control over the favorites bar.
|
||||
text: Some of the features in Microsoft Edge Legacy gives you the ability to set a custom URL for the New Tab page or Home button. Another new feature allows you to hide or show the Favorites bar, giving you more control over the favorites bar. (To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).)
|
||||
|
||||
keywords: Microsoft Edge, Windows 10, Windows 10 Mobile
|
||||
keywords: Microsoft Edge Legacy, Windows 10, Windows 10 Mobile
|
||||
|
||||
ms.localizationpriority: medium
|
||||
|
||||
@ -36,7 +36,7 @@ sections:
|
||||
|
||||
- type: markdown
|
||||
|
||||
text: Microsoft Edge works with Group Policy and Microsoft Intune to help you manage your organization's computer settings. Group Policy objects (GPOs) can include registry-based Administrative Template policy settings, security settings, software deployment information, scripts, folder redirection, and preferences.
|
||||
text: (Note - You've reached the documentation for Microsoft Edge version 45 and earlier. To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).) Microsoft Edge Legacy works with Group Policy and Microsoft Intune to help you manage your organization's computer settings. Group Policy objects (GPOs) can include registry-based Administrative Template policy settings, security settings, software deployment information, scripts, folder redirection, and preferences.
|
||||
|
||||
- items:
|
||||
|
||||
|
||||
@ -2,19 +2,19 @@
|
||||
|
||||
documentType: LandingData
|
||||
|
||||
title: Microsoft Edge Group Policy configuration options
|
||||
title: Microsoft Edge Legacy Group Policy configuration options
|
||||
|
||||
metadata:
|
||||
|
||||
document_id:
|
||||
|
||||
title: Microsoft Edge Group Policy configuration options
|
||||
title: Microsoft Edge Group Legacy Policy configuration options
|
||||
|
||||
description:
|
||||
|
||||
text: Learn how to deploy and configure group policies in Microsoft Edge on Windows 10. Some of the features coming to Microsoft Edge gives you the ability to set a custom URL for the New Tab page or Home button. Another new feature allows you to hide or show the Favorites bar, giving you more control over the favorites bar.
|
||||
text: (Note - You've reached the documentation for Microsoft Edge version 45 and earlier. To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).) Learn how to deploy and configure group policies in Microsoft Edge Legacy on Windows 10. Some of the features coming to Microsoft Edge Legacy gives you the ability to set a custom URL for the New Tab page or Home button. Another new feature allows you to hide or show the Favorites bar, giving you more control over the favorites bar.
|
||||
|
||||
keywords: Microsoft Edge, Windows 10
|
||||
keywords: Microsoft Edge Legacy, Windows 10
|
||||
|
||||
ms.localizationpriority: medium
|
||||
|
||||
@ -36,7 +36,7 @@ sections:
|
||||
|
||||
- type: markdown
|
||||
|
||||
text: Learn about interoperability goals and enterprise guidance along with system requirements, language support and frequently asked questions.
|
||||
text: (Note - You've reached the documentation for Microsoft Edge version 45 and earlier. To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).) Learn about interoperability goals and enterprise guidance along with system requirements, language support and frequently asked questions.
|
||||
|
||||
- items:
|
||||
|
||||
|
||||
@ -32,6 +32,7 @@
|
||||
## [Create, share, and view photos and video](holographic-photos-and-videos.md)
|
||||
|
||||
# User management and access management
|
||||
## [Accounts on HoloLens](hololens-identity.md)
|
||||
## [Share your HoloLens with multiple people](hololens-multiple-users.md)
|
||||
## [Set up HoloLens as a kiosk (single application access)](hololens-kiosk.md)
|
||||
## [Set up limited application access](hololens-kiosk.md)
|
||||
|
||||
111
devices/hololens/hololens-identity.md
Normal file
@ -0,0 +1,111 @@
|
||||
---
|
||||
title: Managing user identity and login on HoloLens
|
||||
description: Manage user identity, security, and login on HoloLens.
|
||||
keywords: HoloLens, user, account, aad, adfs, microsoft account, msa, credentials, reference
|
||||
ms.assetid: 728cfff2-81ce-4eb8-9aaa-0a3c3304660e
|
||||
author: scooley
|
||||
ms.author: scooley
|
||||
ms.date: 1/6/2019
|
||||
ms.prod: hololens
|
||||
ms.topic: article
|
||||
ms.sitesec: library
|
||||
ms.topic: article
|
||||
ms.localizationpriority: medium
|
||||
audience: ITPro
|
||||
manager: jarrettr
|
||||
appliesto:
|
||||
- HoloLens (1st gen)
|
||||
- HoloLens 2
|
||||
---
|
||||
|
||||
# User identity and signin
|
||||
|
||||
> [!NOTE]
|
||||
> This article is a technical reference for IT Pros and tech enthusiasts. If you're looking for HoloLens set up instructions, read "[Setting up your HoloLens (1st gen)](hololens1-start.md)" or "[Setting up your HoloLens 2](hololens2-start.md)".
|
||||
|
||||
Like other Windows devices, HoloLens always operates under a user context. There is always a user identity. HoloLens treats identity in almost the same manner as other Windows 10 devices do. This article is a deep-dive reference for identity on HoloLens, and focuses on how HoloLens differs from other Windows 10 devices.
|
||||
|
||||
HoloLens supports several kinds of user identities. You can use one or more user accounts to sign in. Here's an overview of the identity types and authentication options on HoloLens:
|
||||
|
||||
| Identity type | Accounts per device | Authentication options |
|
||||
| --- | --- | --- |
|
||||
| [Azure Active Directory (AAD)](https://docs.microsoft.com/azure/active-directory/) | 32 (see details) | <ul><li>Azure web credential provider</li><li>Azure Authenticator App</li><li>Biometric (Iris) – HoloLens 2 only</li><li>PIN – Optional for HoloLens (1st gen), required for HoloLens 2</li><li>Password</li></ul> |
|
||||
| [Microsoft Account (MSA)](https://docs.microsoft.com/windows/security/identity-protection/access-control/microsoft-accounts) | 1 | <ul><li>Biometric (Iris) – HoloLens 2 only</li><li>PIN – Optional for HoloLens (1st gen), required for HoloLens 2</li><li>Password</li></ul> |
|
||||
| [Local account](https://docs.microsoft.com/windows/security/identity-protection/access-control/local-accounts) | 1 | Password |
|
||||
|
||||
Cloud-connected accounts (AAD and MSA) offer more features because they can use Azure services.
|
||||
|
||||
## Setting up users
|
||||
|
||||
The most common way to set up a new user is during the HoloLens out-of-box experience (OOBE). During setup, HoloLens prompts for a user to sign in by using the account that they want to use on the device. This account can be a consumer Microsoft account or an enterprise account that has been configured in Azure. See Setting up your [HoloLens (1st gen)](hololens1-start.md) or [HoloLens 2](hololens2-start.md).
|
||||
|
||||
Like Windows on other devices, signing in during setup creates a user profile on the device. The user profile stores apps and data. The same account also provides Single Sign-on for apps such as Edge or Skype by using the Windows Account Manager APIs.
|
||||
|
||||
If you use an enterprise or organizational account to sign in to HoloLens, HoloLens enrolls in the organization's IT infrastructure. This enrollment allows your IT Admin to configure Mobile Device Management (MDM) to send group policies to your HoloLens.
|
||||
|
||||
By default, as for other Windows 10 devices, you'll have to sign in again when HoloLens restarts or resumes from standby. You can use the Settings app to change this behavior, or the behavior can be controlled by group policy.
|
||||
|
||||
### Linked accounts
|
||||
|
||||
As in the Desktop version of Windows, you can link additional web account credentials to your HoloLens account. Such linking makes it easier to access resources across or within apps (such as the Store) or to combine access to personal and work resources. After you connect an account to the device, you can grant permission to use the device to apps so that you don't have to sign in to each app individually.
|
||||
|
||||
Linking accounts does not separate the user data created on the device, such as images or downloads.
|
||||
|
||||
### Setting up multi-user support (AAD only)
|
||||
|
||||
> [!NOTE]
|
||||
> **HoloLens (1st gen)** began supporting multiple AAD users in the [Windows 10 April 2018 Update](https://docs.microsoft.com/windows/mixed-reality/release-notes-april-2018) as part of [Windows Holographic for Business](hololens-upgrade-enterprise.md).
|
||||
|
||||
HoloLens supports multiple users from the same AAD tenant. To use this feature, you must use an account that belongs to your organization to set up the device. Subsequently, other users from the same tenant can sign in to the device from the sign-in screen or by tapping the user tile on the Start panel. Only one user can be signed in at a time. When a user signs in, HoloLens signs out the previous user.
|
||||
|
||||
All users can use the apps installed on the device. However, each user has their own app data and preferences. Removing an app from the device removes it for all users.
|
||||
|
||||
## Removing users
|
||||
|
||||
You can remove a user from the device by going to **Settings** > **Accounts** > **Other people**. This action also reclaims space by removing all of that user's app data from the device.
|
||||
|
||||
## Using single sign-on within an app
|
||||
|
||||
As an app developer, you can take advantage of linked identities on HoloLens by using the [Windows Account Manager APIs](https://docs.microsoft.com/uwp/api/Windows.Security.Authentication.Web.Core), just as you would on other Windows devices. Some code samples for these APIs are available [here](https://go.microsoft.com/fwlink/p/?LinkId=620621).
|
||||
|
||||
Any account interrupts that might occur, such as requesting user consent for account information, two-factor authentication, and so forth, must be handled when the app requests an authentication token.
|
||||
|
||||
If your app requires a specific account type that hasn't been linked previously, your app can ask the system to prompt the user to add one. This request triggers the account settings pane to launch as a modal child of your app. For 2D apps, this window renders directly over the center of your app. For Unity apps, this request briefly takes the user out of your holographic app to render the child window. For information about customizing the commands and actions on this pane, see [WebAccountCommand Class](https://docs.microsoft.com/uwp/api/Windows.UI.ApplicationSettings.WebAccountCommand).
|
||||
|
||||
## Enterprise and other authentication
|
||||
|
||||
If your app uses other types of authentication, such as NTLM, Basic, or Kerberos, you can use [Windows Credential UI](https://docs.microsoft.com/uwp/api/Windows.Security.Credentials.UI) to collect, process, and store the user's credentials. The user experience for collecting these credentials is very similar to other cloud-driven account interrupts, and appears as a child app on top of your 2D app or briefly suspends a Unity app to show the UI.
|
||||
|
||||
## Deprecated APIs
|
||||
|
||||
One way in which developing for HoloLens differs from developing for Desktop is that the [OnlineIDAuthenticator](https://docs.microsoft.com/uwp/api/Windows.Security.Authentication.OnlineId.OnlineIdAuthenticator) API is not fully supported. Although the API returns a token if the primary account is in good-standing, interrupts such as those described in this article do not display any UI for the user and fail to correctly authenticate the account.
|
||||
|
||||
## Frequently asked questions
|
||||
|
||||
### Is Windows Hello for Business supported on HoloLens?
|
||||
|
||||
Windows Hello for Business (which supports using a PIN to sign in) is supported for HoloLens. To allow Windows Hello for Business PIN sign-in on HoloLens:
|
||||
|
||||
1. The HoloLens device must be [managed by MDM](hololens-enroll-mdm.md).
|
||||
1. You must enable Windows Hello for Business for the device. ([See instructions for Microsoft Intune.](https://docs.microsoft.com/intune/windows-hello))
|
||||
1. On HoloLens, the user can then use **Settings** > **Sign-in Options** > **Add PIN** to set up a PIN.
|
||||
|
||||
> [!NOTE]
|
||||
> Users who sign in by using a Microsoft account can also set up a PIN in **Settings** > **Sign-in Options** > **Add PIN**. This PIN is associated with [Windows Hello](https://support.microsoft.com/help/17215/windows-10-what-is-hello), rather than [Windows Hello for Business](https://docs.microsoft.com/windows/security/identity-protection/hello-for-business/hello-overview).
|
||||
|
||||
#### Does the type of account change the sign-in behavior?
|
||||
|
||||
Yes, the behavior for the type of account affects the sign-in behavior. If you apply policies for sign-in, the policy is always respected. If no policy for sign-in is applied, these are the default behaviors for each account type:
|
||||
|
||||
- **Microsoft account**: signs in automatically
|
||||
- **Local account**: always asks for password, not configurable in **Settings**
|
||||
- **Azure AD**: asks for password by default, and configurable by **Settings** to no longer ask for password.
|
||||
|
||||
> [!NOTE]
|
||||
> Inactivity timers are currently not supported, which means that the **AllowIdleReturnWithoutPassword** policy is only respected when the device goes into StandBy.
|
||||
|
||||
## Additional resources
|
||||
|
||||
Read much more about user identity protection and authentication on [the Windows 10 security and identity documentation](https://docs.microsoft.com/windows/security/identity-protection/).
|
||||
|
||||
Learn more about setting up hybrid identity infrastructure thorough the [Azure Hybrid identity documentation](https://docs.microsoft.com/azure/active-directory/hybrid/).
|
||||
@ -50,9 +50,6 @@ You can use Windows Installer commands (Msiexec.exe) to deploy Surface Dock Firm
|
||||
> [!NOTE]
|
||||
> A log file is not created by default. In order to create a log file, you will need to append "/l*v [path]"
|
||||
|
||||
> [!NOTE]
|
||||
> A log file is not created by default. In order to create a log file, you will need to append "/l*v [path]"
|
||||
|
||||
For more information, refer to [Command line options](https://docs.microsoft.com/windows/win32/msi/command-line-options) documentation.
|
||||
|
||||
> [!IMPORTANT]
|
||||
|
||||
@ -206,7 +206,7 @@ This node is deprecated. Use **Biometrics/UseBiometrics** node instead.
|
||||
|
||||
<a href="" id="biometrics--only-for---device-vendor-msft-"></a>**Biometrics** (only for ./Device/Vendor/MSFT)
|
||||
Node for defining biometric settings. This node was added in Windows 10, version 1511.
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business prior to Windows 10 version 1903 (May 2019 Update).*
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business.*
|
||||
|
||||
<a href="" id="biometrics-usebiometrics--only-for---device-vendor-msft-"></a>**Biometrics/UseBiometrics** (only for ./Device/Vendor/MSFT)
|
||||
Boolean value used to enable or disable the use of biometric gestures, such as face and fingerprint, as an alternative to the PIN gesture for Windows Hello for Business. Users must still configure a PIN if they configure biometric gestures to use in case of failures. This node was added in Windows 10, version 1511.
|
||||
@ -217,7 +217,7 @@ Default value is true, enabling the biometric gestures for use with Windows Hell
|
||||
|
||||
Supported operations are Add, Get, Delete, and Replace.
|
||||
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business.*
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business prior to Windows 10 version 1903 (May 2019 Update).*
|
||||
|
||||
<a href="" id="biometrics-facialfeaturesuseenhancedantispoofing--only-for---device-vendor-msft-"></a>**Biometrics/FacialFeaturesUseEnhancedAntiSpoofing** (only for ./Device/Vendor/MSFT)
|
||||
Boolean value used to enable or disable enhanced anti-spoofing for facial feature recognition on Windows Hello face authentication. This node was added in Windows 10, version 1511.
|
||||
|
||||
@ -14,10 +14,14 @@ ms.localizationpriority: medium
|
||||
|
||||
# Policy CSP - Browser
|
||||
|
||||
|
||||
> [!NOTE]
|
||||
> You've reached the documentation for Microsoft Edge version 45 and earlier. To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).
|
||||
|
||||
<hr/>
|
||||
|
||||
> [!NOTE]
|
||||
> You've reached the documentation for Microsoft Edge version 45 and earlier. To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).
|
||||
|
||||
<!--Policies-->
|
||||
## Browser policies
|
||||
|
||||
|
||||
@ -29,21 +29,11 @@ If you have paid subscriptions to Office 365, Microsoft Dynamics CRM Online, Ent
|
||||
|
||||

|
||||
|
||||
3. On the **Admin center** page, hover your mouse over the Admin tools icon on the left and then click **Azure AD**. This will take you to the Azure Active Directory sign-up page and brings up your existing Office 365 organization account information.
|
||||
3. On the **Admin center** page, under Admin Centers on the left, click **Azure Active Directory**. This will take you to the Azure Active Directory portal.
|
||||
|
||||

|
||||
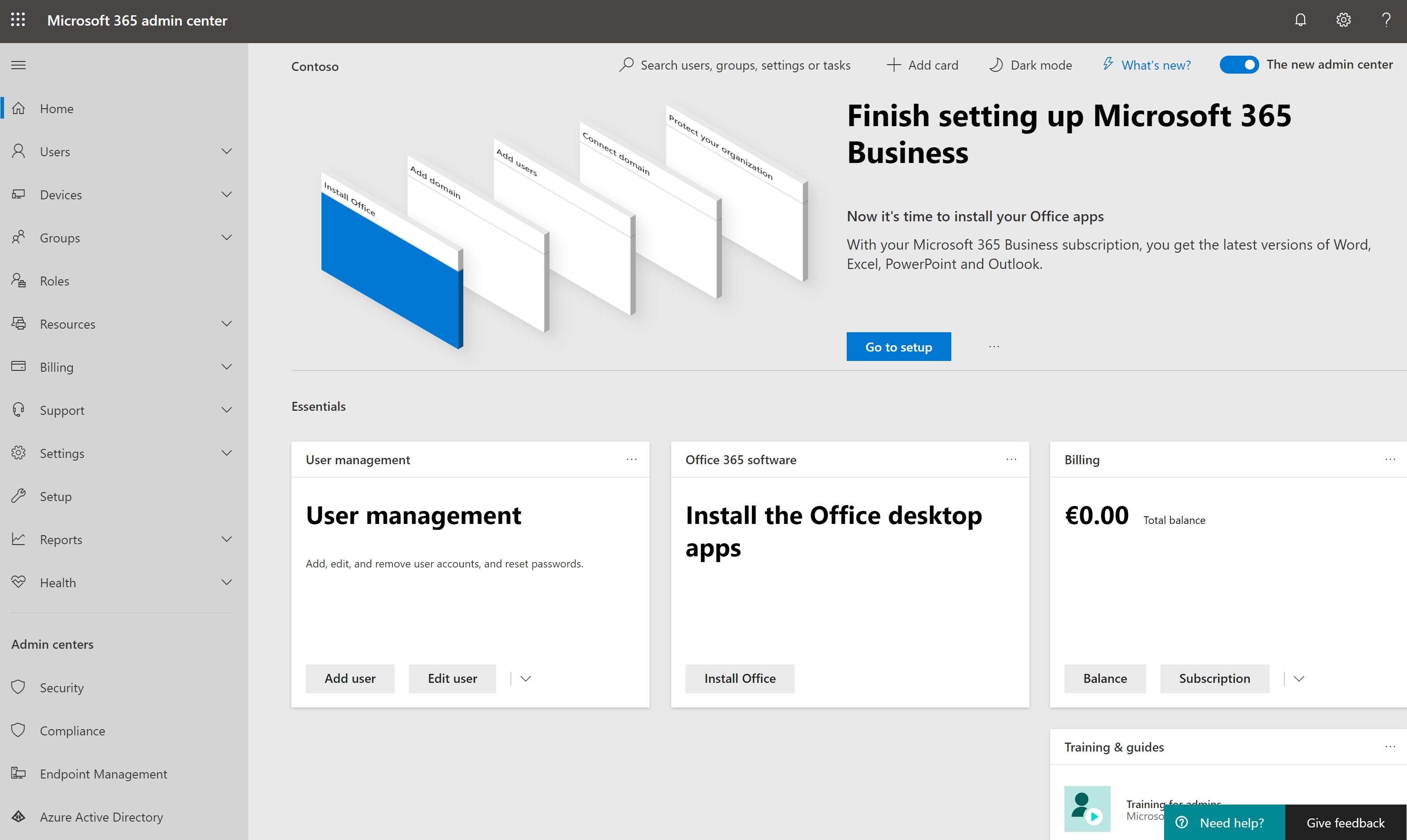
|
||||
|
||||
4. On the **Sign up** page, make sure to enter a valid phone number and then click **Sign up**.
|
||||
|
||||

|
||||
|
||||
5. It may take a few minutes to process the request.
|
||||
|
||||

|
||||
|
||||
6. You will see a welcome page when the process completes.
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
@ -125,9 +125,9 @@ Starting with Windows 10, version 1703, using Settings to control the pause beha
|
||||
|
||||
## Configure when devices receive Quality Updates
|
||||
|
||||
Quality Updates are typically published on the first Tuesday of every month, although they can be released at any time. You can define if, and for how long, you would like to defer receiving Quality Updates following their availability. You can defer receiving these Quality Updates for a period of up to 35 days from their release by setting the **DeferQualityUpdatesPeriodinDays** value.
|
||||
Quality updates are typically published on the first Tuesday of every month, although they can be released at any time. You can define if, and for how long, you would like to defer receiving Quality updates following their availability. You can defer receiving these quality updates for a period of up to 30 days from their release by setting the **DeferQualityUpdatesPeriodinDays** value.
|
||||
|
||||
You can set your system to receive updates for other Microsoft products—known as Microsoft Updates (such as Microsoft Office, Visual Studio)—along with Windows Updates by setting the **AllowMUUpdateService** policy. When you do this, these Microsoft Updates will follow the same deferral and pause rules as all other Quality Updates.
|
||||
You can set your system to receive updates for other Microsoft products—known as Microsoft updates (such as Microsoft Office, Visual Studio)—along with Windows updates by setting the **AllowMUUpdateService** policy. When you do this, these Microsoft updates will follow the same deferral and pause rules as all other quality updates.
|
||||
|
||||
>[!IMPORTANT]
|
||||
>This policy defers both Feature and Quality Updates on Windows 10 Mobile Enterprise.
|
||||
@ -146,7 +146,7 @@ You can set your system to receive updates for other Microsoft products—known
|
||||
|
||||
## Pause quality updates
|
||||
|
||||
You can also pause a system from receiving Quality Updates for a period of up to 35 days from when the value is set. After 35 days has passed, the pause setting will automatically expire and the device will scan Windows Update for applicable quality Updates. Following this scan, you can then pause quality Updates for the device again.
|
||||
You can also pause a system from receiving quality updates for a period of up to 35 days from when the value is set. After 35 days have passed, the pause setting will automatically expire and the device will scan Windows Update for applicable quality updates. Following this scan, you can then pause quality updates for the device again.
|
||||
|
||||
Starting with Windows 10, version 1703, when you configure a pause by using policy, you must set a start date for the pause to begin. The pause period is calculated by adding 35 days to this start date.
|
||||
|
||||
@ -201,9 +201,9 @@ The policy settings to **Select when Feature Updates are received** allows you t
|
||||
* Group Policy: **Computer Configuration/Administrative Templates/Windows Components/Windows Update/ Windows Update for Business** - *Select when Preview Builds and Feature Updates are received*
|
||||
* MDM: **Update/BranchReadinessLevel**
|
||||
|
||||
## Exclude drivers from Quality Updates
|
||||
## Exclude drivers from quality updates
|
||||
|
||||
Starting with Windows 10, version 1607, you can selectively opt out of receiving driver update packages as part of your normal quality update cycle. This policy will not apply to updates to drivers provided with the operating system (which will be packaged within a security or critical update) or to Feature Updates, where drivers might be dynamically installed to ensure the Feature Update process can complete.
|
||||
Starting with Windows 10, version 1607, you can selectively opt out of receiving driver update packages as part of your normal quality update cycle. This policy will not apply to updates to drivers provided with the operating system (which will be packaged within a security or critical update) or to feature updates, where drivers might be dynamically installed to ensure the feature update process can complete.
|
||||
|
||||
**Policy settings to exclude drivers**
|
||||
|
||||
|
||||
@ -35,7 +35,7 @@ The following table describes some log files and how to use them for troubleshoo
|
||||
<br>
|
||||
|
||||
<table>
|
||||
<tr><td BGCOLOR="#a0e4fa"><B>Log file</td><td BGCOLOR="#a0e4fa"><B>Phase: Location</td><td BGCOLOR="#a0e4fa"><B>Description</td><td BGCOLOR="#a0e4fa"><B>When to use</td>
|
||||
<tr><td BGCOLOR="#a0e4fa"><font color="#000000"><B>Log file</td><td BGCOLOR="#a0e4fa"><font color="#000000"><B>Phase: Location</td><td BGCOLOR="#a0e4fa"><font color="#000000"><B>Description</td><td BGCOLOR="#a0e4fa"><font color="#000000"><B>When to use</td>
|
||||
<tr><td rowspan="5">setupact.log</td><td>Down-Level:<br>$Windows.~BT\Sources\Panther</td><td>Contains information about setup actions during the downlevel phase. </td>
|
||||
<td>All down-level failures and starting point for rollback investigations.<br> This is the most important log for diagnosing setup issues.</td>
|
||||
<tr><td>OOBE:<br>$Windows.~BT\Sources\Panther\UnattendGC</td>
|
||||
|
||||
@ -513,9 +513,9 @@ This error has more than one possible cause. Attempt [quick fixes](quick-fixes.m
|
||||
<br /><table>
|
||||
|
||||
<tr>
|
||||
<td BGCOLOR="#a0e4fa"><b>Error code</b></th>
|
||||
<td BGCOLOR="#a0e4fa"><b>Cause</b></th>
|
||||
<td BGCOLOR="#a0e4fa"><b>Mitigation</b></th>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><b>Error code</b></font></td>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><b>Cause</b></font></td>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><b>Mitigation</b></font></td>
|
||||
</tr>
|
||||
|
||||
<tr>
|
||||
@ -647,7 +647,7 @@ For detailed information on how to run these steps check out <a href="https://bl
|
||||
|
||||
<br><table>
|
||||
|
||||
<tr><td BGCOLOR="#a0e4fa">Error Codes<td BGCOLOR="#a0e4fa">Cause<td BGCOLOR="#a0e4fa">Mitigation</td></tr>
|
||||
<tr><td BGCOLOR="#a0e4fa"><font color="#000000">Error Codes<td BGCOLOR="#a0e4fa"><font color="#000000">Cause<td BGCOLOR="#a0e4fa"><font color="#000000">Mitigation</td></tr>
|
||||
<tr><td>0x80070003- 0x20007
|
||||
<td>This is a failure during SafeOS phase driver installation.
|
||||
|
||||
|
||||
@ -91,7 +91,7 @@ The following tables provide the corresponding phase and operation for values of
|
||||
<br>
|
||||
|
||||
<table cellspacing="0" cellpadding="0">
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><b>Extend code: phase</b></td>
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><font color="#000000"><b>Extend code: phase</b></td>
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'><b>Hex</b><td style='padding:0in 5.4pt 0in 5.4pt'><b>Phase</b>
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'>0<td style='padding:0in 4pt 0in 4pt'>SP_EXECUTION_UNKNOWN
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'>1<td style='padding:0in 4pt 0in 4pt'>SP_EXECUTION_DOWNLEVEL
|
||||
@ -103,7 +103,7 @@ The following tables provide the corresponding phase and operation for values of
|
||||
|
||||
|
||||
<table border="0" style='border-collapse:collapse;border:none'>
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><B>Extend code: operation</B></td>
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><font color="#000000"><B>Extend code: operation</B></td>
|
||||
<tr><td align="left" valign="top" style='border:dotted #A6A6A6 1.0pt;'>
|
||||
<table>
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'><b>Hex</b><td style='padding:0in 4pt 0in 4pt'><span style='padding:0in 5.4pt 0in 5.4pt;'><b>Operation</b>
|
||||
|
||||
@ -2,7 +2,8 @@
|
||||
title: Configure a test lab to deploy Windows 10
|
||||
ms.reviewer:
|
||||
manager: laurawi
|
||||
ms.audience: itpro
|
||||
ms.audience: itpro
|
||||
author: greg-lindsay
|
||||
description: Concepts and procedures for deploying Windows 10 in a proof of concept lab environment.
|
||||
ms.prod: w10
|
||||
ms.mktglfcycl: deploy
|
||||
@ -10,7 +11,8 @@ ms.sitesec: library
|
||||
ms.pagetype: deploy
|
||||
keywords: deployment, automate, tools, configure, mdt, sccm
|
||||
ms.localizationpriority: medium
|
||||
ms.localizationpriority: medium
|
||||
audience: itpro
|
||||
author: greg-lindsay
|
||||
ms.topic: article
|
||||
---
|
||||
|
||||
@ -50,7 +52,7 @@ Topics and procedures in this guide are summarized in the following table. An es
|
||||
<div style='font-size:9.0pt'>
|
||||
|
||||
<table border="1" cellspacing="0" cellpadding="0">
|
||||
|
||||
<tr><TD BGCOLOR="#a0e4fa"><font color="#000000"><B>Topic</B></font></td><TD BGCOLOR="#a0e4fa"><font color="#000000"><B>Description</B></font></td><TD BGCOLOR="#a0e4fa"><font color="#000000"><B>Time</B></font></td></tr>
|
||||
<tr><td><a href="#hardware-and-software-requirements" data-raw-source="[Hardware and software requirements](#hardware-and-software-requirements)">Hardware and software requirements</a><td>Prerequisites to complete this guide.<td>Informational
|
||||
<tr><td><a href="#lab-setup" data-raw-source="[Lab setup](#lab-setup)">Lab setup</a><td>A description and diagram of the PoC environment.<td>Informational
|
||||
<tr><td><a href="#configure-the-poc-environment" data-raw-source="[Configure the PoC environment](#configure-the-poc-environment)">Configure the PoC environment</a><td>Parent topic for procedures.<td>Informational
|
||||
@ -73,59 +75,59 @@ One computer that meets the hardware and software specifications below is requir
|
||||
- **Computer 1**: the computer you will use to run Hyper-V and host virtual machines. This computer should have 16 GB or more of installed RAM and a multi-core processor.
|
||||
- **Computer 2**: a client computer from your corporate network. It is shadow-copied to create a VM that can be added to the PoC environment, enabling you to test a mirror image of a computer on your network. If you do not have a computer to use for this simulation, you can download an evaluation VHD and use it to represent this computer. Subsequent guides use this computer to simulate Windows 10 replace and refresh scenarios, so the VM is required even if you cannot create this VM using computer 2.
|
||||
|
||||
- **Computer 2**: a client computer from your corporate network. It is shadow-copied to create a VM that can be added to the PoC environment, enabling you to test a mirror image of a computer on your network. If you do not have a computer to use for this simulation, you can download an evaluation VHD and use it to represent this computer. Subsequent guides use this computer to simulate Windows 10 replace and refresh scenarios, so the VM is required even if you cannot create this VM using computer 2.
|
||||
Hardware requirements are displayed below:
|
||||
|
||||
<div style='font-size:9.0pt'>
|
||||
|
||||
<table border="1" cellspacing="0" cellpadding="0">
|
||||
<tr>
|
||||
<td></td>
|
||||
<tr>
|
||||
<td></td>
|
||||
<td BGCOLOR="#a0e4fa"><strong><font color="#000000">Computer 1</strong> (required)</font></td>
|
||||
<td BGCOLOR="#a0e4fa"><strong><font color="#000000">Computer 2</strong> (recommended)</font></td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>Role</strong></font></td>
|
||||
<td>Hyper-V host</td>
|
||||
<td>Client computer</td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>Description</strong></font></td>
|
||||
<td>This computer will run Hyper-V, the Hyper-V management tools, and the Hyper-V Windows PowerShell module.</td>
|
||||
<td>This computer is a Windows 7 or Windows 8/8.1 client on your corporate network that will be converted to a VM to demonstrate the upgrade process.</td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>OS</strong></font></td>
|
||||
<td>Windows 8.1/10 or Windows Server 2012/2012 R2/2016<b>*</b></td>
|
||||
<td>Windows 7 or a later</td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>Edition</strong></font></td>
|
||||
<td>Enterprise, Professional, or Education</td>
|
||||
<td>Any</td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>Architecture</strong></font></td>
|
||||
<td>64-bit</td>
|
||||
<td>Any<BR><I>Note: Retaining applications and settings requires that architecture (32 or 64-bit) is the same before and after the upgrade.</I></td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>RAM</strong></font></td>
|
||||
<td>8 GB RAM (16 GB recommended) to test Windows 10 deployment with MDT.
|
||||
<BR>16 GB RAM to test Windows 10 deployment with System Center Configuration Manager.</td>
|
||||
<td>Any</td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>Disk</strong></font></td>
|
||||
<td>200 GB available hard disk space, any format.</td>
|
||||
<td>Any size, MBR formatted.</td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>CPU</strong></font></td>
|
||||
<td>SLAT-Capable CPU</td>
|
||||
<td>Any</td>
|
||||
</tr>
|
||||
<tr>
|
||||
</tr>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><strong>Network</strong></font></td>
|
||||
<td>Internet connection</td>
|
||||
<td>Any</td>
|
||||
</tr>
|
||||
@ -631,7 +633,7 @@ The second Windows Server 2012 R2 VHD needs to be expanded in size from 40GB to
|
||||
Dismount-VHD -Path c:\vhd\d.vhd
|
||||
</pre>
|
||||
|
||||
</pre>
|
||||
Next, create the PC1 VM with two attached VHDs, and boot to DVD ($maxram must be defined previously using the same Windows PowerShell prompt):
|
||||
|
||||
<pre style="overflow-y: visible">
|
||||
New-VM -Name "PC1" -VHDPath c:\vhd\w7.vhd -SwitchName poc-internal
|
||||
@ -821,7 +823,7 @@ The second Windows Server 2012 R2 VHD needs to be expanded in size from 40GB to
|
||||
|
||||
17. Open an elevated Windows PowerShell prompt on PC1 and verify that the client VM has received a DHCP lease and can communicate with the consoto.com domain controller.
|
||||
|
||||
17. Open an elevated Windows PowerShell prompt on PC1 and verify that the client VM has received a DHCP lease and can communicate with the consoto.com domain controller.
|
||||
To open Windows PowerShell on Windows 7, click **Start**, and search for "**power**." Right-click **Windows PowerShell** and then click **Pin to Taskbar** so that it is simpler to use Windows PowerShell during this lab. Click **Windows PowerShell** on the taskbar, and then type **ipconfig** at the prompt to see the client's current IP address. Also type **ping dc1.contoso.com** and **nltest /dsgetdc:contoso.com** to verify that it can reach the domain controller. See the following examples of a successful network connection:
|
||||
|
||||
```
|
||||
ipconfig
|
||||
@ -964,7 +966,7 @@ The second Windows Server 2012 R2 VHD needs to be expanded in size from 40GB to
|
||||
cmd /c netsh routing ip nat add interface name="Internal" mode=PRIVATE
|
||||
</pre>
|
||||
|
||||
</pre>
|
||||
32. The DNS service on SRV1 also needs to resolve hosts in the `contoso.com` domain. This can be accomplished with a conditional forwarder. Open an elevated Windows PowerShell prompt on SRV1 and type the following command:
|
||||
|
||||
<pre style="overflow-y: visible">
|
||||
Add-DnsServerConditionalForwarderZone -Name contoso.com -MasterServers 192.168.0.1
|
||||
@ -976,7 +978,7 @@ The second Windows Server 2012 R2 VHD needs to be expanded in size from 40GB to
|
||||
ping www.microsoft.com
|
||||
</pre>
|
||||
|
||||
</pre>
|
||||
If you see "Ping request could not find host `www.microsoft.com`" on PC1 and DC1, but not on SRV1, then you will need to configure a server-level DNS forwarder on SRV1. To do this, open an elevated Windows PowerShell prompt on SRV1 and type the following command.
|
||||
|
||||
**Note**: This command also assumes that "Ethernet 2" is the external-facing network adapter on SRV1. If the external adapter has a different name, replace "Ethernet 2" in the command below with that name:
|
||||
|
||||
@ -1032,10 +1034,10 @@ Use the following procedures to verify that the PoC environment is configured pr
|
||||
**DCDiag** displays "passed test" for all tests.<BR>
|
||||
**Get-DnsServerResourceRecord** displays the correct DNS address records for DC1, SRV1, and the computername of PC1. Additional address records for the zone apex (@), DomainDnsZones, and ForestDnsZones will also be registered.<BR>
|
||||
**Get-DnsServerForwarder** displays a single forwarder of 192.168.0.2.<BR>
|
||||
**Get-DnsServerResourceRecord** displays the correct DNS address records for DC1, SRV1, and the computername of PC1. Additional address records for the zone apex (@), DomainDnsZones, and ForestDnsZones will also be registered.<BR>
|
||||
**Get-DnsServerForwarder** displays a single forwarder of 192.168.0.2.<BR>
|
||||
**Resolve-DnsName** displays public IP address results for `www.microsoft.com`.<BR>
|
||||
**Get-DhcpServerInDC** displays 192.168.0.1, `dc1.contoso.com`.<BR>
|
||||
**Get-DhcpServerv4Statistics** displays 1 scope with 2 addresses in use (these belong to PC1 and the Hyper-V host).<BR>
|
||||
**Get-DhcpServerInDC** displays 192.168.0.1, dc1.contoso.com.<BR>
|
||||
**ipconfig** displays a primary DNS suffix and suffix search list of `contoso.com`, IP address of 192.168.0.1, subnet mask of 255.255.255.0, default gateway of 192.168.0.2, and DNS server addresses of 192.168.0.1 and 192.168.0.2.
|
||||
|
||||
2. On SRV1, open an elevated Windows PowerShell prompt and type the following commands:
|
||||
|
||||
@ -1049,8 +1051,8 @@ Use the following procedures to verify that the PoC environment is configured pr
|
||||
|
||||
**Get-Service** displays a status of "Running" for both services.<BR>
|
||||
**Get-DnsServerForwarder** either displays no forwarders, or displays a list of forwarders you are required to use so that SRV1 can resolve Internet names.<BR>
|
||||
**Get-Service** displays a status of "Running" for both services.<BR>
|
||||
**Get-DnsServerForwarder** either displays no forwarders, or displays a list of forwarders you are required to use so that SRV1 can resolve Internet names.<BR>
|
||||
**Resolve-DnsName** displays public IP address results for `www.microsoft.com`.<BR>
|
||||
**ipconfig** displays a primary DNS suffix of `contoso.com`. The suffix search list contains `contoso.com` and your corporate domain. Two ethernet adapters are shown: Ethernet adapter "Ethernet" has an IP addresses of 192.168.0.2, subnet mask of 255.255.255.0, no default gateway, and DNS server addresses of 192.168.0.1 and 192.168.0.2. Ethernet adapter "Ethernet 2" has an IP address, subnet mask, and default gateway configured by DHCP on your corporate network.<BR>
|
||||
**netsh** displays three interfaces on the computer: interface "Ethernet 2" with DHCP enabled = Yes and IP address assigned by your corporate network, interface "Ethernet" with DHCP enabled = No and IP address of 192.168.0.2, and interface "Loopback Pseudo-Interface 1" with IP address of 127.0.0.1.
|
||||
|
||||
3. On PC1, open an elevated Windows PowerShell prompt and type the following commands:
|
||||
@ -1065,9 +1067,9 @@ Use the following procedures to verify that the PoC environment is configured pr
|
||||
|
||||
**whoami** displays the current user context, for example in an elevated Windows PowerShell prompt, contoso\administrator is displayed.<BR>
|
||||
**hostname** displays the name of the local computer, for example W7PC-001.<BR>
|
||||
**whoami** displays the current user context, for example in an elevated Windows PowerShell prompt, contoso\administrator is displayed.<BR>
|
||||
**hostname** displays the name of the local computer, for example W7PC-001.<BR>
|
||||
**nslookup** displays the DNS server used for the query, and the results of the query. For example, server dc1.contoso.com, address 192.168.0.1, Name e2847.dspb.akamaiedge.net.<BR>
|
||||
**nslookup** displays the DNS server used for the query, and the results of the query. For example, server `dc1.contoso.com`, address 192.168.0.1, Name `e2847.dspb.akamaiedge.net`.<BR>
|
||||
**ping** displays if the source can resolve the target name, and whether or not the target responds to ICMP. If it cannot be resolved, "..could not find host" will be displayed and if the target is found and also responds to ICMP, you will see "Reply from" and the IP address of the target.<BR>
|
||||
**tracert** displays the path to reach the destination, for example `srv1.contoso.com` [192.168.0.2] followed by a list of hosts and IP addresses corresponding to subsequent routing nodes between the source and the destination.
|
||||
|
||||
|
||||
## Appendix B: Terminology used in this guide
|
||||
@ -1077,7 +1079,8 @@ Use the following procedures to verify that the PoC environment is configured pr
|
||||
<div style='font-size:9.0pt'>
|
||||
|
||||
<table border="1" cellspacing="0" cellpadding="0">
|
||||
|
||||
<tr><TD BGCOLOR="#a0e4fa"><font color="#000000"><B>Term</B></font>
|
||||
<TD BGCOLOR="#a0e4fa"><font color="#000000"><B>Definition</B></font>
|
||||
<tr><td>GPT<td>GUID partition table (GPT) is an updated hard-disk formatting scheme that enables the use of newer hardware. GPT is one of the partition formats that can be chosen when first initializing a hard drive, prior to creating and formatting partitions.
|
||||
<tr><td>Hyper-V<td>Hyper-V is a server role introduced with Windows Server 2008 that lets you create a virtualized computing environment. Hyper-V can also be installed as a Windows feature on Windows client operating systems, starting with Windows 8.
|
||||
<tr><td>Hyper-V host<td>The computer where Hyper-V is installed.
|
||||
|
||||
@ -104,13 +104,13 @@ Once the hardware IDs have been captured from existing devices, they can be uplo
|
||||
- [Microsoft Store for Business](https://docs.microsoft.com/microsoft-store/add-profile-to-devices#manage-autopilot-deployment-profiles). You might already be using MSfB to manage your apps and settings.
|
||||
|
||||
A summary of each platform's capabilities is provided below.
|
||||
|
||||
<br>
|
||||
<table>
|
||||
<tr>
|
||||
<td BGCOLOR="#a0e4fa"><B>Platform/Portal</th>
|
||||
<td BGCOLOR="#a0e4fa"><B>Register devices?</th>
|
||||
<td BGCOLOR="#a0e4fa"><B>Create/Assign profile</th>
|
||||
<td BGCOLOR="#a0e4fa"><B>Acceptable DeviceID</th>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Platform/Portal</font></td>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Register devices?</font></td>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Create/Assign profile</font></td>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Acceptable DeviceID</font></td>
|
||||
</tr>
|
||||
|
||||
<tr>
|
||||
|
||||
@ -68,15 +68,16 @@ See the following examples.
|
||||
Install-PackageProvider -Name NuGet -MinimumVersion 2.8.5.201 -Force
|
||||
Install-Module AzureAD -Force
|
||||
Install-Module WindowsAutopilotIntune -Force
|
||||
Install-Module Microsoft.Graph.Intune -Force
|
||||
```
|
||||
|
||||
3. Enter the following lines and provide Intune administrative credentials
|
||||
- In the following command, replace the example user principal name for Azure authentication (admin@M365x373186.onmicrosoft.com) with your user account. Be sure that the user account you specify has sufficient administrative rights.
|
||||
- Be sure that the user account you specify has sufficient administrative rights.
|
||||
|
||||
```powershell
|
||||
Connect-MSGraph -user admin@M365x373186.onmicrosoft.com
|
||||
Connect-MSGraph
|
||||
```
|
||||
The password for your account will be requested using a standard Azure AD form. Type your password and then click **Sign in**.
|
||||
The user and password for your account will be requested using a standard Azure AD form. Type your username and password and then click **Sign in**.
|
||||
<br>See the following example:
|
||||
|
||||

|
||||
|
||||
@ -289,6 +289,16 @@ Capability Security Identifiers (SIDs) are used to uniquely and immutably identi
|
||||
|
||||
All Capability SIDs that the operating system is aware of are stored in the Windows Registry in the path `HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities'. Any Capability SID added to Windows by first or third-party applications will be added to this location.
|
||||
|
||||
## Examples of registry keys taken from Windows 10, version 1909, 64-bit Enterprise edition
|
||||
You may see the following registry keys under AllCachedCapabilities:
|
||||
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_DevUnlock
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_DevUnlock_Internal
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_Enterprise
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_General
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_Restricted
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_Windows
|
||||
|
||||
All Capability SIDs are prefixed by S-1-15-3
|
||||
|
||||
## See also
|
||||
|
||||
@ -129,7 +129,7 @@
|
||||
##### [DeviceTvmSecureConfigurationAssessment](microsoft-defender-atp/advanced-hunting-tvm-configassessment-table.md)
|
||||
##### [DeviceTvmSecureConfigurationAssessmentKB](microsoft-defender-atp/advanced-hunting-tvm-secureconfigkb-table.md)
|
||||
#### [Apply query best practices](microsoft-defender-atp/advanced-hunting-best-practices.md)
|
||||
#### [Stream advanced hunting events to Azure Event Hubs](microsoft-defender-atp/raw-data-export-event-hub.md)
|
||||
|
||||
|
||||
#### [Custom detections]()
|
||||
##### [Understand custom detection rules](microsoft-defender-atp/overview-custom-detections.md)
|
||||
@ -137,8 +137,6 @@
|
||||
|
||||
### [Management and APIs]()
|
||||
#### [Overview of management and APIs](microsoft-defender-atp/management-apis.md)
|
||||
#### [Understand threat intelligence concepts](microsoft-defender-atp/threat-indicator-concepts.md)
|
||||
#### [Managed security service provider support](microsoft-defender-atp/mssp-support.md)
|
||||
|
||||
### [Integrations]()
|
||||
#### [Microsoft Defender ATP integrations](microsoft-defender-atp/threat-protection-integration.md)
|
||||
@ -362,15 +360,15 @@
|
||||
###### [Troubleshoot subscription and portal access issues](microsoft-defender-atp/troubleshoot-onboarding-error-messages.md)
|
||||
|
||||
#### [Microsoft Defender ATP API]()
|
||||
##### [Microsoft Defender ATP API license and terms](microsoft-defender-atp/api-terms-of-use.md)
|
||||
##### [Get started with Microsoft Defender ATP APIs]()
|
||||
###### [Introduction](microsoft-defender-atp/apis-intro.md)
|
||||
###### [Microsoft Defender ATP API license and terms](microsoft-defender-atp/api-terms-of-use.md)
|
||||
###### [Access the Microsoft Defender ATP APIs](microsoft-defender-atp/apis-intro.md)
|
||||
###### [Hello World](microsoft-defender-atp/api-hello-world.md)
|
||||
###### [Get access with application context](microsoft-defender-atp/exposed-apis-create-app-webapp.md)
|
||||
###### [Get access with user context](microsoft-defender-atp/exposed-apis-create-app-nativeapp.md)
|
||||
###### [Get partner application access](microsoft-defender-atp/exposed-apis-create-app-partners.md)
|
||||
|
||||
##### [APIs]()
|
||||
##### [Microsoft Defender ATP APIs Schema]()
|
||||
###### [Supported Microsoft Defender ATP APIs](microsoft-defender-atp/exposed-apis-list.md)
|
||||
###### [Advanced Hunting](microsoft-defender-atp/run-advanced-query-api.md)
|
||||
|
||||
@ -444,14 +442,14 @@
|
||||
###### [Advanced Hunting using PowerShell](microsoft-defender-atp/run-advanced-query-sample-powershell.md)
|
||||
###### [Using OData Queries](microsoft-defender-atp/exposed-apis-odata-samples.md)
|
||||
|
||||
#### [Windows updates (KB) info]()
|
||||
##### [Get KbInfo collection](microsoft-defender-atp/get-kbinfo-collection.md)
|
||||
|
||||
#### [Common Vulnerabilities and Exposures (CVE) to KB map]()
|
||||
##### [Get CVE-KB map](microsoft-defender-atp/get-cvekbmap-collection.md)
|
||||
#### [Raw data streaming API]()
|
||||
##### [Raw data streaming (preview)](microsoft-defender-atp/raw-data-export.md)
|
||||
##### [Stream advanced hunting events to Azure Events hub](microsoft-defender-atp/raw-data-export-event-hub.md)
|
||||
##### [Stream advanced hunting events to your storage account](microsoft-defender-atp/raw-data-export-storage.md)
|
||||
|
||||
|
||||
#### [Pull detections to your SIEM tools]()
|
||||
#### [SIEM integration]()
|
||||
##### [Understand threat intelligence concepts](microsoft-defender-atp/threat-indicator-concepts.md)
|
||||
##### [Learn about different ways to pull detections](microsoft-defender-atp/configure-siem.md)
|
||||
##### [Enable SIEM integration](microsoft-defender-atp/enable-siem-integration.md)
|
||||
##### [Configure Splunk to pull detections](microsoft-defender-atp/configure-splunk.md)
|
||||
@ -460,6 +458,7 @@
|
||||
##### [Pull detections using SIEM REST API](microsoft-defender-atp/pull-alerts-using-rest-api.md)
|
||||
##### [Troubleshoot SIEM tool integration issues](microsoft-defender-atp/troubleshoot-siem.md)
|
||||
|
||||
|
||||
#### [Reporting]()
|
||||
##### [Power BI - How to use API - Samples](microsoft-defender-atp/api-power-bi.md)
|
||||
##### [Create and build Power BI reports using Microsoft Defender ATP data connectors (deprecated)](microsoft-defender-atp/powerbi-reports.md)
|
||||
@ -486,45 +485,55 @@
|
||||
###### [Using machine groups](microsoft-defender-atp/machine-groups.md)
|
||||
###### [Create and manage machine tags](microsoft-defender-atp/machine-tags.md)
|
||||
|
||||
#### [Configure managed security service provider (MSSP) support](microsoft-defender-atp/configure-mssp-support.md)
|
||||
#### [Configure managed security service provider (MSSP) integration](microsoft-defender-atp/configure-mssp-support.md)
|
||||
|
||||
## [Partner integration scenarios]()
|
||||
### [Technical partner opportunities](microsoft-defender-atp/partner-integration.md)
|
||||
### [Managed security service provider opportunity](microsoft-defender-atp/mssp-support.md)
|
||||
### [Become a Microsoft Defender ATP partner](microsoft-defender-atp/get-started-partner-integration.md)
|
||||
|
||||
|
||||
### [Configure Microsoft threat protection integration]()
|
||||
#### [Configure conditional access](microsoft-defender-atp/configure-conditional-access.md)
|
||||
#### [Configure Microsoft Cloud App Security integration](microsoft-defender-atp/microsoft-cloud-app-security-config.md)
|
||||
#### [Configure information protection in Windows](microsoft-defender-atp/information-protection-in-windows-config.md)
|
||||
## [Configure Microsoft threat protection integration]()
|
||||
### [Configure conditional access](microsoft-defender-atp/configure-conditional-access.md)
|
||||
### [Configure Microsoft Cloud App Security integration](microsoft-defender-atp/microsoft-cloud-app-security-config.md)
|
||||
### [Configure information protection in Windows](microsoft-defender-atp/information-protection-in-windows-config.md)
|
||||
|
||||
### [Configure portal settings]()
|
||||
#### [Set up preferences](microsoft-defender-atp/preferences-setup.md)
|
||||
#### [General]()
|
||||
##### [Update data retention settings](microsoft-defender-atp/data-retention-settings.md)
|
||||
##### [Configure alert notifications](microsoft-defender-atp/configure-email-notifications.md)
|
||||
##### [Enable and create Power BI reports using Windows Defender Security center data](microsoft-defender-atp/powerbi-reports.md)
|
||||
##### [Enable Secure score security controls](microsoft-defender-atp/enable-secure-score.md)
|
||||
##### [Configure advanced features](microsoft-defender-atp/advanced-features.md)
|
||||
## [Configure portal settings]()
|
||||
### [Set up preferences](microsoft-defender-atp/preferences-setup.md)
|
||||
### [General]()
|
||||
#### [Update data retention settings](microsoft-defender-atp/data-retention-settings.md)
|
||||
#### [Configure alert notifications](microsoft-defender-atp/configure-email-notifications.md)
|
||||
#### [Enable and create Power BI reports using Windows Defender Security center data](microsoft-defender-atp/powerbi-reports.md)
|
||||
#### [Enable Secure score security controls](microsoft-defender-atp/enable-secure-score.md)
|
||||
#### [Configure advanced features](microsoft-defender-atp/advanced-features.md)
|
||||
|
||||
### [Permissions]()
|
||||
#### [Use basic permissions to access the portal](microsoft-defender-atp/basic-permissions.md)
|
||||
#### [Manage portal access using RBAC](microsoft-defender-atp/rbac.md)
|
||||
##### [Create and manage roles](microsoft-defender-atp/user-roles.md)
|
||||
##### [Create and manage machine groups](microsoft-defender-atp/machine-groups.md)
|
||||
###### [Create and manage machine tags](microsoft-defender-atp/machine-tags.md)
|
||||
|
||||
### [APIs]()
|
||||
#### [Enable Threat intel (Deprecated)](microsoft-defender-atp/enable-custom-ti.md)
|
||||
#### [Enable SIEM integration](microsoft-defender-atp/enable-siem-integration.md)
|
||||
|
||||
### [Rules]()
|
||||
#### [Manage suppression rules](microsoft-defender-atp/manage-suppression-rules.md)
|
||||
#### [Manage indicators](microsoft-defender-atp/manage-indicators.md)
|
||||
#### [Manage automation file uploads](microsoft-defender-atp/manage-automation-file-uploads.md)
|
||||
#### [Manage automation folder exclusions](microsoft-defender-atp/manage-automation-folder-exclusions.md)
|
||||
|
||||
### [Machine management]()
|
||||
#### [Onboarding machines](microsoft-defender-atp/onboard-configure.md)
|
||||
#### [Offboarding machines](microsoft-defender-atp/offboard-machines.md)
|
||||
|
||||
### [Configure Microsoft Defender Security Center time zone settings](microsoft-defender-atp/time-settings.md)
|
||||
|
||||
#### [Permissions]()
|
||||
##### [Use basic permissions to access the portal](microsoft-defender-atp/basic-permissions.md)
|
||||
##### [Manage portal access using RBAC](microsoft-defender-atp/rbac.md)
|
||||
###### [Create and manage roles](microsoft-defender-atp/user-roles.md)
|
||||
###### [Create and manage machine groups](microsoft-defender-atp/machine-groups.md)
|
||||
####### [Create and manage machine tags](microsoft-defender-atp/machine-tags.md)
|
||||
|
||||
#### [APIs]()
|
||||
##### [Enable Threat intel (Deprecated)](microsoft-defender-atp/enable-custom-ti.md)
|
||||
##### [Enable SIEM integration](microsoft-defender-atp/enable-siem-integration.md)
|
||||
|
||||
#### [Rules]()
|
||||
##### [Manage suppression rules](microsoft-defender-atp/manage-suppression-rules.md)
|
||||
##### [Manage indicators](microsoft-defender-atp/manage-indicators.md)
|
||||
##### [Manage automation file uploads](microsoft-defender-atp/manage-automation-file-uploads.md)
|
||||
##### [Manage automation folder exclusions](microsoft-defender-atp/manage-automation-folder-exclusions.md)
|
||||
|
||||
#### [Machine management]()
|
||||
##### [Onboarding machines](microsoft-defender-atp/onboard-configure.md)
|
||||
##### [Offboarding machines](microsoft-defender-atp/offboard-machines.md)
|
||||
|
||||
#### [Configure Microsoft Defender Security Center time zone settings](microsoft-defender-atp/time-settings.md)
|
||||
|
||||
|
||||
## [Troubleshoot Microsoft Defender ATP]()
|
||||
|
||||
@ -184,6 +184,7 @@ The most common values:
|
||||
| 2 | PA-ENC-TIMESTAMP | This is a normal type for standard password authentication. |
|
||||
| 11 | PA-ETYPE-INFO | The ETYPE-INFO pre-authentication type is sent by the KDC in a KRB-ERROR indicating a requirement for additional pre-authentication. It is usually used to notify a client of which key to use for the encryption of an encrypted timestamp for the purposes of sending a PA-ENC-TIMESTAMP pre-authentication value.<br>Never saw this Pre-Authentication Type in Microsoft Active Directory environment. |
|
||||
| 15 | PA-PK-AS-REP\_OLD | Used for Smart Card logon authentication. |
|
||||
| 16 | PA-PK-AS-REQ | Request sent to KDC in Smart Card authentication scenarios.|
|
||||
| 17 | PA-PK-AS-REP | This type should also be used for Smart Card authentication, but in certain Active Directory environments, it is never seen. |
|
||||
| 19 | PA-ETYPE-INFO2 | The ETYPE-INFO2 pre-authentication type is sent by the KDC in a KRB-ERROR indicating a requirement for additional pre-authentication. It is usually used to notify a client of which key to use for the encryption of an encrypted timestamp for the purposes of sending a PA-ENC-TIMESTAMP pre-authentication value.<br>Never saw this Pre-Authentication Type in Microsoft Active Directory environment. |
|
||||
| 20 | PA-SVR-REFERRAL-INFO | Used in KDC Referrals tickets. |
|
||||
|
||||
@ -126,8 +126,9 @@ This event is always logged regardless of the "Audit Policy Change" sub-category
|
||||
|
||||
- **Subcategory** \[Type = UnicodeString\]**:** the name of auditing subcategory which state was changed. Possible values:
|
||||
|
||||
| Audit Credential Validation | Audit Process Termination | Audit Other Logon/Logoff Events |
|
||||
| Value | Value | Value |
|
||||
|------------------------------------------|----------------------------------------------|--------------------------------------|
|
||||
| Audit Credential Validation | Audit Process Termination | Audit Other Logon/Logoff Events |
|
||||
| Audit Kerberos Authentication Service | Audit RPC Events | Audit Special Logon |
|
||||
| Audit Kerberos Service Ticket Operations | Audit Detailed Directory Service Replication | Audit Application Generated |
|
||||
| Audit Other Logon/Logoff Events | Audit Directory Service Access | Audit Certification Services |
|
||||
@ -145,7 +146,7 @@ This event is always logged regardless of the "Audit Policy Change" sub-category
|
||||
| Audit Policy Change | Audit Non-Sensitive Privilege Use | Audit System Integrity |
|
||||
| Audit Authentication Policy Change | Audit Sensitive Privilege Use | Audit PNP Activity |
|
||||
| Audit Authorization Policy Change | Audit Other Privilege Use Events | |
|
||||
| Group Membership | Audit Network Policy Server | |
|
||||
| Audit Group Membership | Audit Network Policy Server | |
|
||||
|
||||
- **Subcategory GUID** \[Type = GUID\]**:** the unique GUID of changed subcategory.
|
||||
|
||||
|
||||
|
After Width: | Height: | Size: 30 KiB |
@ -1,5 +1,5 @@
|
||||
---
|
||||
title: Microsoft Defender Advanced Threat Protection API overview
|
||||
title: Access the Microsoft Defender Advanced Threat Protection APIs
|
||||
ms.reviewer:
|
||||
description: Learn how you can use APIs to automate workflows and innovate based on Microsoft Defender ATP capabilities
|
||||
keywords: apis, api, wdatp, open api, windows defender atp api, public api, supported apis, alerts, machine, user, domain, ip, file, advanced hunting, query
|
||||
@ -17,7 +17,7 @@ ms.collection: M365-security-compliance
|
||||
ms.topic: conceptual
|
||||
---
|
||||
|
||||
# Microsoft Defender ATP API overview
|
||||
# Access the Microsoft Defender Advanced Threat Protection APIs
|
||||
|
||||
**Applies to:**
|
||||
- [Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP)](https://go.microsoft.com/fwlink/p/?linkid=2069559)
|
||||
|
||||
@ -15,7 +15,6 @@ manager: dansimp
|
||||
audience: ITPro
|
||||
ms.collection: M365-security-compliance
|
||||
ms.topic: article
|
||||
ms.date: 10/16/2017
|
||||
---
|
||||
|
||||
# Pull detections to your SIEM tools
|
||||
@ -56,13 +55,3 @@ Microsoft Defender ATP supports the OAuth 2.0 protocol to pull detections using
|
||||
For more information, see [Pull Microsoft Defender ATP detections using REST API](pull-alerts-using-rest-api.md).
|
||||
|
||||
|
||||
## In this section
|
||||
|
||||
Topic | Description
|
||||
:---|:---
|
||||
[Enable SIEM integration in Microsoft Defender ATP](enable-siem-integration.md)| Learn about enabling the SIEM integration feature in the **Settings** page in the portal so that you can use and generate the required information to configure supported SIEM tools.
|
||||
[Configure Splunk to pull Microsoft Defender ATP detections](configure-splunk.md)| Learn about installing the REST API Modular Input App and other configuration settings to enable Splunk to pull Microsoft Defender ATP detections.
|
||||
[Configure HP ArcSight to pull Microsoft Defender ATP detections](configure-arcsight.md)| Learn about installing the HP ArcSight REST FlexConnector package and the files you need to configure ArcSight to pull Microsoft Defender ATP detections.
|
||||
[Microsoft Defender ATP Detection fields](api-portal-mapping.md) | Understand what data fields are exposed as part of the alerts API and how they map to Microsoft Defender Security Center.
|
||||
[Pull Microsoft Defender ATP detections using REST API](pull-alerts-using-rest-api.md) | Use the Client credentials OAuth 2.0 flow to pull detections from Microsoft Defender ATP using REST API.
|
||||
[Troubleshoot SIEM tool integration issues](troubleshoot-siem.md) | Address issues you might encounter when using the SIEM integration feature.
|
||||
|
||||
@ -130,7 +130,7 @@ h. Select **Manage > Assignments**. In the **Include** tab, select *
|
||||
In terminal, run:
|
||||
|
||||
```bash
|
||||
mdatp --edr --earlypreview true
|
||||
mdatp --edr --early-preview true
|
||||
```
|
||||
|
||||
For versions earlier than 100.78.0, run:
|
||||
|
||||
@ -0,0 +1,54 @@
|
||||
---
|
||||
title: Become a Microsoft Defender ATP partner
|
||||
ms.reviewer:
|
||||
description: Learn the steps and requirements so that you can integrate your solution with Microsoft Defender ATP and be a partner
|
||||
keywords: partner, integration, solution validation, certification, requirements, member, misa, application portal
|
||||
search.product: eADQiWindows 10XVcnh
|
||||
search.appverid: met150
|
||||
ms.prod: w10
|
||||
ms.mktglfcycl: deploy
|
||||
ms.sitesec: library
|
||||
ms.pagetype: security
|
||||
ms.author: macapara
|
||||
author: mjcaparas
|
||||
ms.localizationpriority: medium
|
||||
manager: dansimp
|
||||
audience: ITPro
|
||||
ms.collection: M365-security-compliance
|
||||
ms.topic: conceptual
|
||||
---
|
||||
|
||||
# Become a Microsoft Defender ATP partner
|
||||
|
||||
**Applies to:**
|
||||
- [Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP)](https://go.microsoft.com/fwlink/p/?linkid=2069559)
|
||||
|
||||
To become a Microsoft Defender ATP solution partner, you'll need to follow and complete the following steps.
|
||||
|
||||
## Step 1: Subscribe to a Microsoft Defender ATP Developer license
|
||||
Subscribing to the [Microsoft Defender ATP Developer license](https://winatpregistration-prd.trafficmanager.net/Developer/UserAgreement?Length=9) allows you to use a Microsoft Defender ATP tenant with up to 10 devices for developing solutions to integrate with Microsoft Defender ATP.
|
||||
|
||||
## Step 2: Fulfill the solution validation and certification requirements
|
||||
The best way for technology partners to certify their integration works, is to have a joint customer approve the suggested integration design and have it tested and demoed to the Microsoft Defender ATP team.
|
||||
|
||||
Once the Microsoft Defender ATP team has reviewed and approves the integration, we will direct you to be included as a partner at the Microsoft Intelligent Security Association.
|
||||
|
||||
## Step 3: Become a Microsoft Intelligent Security Association member
|
||||
[Microsoft Intelligent Security Association](https://www.microsoft.com/security/partnerships/intelligent-security-association) is a program specifically for Microsoft security partners to help enrich your security products and improve customer discoverability of your integrations to Microsoft security products.
|
||||
|
||||
## Step 4: Get listed in the Microsoft Defender ATP partner application portal
|
||||
Microsoft Defender ATP supports third-party applications discovery and integration using the in-product [partner page](partner-applications.md) that is embedded within the Microsoft Defender ATP management portal.
|
||||
|
||||
To have your company listed as a partner in the in-product partner page, you will need to provide the following:
|
||||
|
||||
1. A square logo (SVG).
|
||||
2. Name of the product to be presented.
|
||||
3. Provide a 15-word product description.
|
||||
4. Link to the landing page for the customer to complete the integration or blog post that will include sufficient information for customers. Please note that any press release including the Microsoft Defender ATP product name should be reviewed by the marketing and engineering teams. You should allow at least 10 days for review process to be performed.
|
||||
5. If you use a multi-tenant Azure AD approach, we will need the AAD application name to track usage of the application.
|
||||
|
||||
|
||||
Partnership with Microsoft Defender ATP help our mutual customers to further streamline, integrate, and orchestrate defenses. We are happy that you chose to become a Microsoft Defender ATP partner and to achieve our common goal of effectively protecting customers and their assets by preventing and responding to modern threats together.
|
||||
|
||||
## Related topics
|
||||
- [Technical partner opportunities](partner-integration.md)
|
||||
|
After Width: | Height: | Size: 102 KiB |
|
After Width: | Height: | Size: 84 KiB |
|
After Width: | Height: | Size: 99 KiB |
|
After Width: | Height: | Size: 69 KiB |
|
After Width: | Height: | Size: 62 KiB |
@ -225,7 +225,7 @@ $ mdatp --health healthy
|
||||
The above command prints "1" if the product is onboarded and functioning as expected.
|
||||
|
||||
If the product is not healthy, the exit code (which can be checked through `echo $?`) indicates the problem:
|
||||
- 1 if the device is not yet onboarded
|
||||
- 0 if the device is not yet onboarded
|
||||
- 3 if the connection to the daemon cannot be established—for example, if the daemon is not running
|
||||
|
||||
## Logging installation issues
|
||||
|
||||
@ -371,10 +371,6 @@ The following configuration profile will:
|
||||
### Intune profile
|
||||
|
||||
```XML
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
|
||||
<plist version="1">
|
||||
<dict>
|
||||
<key>PayloadUUID</key>
|
||||
<string>C4E6A782-0C8D-44AB-A025-EB893987A295</string>
|
||||
<key>PayloadType</key>
|
||||
@ -443,8 +439,6 @@ The following configuration profile will:
|
||||
</dict>
|
||||
</dict>
|
||||
</array>
|
||||
</dict>
|
||||
</plist>
|
||||
```
|
||||
|
||||
## Full configuration profile example
|
||||
@ -530,10 +524,6 @@ The following configuration profile contains entries for all settings described
|
||||
### Intune profile
|
||||
|
||||
```XML
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
|
||||
<plist version="1">
|
||||
<dict>
|
||||
<key>PayloadUUID</key>
|
||||
<string>C4E6A782-0C8D-44AB-A025-EB893987A295</string>
|
||||
<key>PayloadType</key>
|
||||
@ -640,8 +630,6 @@ The following configuration profile contains entries for all settings described
|
||||
</dict>
|
||||
</dict>
|
||||
</array>
|
||||
</dict>
|
||||
</plist>
|
||||
```
|
||||
|
||||
## Configuration profile deployment
|
||||
|
||||
@ -1,8 +1,8 @@
|
||||
---
|
||||
title: Overview of management and APIs
|
||||
ms.reviewer:
|
||||
description:
|
||||
keywords:
|
||||
description: Learn about the management tools and API categories in Microsoft Defender ATP
|
||||
keywords: onboarding, api, siem, rbac, access, portal, integration, investigation, response, entities, entity, user context, application context, streaming
|
||||
search.product: eADQiWindows 10XVcnh
|
||||
search.appverid: met150
|
||||
ms.prod: w10
|
||||
@ -29,40 +29,51 @@ Microsoft Defender ATP supports a wide variety of options to ensure that custome
|
||||
|
||||
Acknowledging that customer environments and structures can vary, Microsoft Defender ATP was created with flexibility and granular control to fit varying customer requirements.
|
||||
|
||||
## Endpoint onboarding and portal access
|
||||
|
||||
Machine onboarding is fully integrated into System Center Configuration Manager and Microsoft Intune for client machines and Azure Security Center for server machines, providing complete end-to-end experience of configuration, deployment, and monitoring. In addition, Microsoft Defender ATP supports Group Policy and other third-party tools used for machines management.
|
||||
|
||||
Microsoft Defender ATP provides fine-grained control over what users with access to the portal can see and do through the flexibility of role-based access control (RBAC). The RBAC model supports all flavors of security teams structure:
|
||||
- Globally distributed organizations and security teams
|
||||
- Tiered model security operations teams
|
||||
- Fully segregated devisions with single centralized global security operations teams
|
||||
- Fully segregated divisions with single centralized global security operations teams
|
||||
|
||||
The Microsoft Defender ATP solution is built on top of an integration-ready platform:
|
||||
- It supports integration with a number of security information and event management (SIEM) solutions and also exposes APIs to fully support pulling all the alerts and detection information into any SIEM solution.
|
||||
- It supports a rich set of application programming interface (APIs) providing flexibility for those who are already heavily invested in data enrichment and automation:
|
||||
- Enriching events coming from other security systems with foot print or prevalence information
|
||||
- Triggering file or machine level response actions through APIs
|
||||
- Keeping systems in-sync such as importing machine tags from asset management systems into Microsoft Defender ATP, synchronize alerts and incidents status cross ticketing systems with Microsoft Defender ATP.
|
||||
## Available APIs
|
||||
The Microsoft Defender ATP solution is built on top of an integration-ready platform.
|
||||
|
||||
An important aspect of machine management is the ability to analyze the environment from varying and broad perspectives. This often helps drive new insights and proper priority identification:
|
||||
- The Secure score dashboard provides metrics based method of prioritizing the most important proactive security measures.
|
||||
- Microsoft Defender ATP includes a built-in PowerBI based reporting solution to quickly review trends and details related to Microsoft Defender ATP alerts and secure score of machines. The platform also supports full customization of the reports, including mashing of Microsoft Defender ATP data with your own data stream to produce business specific reports.
|
||||
Microsoft Defender ATP exposes much of its data and actions through a set of programmatic APIs. Those APIs will enable you to automate workflows and innovate based on Microsoft Defender ATP capabilities.
|
||||
|
||||

|
||||
|
||||
The Microsoft Defender ATP APIs can be grouped into three:
|
||||
- Microsoft Defender ATP APIs
|
||||
- Raw data streaming API
|
||||
- SIEM integration
|
||||
|
||||
|
||||
## In this section
|
||||
Topic | Description
|
||||
:---|:---
|
||||
Understand threat intelligence concepts | Learn about alert definitions, indicators of compromise, and other threat intelligence concepts.
|
||||
Managed security service provider | Get a quick overview on managed security service provider support.
|
||||
## Microsoft Defender ATP APIs
|
||||
|
||||
Microsoft Defender ATP offers a layered API model exposing data and capabilities in a structured, clear and easy to use model, exposed through a standard Azure AD-based authentication and authorization model allowing access in context of users or SaaS applications. The API model was designed to expose entities and capabilities in a consistent form.
|
||||
|
||||
The **Investigation API** exposes the richness of Microsoft Defender ATP - exposing calculated or 'profiled' entities (for example, machine, user, and file) and discrete events (for example, process creation and file creation) which typically describes a behavior related to an entity, enabling access to data via investigation interfaces allowing a query-based access to data. For more information see, [Supported APIs](exposed-apis-list.md).
|
||||
|
||||
The **Response API** exposes the ability to take actions in the service and on devices, enabling customers to ingest indicators, manage settings, alert status, as well as take response actions on devices programmatically such as isolate machines from the network, quarantine files, and others.
|
||||
|
||||
## Raw data streaming API
|
||||
Microsoft Defender ATP raw data streaming API provides the ability for customers to ship real-time events and alerts from their instances as they occur within a single data stream, providing a low latency, high throughput delivery mechanism.
|
||||
|
||||
The Microsoft Defender ATP event information is pushed directly to Azure storage for long-term data retention, or to Azure Event Hubs for consumption by visualization services or additional data processing engines.
|
||||
|
||||
For more information see, [Raw data streaming API](raw-data-export.md).
|
||||
|
||||
|
||||
## SIEM API
|
||||
When you enable security information and event management (SIEM) integration it allows you to pull detections from Microsoft Defender Security Center using your SIEM solution or by connecting directly to the detections REST API. This activates the SIEM connector access details section with pre-populated values and an application is created under you Azure Active Directory (AAD) tenant. For more information see, [SIEM integration](enable-siem-integration.md)
|
||||
|
||||
|
||||
## Related topics
|
||||
- [Onboard machines](onboard-configure.md)
|
||||
- [Enable the custom threat intelligence application](enable-custom-ti.md)
|
||||
- [Microsoft Defender ATP Public API](apis-intro.md)
|
||||
- [Pull alerts to your SIEM tools](configure-siem.md)
|
||||
- [Create and build Power BI reports using Microsoft Defender ATP data](powerbi-reports.md)
|
||||
- [Role-based access control](rbac.md)
|
||||
- [Access the Microsoft Defender Advanced Threat Protection APIs ](apis-intro.md)
|
||||
- [Supported APIs](exposed-apis-list.md)
|
||||
- [Technical partner opportunities](partner-integration.md)
|
||||
|
||||
|
||||
|
||||
@ -174,6 +174,9 @@ When Windows Defender Antivirus is not the active antimalware in your organizati
|
||||
|
||||
If you are onboarding servers and Windows Defender Antivirus is not the active antimalware on your servers, you shouldn't uninstall Windows Defender Antivirus. You'll need to configure it to run on passive mode. For more information, see [Onboard servers](configure-server-endpoints.md).
|
||||
|
||||
> [!NOTE]
|
||||
> Your regular group policy doesn’t apply to Tamper Protection, and changes to Windows Defender Antivirus settings will be ignored when Tamper Protection is on.
|
||||
|
||||
|
||||
For more information, see [Windows Defender Antivirus compatibility](../windows-defender-antivirus/windows-defender-antivirus-compatibility.md).
|
||||
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
---
|
||||
title: Managed security service provider (MSSP) support
|
||||
title: Managed security service provider (MSSP) partnership opportunities
|
||||
description: Understand how Microsoft Defender ATP integrates with managed security service providers (MSSP)
|
||||
keywords: mssp, integration, managed, security, service, provider
|
||||
search.product: eADQiWindows 10XVcnh
|
||||
@ -17,7 +17,7 @@ ms.collection: M365-security-compliance
|
||||
ms.topic: conceptual
|
||||
---
|
||||
|
||||
# Managed security service provider support
|
||||
# Managed security service provider partnership opportunities
|
||||
|
||||
**Applies to:**
|
||||
- [Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP)](https://go.microsoft.com/fwlink/p/?linkid=2069559)
|
||||
@ -25,14 +25,13 @@ ms.topic: conceptual
|
||||
>Want to experience Microsoft Defender ATP? [Sign up for a free trial.](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp?ocid=docs-mssp-support-abovefoldlink)
|
||||
|
||||
|
||||
|
||||
Security is recognized as a key component in running an enterprise, however some organizations might not have the capacity or expertise to have a dedicated security operations team to manage the security of their endpoints and network, others may want to have a second set of eyes to review alerts in their network.
|
||||
|
||||
|
||||
To address this demand, managed security service providers (MSSP) offer to deliver managed detection and response (MDR) services on top of Microsoft Defender ATP.
|
||||
|
||||
|
||||
Microsoft Defender ATP adds support for this scenario and to allow MSSPs to take the following actions:
|
||||
Microsoft Defender ATP adds partnership opportunities for this scenario and allows MSSPs to take the following actions:
|
||||
|
||||
- Get access to MSSP customer's Microsoft Defender Security Center portal
|
||||
- Get email notifications, and
|
||||
|
||||
@ -0,0 +1,55 @@
|
||||
---
|
||||
title: Microsoft Defender ATP partner opportunities and scenarios
|
||||
ms.reviewer:
|
||||
description: Learn how you can extend existing security offerings on top of the open framework and a rich set of APIs to build extensions and integrations with Microsoft Defender ATP
|
||||
keywords: API, partner, extend, open framework, apis, extensions, integrations, detection, management, response, vulnerabilities, intelligence
|
||||
search.product: eADQiWindows 10XVcnh
|
||||
search.appverid: met150
|
||||
ms.prod: w10
|
||||
ms.mktglfcycl: deploy
|
||||
ms.sitesec: library
|
||||
ms.pagetype: security
|
||||
ms.author: macapara
|
||||
author: mjcaparas
|
||||
ms.localizationpriority: medium
|
||||
manager: dansimp
|
||||
audience: ITPro
|
||||
ms.collection: M365-security-compliance
|
||||
ms.topic: conceptual
|
||||
---
|
||||
|
||||
# Microsoft Defender ATP partner opportunities and scenarios
|
||||
|
||||
**Applies to:**
|
||||
- [Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP)](https://go.microsoft.com/fwlink/p/?linkid=2069559)
|
||||
|
||||
> Want to experience Microsoft Defender ATP? [Sign up for a free trial.](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp?ocid=docs-wdatp-exposedapis-abovefoldlink)
|
||||
|
||||
|
||||
Partners can easily extend their existing security offerings on top of the open framework and a rich and complete set of APIs to build extensions and integrations with Microsoft Defender ATP.
|
||||
|
||||
The APIs span functional areas including detection, management, response, vulnerabilities and intelligence wide range of use cases. Based on the use case and need, partners can either stream or query data from Microsoft Defender ATP.
|
||||
|
||||
|
||||
## Scenario 1: External alert correlation and Automated investigation and remediation
|
||||
Microsoft Defender ATP offers unique automated investigation and remediation capabilities to drive incident response at scale.
|
||||
|
||||
Integrating the automated investigation and response capability with other solutions such as network security products or other endpoint security products will help to address alerts and minimize the complexities surrounding network and device signal correlation, effectively streamlining the investigation and threat remediation actions on devices.
|
||||
|
||||
Microsoft Defender ATP adds support for this scenario in the following forms:
|
||||
- External alerts can be pushed into Microsoft Defender ATP and presented side-by-side with additional device-based alerts from Microsoft Defender ATP. This view provides the full context of the alert - with the real process and the full story of attack.
|
||||
|
||||
- Once an alert is generated, the signal is shared across all Microsoft Defender ATP protected endpoints in the enterprise. Microsoft Defender ATP takes immediate automated or operator-assisted response to address the alert.
|
||||
|
||||
## Scenario 2: Security orchestration and automation response (SOAR) integration
|
||||
Orchestration solutions can help build playbooks and integrate the rich data model and actions that Microsoft Defender ATP APIs exposes to orchestrate responses, such as query for device data, trigger machine isolation, block/allow, resolve alert and others.
|
||||
|
||||
## Scenario 3: Indicators matching
|
||||
Indicator of compromise (IoCs) matching is an essential feature in every endpoint protection solution. This capability is available in Microsoft Defender ATP and gives the ability to set a list of indicators for prevention, detection and exclusion of entities. One can define the action to be taken as well as the duration for when to apply the action.
|
||||
|
||||
The above scenarios serve as examples of the extensibility of the platform. You are not limited to these and we certainly encourage you leverage the open framework to discover and explore other scenarios.
|
||||
|
||||
Follow the steps in [Become a Microsoft Defender ATP partner](get-started-partner-integration.md) to integrate your solution in Microsoft Defender ATP.
|
||||
|
||||
## Related topic
|
||||
- [Overview of management and APIs](management-apis.md)
|
||||
@ -50,5 +50,19 @@ Here is an example of an IOC:
|
||||
|
||||
IOCs have a many-to-one relationship with alert definitions such that an alert definition can have many IOCs that correspond to it.
|
||||
|
||||
## In this section
|
||||
|
||||
Topic | Description
|
||||
:---|:---
|
||||
[Pull detections to your SIEM tools](configure-siem.md)| Learn about different ways to pull detections.
|
||||
[Enable SIEM integration in Microsoft Defender ATP](enable-siem-integration.md)| Learn about enabling the SIEM integration feature in the **Settings** page in the portal so that you can use and generate the required information to configure supported SIEM tools.
|
||||
[Configure Splunk to pull Microsoft Defender ATP detections](configure-splunk.md)| Learn about installing the REST API Modular Input App and other configuration settings to enable Splunk to pull Microsoft Defender ATP detections.
|
||||
[Configure HP ArcSight to pull Microsoft Defender ATP detections](configure-arcsight.md)| Learn about installing the HP ArcSight REST FlexConnector package and the files you need to configure ArcSight to pull Microsoft Defender ATP detections.
|
||||
[Microsoft Defender ATP Detection fields](api-portal-mapping.md) | Understand what data fields are exposed as part of the alerts API and how they map to Microsoft Defender Security Center.
|
||||
[Pull Microsoft Defender ATP detections using REST API](pull-alerts-using-rest-api.md) | Use the Client credentials OAuth 2.0 flow to pull detections from Microsoft Defender ATP using REST API.
|
||||
[Troubleshoot SIEM tool integration issues](troubleshoot-siem.md) | Address issues you might encounter when using the SIEM integration feature.
|
||||
|
||||
|
||||
|
||||
## Related topics
|
||||
- [Manage indicators](manage-indicators.md)
|
||||
|
||||
@ -44,12 +44,21 @@ Each machine in the organization is scored based on three important factors: thr
|
||||
|
||||
You can access the security recommendation from the Microsoft Defender ATP Threat & Vulnerability Management menu, dashboard, software page, and machine page, to give you the context that you need, as you require it.
|
||||
|
||||
From the menu, select **Security recommendations** to get an overview of the running list with its weaknesses, related components, application, operating system, network, accounts, and security controls, associated breach, threats, and recommendation insights, exposed machine trends, status, remediation type and activities.
|
||||
*Security recommendations option from the left navigation menu*
|
||||
|
||||
1. Go to the Threat & Vulnerability Management navigation menu and select **Security recommendations** to open up the list of security recommendations for the threats and vulnerabilities found in your organization. It gives you an overview of the security recommendation context: weaknesses found, related components, the application and operating system where the threat or vulnerabilities were found, network, accounts, and security controls, associated breach, threats, and recommendation insights, exposed machine trends, status, remediation type and activities.
|
||||

|
||||
|
||||
>[!NOTE]
|
||||
> The color of the **Exposed machines** graph changes as the trend changes. If the number of exposed machines is on the rise, the color changes into red. If there's a decrease in the amount of exposed machines, the color of the graph will change into green. This happens per change, which means an increase or decrease of even a single machine will change the graph's color.
|
||||
> The color of the **Exposed machines** graph changes as the trend changes. If the number of exposed machines is on the rise, the color changes into red. If there's a decrease in the amount of exposed machines, the color of the graph will change into green. This happens when the numbers on the right hand side is greater than what’s on the left, which means an increase or decrease at the end of even a single machine will change the graph's color.
|
||||
|
||||
You can filter your view based on related components, status, and remediation type. If you want to see the remediation activities of software and software versions which have reached their end-of-life, select **Active**, then select **Software update** from the **Remediation Type** filter, and click **Apply**.
|
||||
<br></br>
|
||||
|
||||
2. Select the security recommendation that you need to investigate or process.
|
||||
<br></br>
|
||||
|
||||
*Top security recommendations from the dashboard*
|
||||
|
||||
In a given day as a Security Administrator, you can take a look at the dashboard to see your exposure score side-by-side with your configuration score. The goal is to lower down your organization's exposure from vulnerabilities, and increase your organization's security configuration to be more resilient against cybersecurity threat attacks. The top security recommendations list can help you achieve that goal.
|
||||
|
||||
|
||||
@ -26,7 +26,7 @@ Describes the best practices, location, values, management, and security conside
|
||||
|
||||
## Reference
|
||||
|
||||
Beginning with Windows Server 2012 and Windows 8, Windows detects user-input inactivity of a sign-in (logon) session by using the security policy setting **Interactive logon: Machine inactivity limit**. If the amount of inactive time exceeds the inactivity limit set by this policy, then the user’s session locks by invoking the screen saver (screen saver should be active on the destination machine). This policy setting allows you to control the locking time by using Group Policy.
|
||||
Beginning with Windows Server 2012 and Windows 8, Windows detects user-input inactivity of a sign-in (logon) session by using the security policy setting **Interactive logon: Machine inactivity limit**. If the amount of inactive time exceeds the inactivity limit set by this policy, then the user’s session locks by invoking the screen saver (screen saver should be active on the destination machine). You can activate the screen saver by enabling the Group Policy **User Configuration\Administrative Templates\Control Panel\Personalization\Enable screen saver**. This policy setting allows you to control the locking time by using Group Policy.
|
||||
|
||||
### Possible values
|
||||
|
||||
|
||||
@ -84,7 +84,7 @@ You can disable this setting to ensure that only globally-defined lists (such as
|
||||
4. Double-click **Configure local administrator merge behavior for lists** and set the option to **Disabled**. Click **OK**.
|
||||
|
||||
> [!NOTE]
|
||||
> If you disable local list merging, it will override controlled folder access settings. It also overrides any protected folders or allowed apps set by the local administrator. For more information about controlled folder access settings, see [Enable controlled folder access](https://docs.microsoft.com/windows/security/threat-protection/windows-defender-exploit-guard/enable-controlled-folders-exploit-guard).
|
||||
> If you disable local list merging, it will override controlled folder access settings. It also overrides any protected folders or allowed apps set by the local administrator. For more information about controlled folder access settings, see [Allow a blocked app in Windows Security](https://support.microsoft.com/help/4046851/windows-10-allow-blocked-app-windows-security).
|
||||
|
||||
## Related topics
|
||||
|
||||
|
||||
@ -13,7 +13,7 @@ author: denisebmsft
|
||||
ms.author: deniseb
|
||||
ms.custom: nextgen
|
||||
audience: ITPro
|
||||
ms.date: 10/02/2018
|
||||
ms.date: 01/06/2020
|
||||
ms.reviewer:
|
||||
manager: dansimp
|
||||
---
|
||||
@ -25,13 +25,13 @@ manager: dansimp
|
||||
- [Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP)](https://go.microsoft.com/fwlink/p/?linkid=2069559)
|
||||
- [Microsoft Edge](https://docs.microsoft.com/microsoft-edge/deploy/microsoft-edge)
|
||||
|
||||
Potentially unwanted applications are not considered viruses, malware, or other types of threats, but they might perform actions on endpoints which adversely affect endpoint performance or use. _PUA_ can also refer to an application that has a poor reputation, as assessed by Microsoft Defender ATP, due to certain kinds of undesirable behavior.
|
||||
Potentially unwanted applications (PUA) are not considered viruses, malware, or other types of threats, but they might perform actions on endpoints which adversely affect endpoint performance or use. _PUA_ can also refer to an application that has a poor reputation, as assessed by Microsoft Defender ATP, due to certain kinds of undesirable behavior.
|
||||
|
||||
For example:
|
||||
|
||||
* **Advertising software:** Software that displays advertisements or promotions, including software that inserts advertisements to webpages.
|
||||
* **Bundling software:** Software that offers to install other software that is not digitally signed by the same entity. Also, software that offers to install other software that qualify as PUA.
|
||||
* **Evasion software:** Software that actively tries to evade detection by security products, including software that behaves differently in the presence of security products.
|
||||
* **Advertising software**: Software that displays advertisements or promotions, including software that inserts advertisements to webpages.
|
||||
* **Bundling software**: Software that offers to install other software that is not digitally signed by the same entity. Also, software that offers to install other software that qualify as PUA.
|
||||
* **Evasion software**: Software that actively tries to evade detection by security products, including software that behaves differently in the presence of security products.
|
||||
|
||||
For more examples and a discussion of the criteria we use to label applications for special attention from security features, see [How Microsoft identifies malware and potentially unwanted applications](../intelligence/criteria.md).
|
||||
|
||||
@ -45,11 +45,11 @@ The next major version of Microsoft Edge, which is Chromium-based, blocks potent
|
||||
|
||||
#### Enable PUA protection in Chromium-based Microsoft Edge
|
||||
|
||||
Although potentially unwanted application protection in Microsoft Edge (Chromium-based) is off by default, it can easily be turned on from within the browser.
|
||||
Although potentially unwanted application protection in Microsoft Edge (Chromium-based) is turned off by default, it can easily be turned on from within the browser.
|
||||
|
||||
1. From the tool bar, select **Settings and more** > **Settings**
|
||||
1. Select **Privacy and services**
|
||||
1. Under the **Services** section, you can toggle **Potentially unwanted app blocking** on or off
|
||||
1. From the tool bar, select **Settings and more** > **Settings**.
|
||||
2. Select **Privacy and services**.
|
||||
3. Under the **Services** section, you can toggle **Potentially unwanted app blocking** on or off.
|
||||
|
||||
> [!TIP]
|
||||
> If you are running Microsoft Edge (Chromium-based), you can safely explore the URL-blocking feature of PUA protection by testing it out on one of our Windows Defender SmartScreen [demo pages](https://demo.smartscreen.msft.net/).
|
||||
@ -71,11 +71,11 @@ The potentially unwanted application (PUA) protection feature in Windows Defende
|
||||
> [!NOTE]
|
||||
> This feature is only available in Windows 10.
|
||||
|
||||
Windows Defender Antivirus blocks detected PUA files, and any attempts to download, move, run, or install them. Blocked PUA files are then moved to quarantine.
|
||||
Windows Defender Antivirus blocks detected PUA files and any attempts to download, move, run, or install them. Blocked PUA files are then moved to quarantine.
|
||||
|
||||
When a PUA is detected on an endpoint, Windows Defender Antivirus sends a notification to the user ([unless notifications have been disabled](configure-notifications-windows-defender-antivirus.md)) in the same format as other threat detections. The notification will be prefaced with _PUA:_ to indicate its content.
|
||||
When a PUA file is detected on an endpoint, Windows Defender Antivirus sends a notification to the user ([unless notifications have been disabled](configure-notifications-windows-defender-antivirus.md)) in the same format as other threat detections. The notification will be prefaced with _PUA:_ to indicate its content.
|
||||
|
||||
The notification will appear in the usual [quarantine list within the Windows Security app](windows-defender-security-center-antivirus.md#detection-history).
|
||||
The notification appears in the usual [quarantine list within the Windows Security app](windows-defender-security-center-antivirus.md#detection-history).
|
||||
|
||||
#### Configure PUA protection in Windows Defender Antivirus
|
||||
|
||||
@ -105,7 +105,7 @@ For Configuration Manager 2012, see [How to Deploy Potentially Unwanted Applicat
|
||||
|
||||
##### Use Group Policy to configure PUA protection
|
||||
|
||||
1. On your Group Policy management computer, open the [Group Policy Management Console](https://technet.microsoft.com/library/cc731212.aspx), right-click the Group Policy Object you want to configure, and select **Edit**.
|
||||
1. On your Group Policy management computer, open the [Group Policy Management Console](https://docs.microsoft.com/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc731212(v=ws.11)), right-click the Group Policy Object you want to configure, and select **Edit**.
|
||||
|
||||
2. In the **Group Policy Management Editor**, go to **Computer configuration** and select **Administrative templates**.
|
||||
|
||||
@ -119,17 +119,30 @@ For Configuration Manager 2012, see [How to Deploy Potentially Unwanted Applicat
|
||||
|
||||
##### Use PowerShell cmdlets to configure PUA protection
|
||||
|
||||
Use the following cmdlet:
|
||||
###### To enable PUA protection
|
||||
|
||||
```PowerShell
|
||||
Set-MpPreference -PUAProtection
|
||||
Set-MpPreference -PUAProtection enable
|
||||
```
|
||||
|
||||
Setting the value for this cmdlet to `Enabled` will turn the feature on if it has been disabled.
|
||||
|
||||
###### To set PUA protection to audit mode
|
||||
|
||||
```PowerShell
|
||||
Set-MpPreference -PUAProtection auditmode
|
||||
```
|
||||
Setting `AuditMode` will detect PUAs without blocking them.
|
||||
|
||||
See [Use PowerShell cmdlets to configure and run Windows Defender Antivirus](use-powershell-cmdlets-windows-defender-antivirus.md) and [Defender cmdlets](https://technet.microsoft.com/library/dn433280.aspx) for more information on how to use PowerShell with Windows Defender Antivirus.
|
||||
###### To disable PUA protection
|
||||
|
||||
We recommend keeping PUA protection turned on. However, you can turn it off by using the following cmdlet:
|
||||
|
||||
```PowerShell
|
||||
Set-MpPreference -PUAProtection disable
|
||||
```
|
||||
Setting the value for this cmdlet to `Disabled` will turn the feature off if it has been enabled.
|
||||
|
||||
See [Use PowerShell cmdlets to configure and run Windows Defender Antivirus](use-powershell-cmdlets-windows-defender-antivirus.md) and [Defender cmdlets](https://docs.microsoft.com/powershell/module/defender/index) for more information on how to use PowerShell with Windows Defender Antivirus.
|
||||
|
||||
#### View PUA events
|
||||
|
||||
|
||||
|
After Width: | Height: | Size: 142 KiB |
@ -1,9 +1,9 @@
|
||||
---
|
||||
title: Protect security settings with Tamper Protection
|
||||
title: Protect security settings with tamper protection
|
||||
ms.reviewer:
|
||||
manager: dansimp
|
||||
description: Use Tamper Protection to prevent malicious apps from changing important security settings.
|
||||
keywords: malware, defender, antivirus, Tamper Protection
|
||||
description: Use tamper protection to prevent malicious apps from changing important security settings.
|
||||
keywords: malware, defender, antivirus, tamper protection
|
||||
search.product: eADQiWindows 10XVcnh
|
||||
ms.pagetype: security
|
||||
ms.prod: w10
|
||||
@ -17,7 +17,7 @@ ms.author: deniseb
|
||||
ms.custom: nextgen
|
||||
---
|
||||
|
||||
# Protect security settings with Tamper Protection
|
||||
# Protect security settings with tamper protection
|
||||
|
||||
**Applies to:**
|
||||
|
||||
@ -25,9 +25,9 @@ ms.custom: nextgen
|
||||
|
||||
## Overview
|
||||
|
||||
During some kinds of cyber attacks, bad actors try to disable security features, such as anti-virus protection, on your machines. They do this to get easier access to your data, to install malware, or to otherwise exploit your data, identity, and devices. Tamper Protection helps prevent this from occurring.
|
||||
During some kinds of cyber attacks, bad actors try to disable security features, such as anti-virus protection, on your machines. They do this to get easier access to your data, to install malware, or to otherwise exploit your data, identity, and devices. Tamper protection helps prevent this from occurring.
|
||||
|
||||
With Tamper Protection, malicious apps are prevented from taking actions like these:
|
||||
With tamper protection, malicious apps are prevented from taking actions like these:
|
||||
- Disabling virus and threat protection
|
||||
- Disabling real-time protection
|
||||
- Turning off behavior monitoring
|
||||
@ -35,25 +35,40 @@ With Tamper Protection, malicious apps are prevented from taking actions like th
|
||||
- Disabling cloud-delivered protection
|
||||
- Removing security intelligence updates
|
||||
|
||||
Tamper protection now integrates with [Threat & Vulnerability Management](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/next-gen-threat-and-vuln-mgt). Security recommendations include a check to make sure tamper protection is turned on.
|
||||
|
||||

|
||||
|
||||
In the results, you can select **Turn on Tamper Protection** to learn more and turn it on.
|
||||
|
||||

|
||||
|
||||
## How it works
|
||||
|
||||
Tamper Protection essentially locks Windows Defender Antivirus and prevents your security settings from being changed through apps and methods like these:
|
||||
Tamper protection essentially locks Windows Defender Antivirus and prevents your security settings from being changed through apps and methods like these:
|
||||
- Configuring settings in Registry Editor on your Windows machine
|
||||
- Changing settings through PowerShell cmdlets
|
||||
- Editing or removing security settings through group policies
|
||||
- and so on.
|
||||
|
||||
Tamper Protection doesn't prevent you from viewing your security settings. And, Tamper Protection doesn't affect how third-party antivirus apps register with the Windows Security app. If your organization is using Windows 10 Enterprise E5, individual users can't change the Tamper Protection setting; this is managed by your security team.
|
||||
Tamper protection doesn't prevent you from viewing your security settings. And, tamper protection doesn't affect how third-party antivirus apps register with the Windows Security app. If your organization is using Windows 10 Enterprise E5, individual users can't change the tamper protection setting; this is managed by your security team.
|
||||
|
||||
### What do you want to do?
|
||||
|
||||
[Turn Tamper Protection on (or off) for an individual machine using Windows Security](#turn-tamper-protection-on-or-off-for-an-individual-machine)
|
||||
[Turn tamper protection on (or off) for an individual machine using Windows Security](#turn-tamper-protection-on-or-off-for-an-individual-machine)
|
||||
|
||||
[Turn Tamper Protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune)
|
||||
[Turn tamper protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune)
|
||||
|
||||
## Turn Tamper Protection on (or off) for an individual machine
|
||||
## Turn tamper protection on (or off) for an individual machine
|
||||
|
||||
If you are a home user, or you are not subject to settings managed by a security team, you can use the Windows Security app to turn Tamper Protection on or off. You must have appropriate admin permissions on your machine to perform the following task.
|
||||
> [!NOTE]
|
||||
> Tamper protection blocks attempts to modify Windows Defender Antivirus settings through the registry.
|
||||
>
|
||||
> To help ensure that tamper protection doesn’t interfere with third-party security products or enterprise installation scripts that modify these settings, go to **Windows Security** and update **Security intelligence** to version 1.287.60.0 or later. (See [Security intelligence updates](https://www.microsoft.com/wdsi/definitions).)
|
||||
>
|
||||
> Once you’ve made this update, tamper protection will continue to protect your registry settings, and will also log attempts to modify them without returning errors.
|
||||
|
||||
If you are a home user, or you are not subject to settings managed by a security team, you can use the Windows Security app to turn tamper protection on or off. You must have appropriate admin permissions on your machine to perform the following task.
|
||||
|
||||
1. Click **Start**, and start typing *Defender*. In the search results, select **Windows Security**.
|
||||
|
||||
@ -61,21 +76,13 @@ If you are a home user, or you are not subject to settings managed by a security
|
||||
|
||||
3. Set **Tamper Protection** to **On** or **Off**.
|
||||
|
||||
> [!NOTE]
|
||||
> Tamper Protection blocks attempts to modify Windows Defender Antivirus settings through the registry.
|
||||
>
|
||||
> To help ensure that Tamper Protection doesn’t interfere with third-party security products or enterprise installation scripts that modify these settings, go to **Windows Security** and update **Security intelligence** to version 1.287.60.0 or later. (See [Security intelligence updates](https://www.microsoft.com/wdsi/definitions).)
|
||||
>
|
||||
> Once you’ve made this update, Tamper Protection will continue to protect your registry settings, and will also log attempts to modify them without returning errors.
|
||||
## Turn tamper protection on (or off) for your organization using Intune
|
||||
|
||||
|
||||
## Turn Tamper Protection on (or off) for your organization using Intune
|
||||
|
||||
If you are part of your organization's security team, you can turn Tamper Protection on (or off) for your organization in the Microsoft 365 Device Management portal (Intune). (This feature is rolling out now; if you don't have it yet, you should very soon, assuming your organization has [Microsoft Defender Advanced Threat Protection](../microsoft-defender-atp/whats-new-in-microsoft-defender-atp.md) (Microsoft Defender ATP) and that you meet the prerequisites listed below.)
|
||||
If you are part of your organization's security team, you can turn tamper protection on (or off) for your organization in the Microsoft 365 Device Management portal (Intune). (This feature is rolling out now; if you don't have it yet, you should very soon, assuming your organization has [Microsoft Defender Advanced Threat Protection](../microsoft-defender-atp/whats-new-in-microsoft-defender-atp.md) (Microsoft Defender ATP) and that you meet the prerequisites listed below.)
|
||||
|
||||
You must have appropriate [permissions](../microsoft-defender-atp/assign-portal-access.md), such as global admin, security admin, or security operations, to perform the following task.
|
||||
|
||||
1. Make sure your organization meets the following requirements:
|
||||
1. Make sure your organization meets all of the following requirements:
|
||||
|
||||
- Your organization must have [Microsoft Defender ATP E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp) (this is included in Microsoft 365 E5. See [Microsoft 365 Enterprise overview](https://docs.microsoft.com/microsoft-365/enterprise/microsoft-365-overview) for more details.)
|
||||
- Your organization's devices must be managed by [Intune](https://docs.microsoft.com/intune/device-management-capabilities).
|
||||
@ -90,44 +97,67 @@ You must have appropriate [permissions](../microsoft-defender-atp/assign-portal-
|
||||
4. Create a profile that includes the following settings:
|
||||
|
||||
- **Platform**: Windows 10 and later
|
||||
|
||||
- **ProfileType**: Endpoint protection
|
||||
|
||||
- **Settings** > Windows Defender Security Center > Tamper Protection
|
||||
|
||||
5. Assign the profile to one or more groups.
|
||||
|
||||
### Are you using Windows OS 1709?
|
||||
|
||||
If you are using Windows OS 1709, you don't have the Windows Security app on your computer. In this case, the one of the following procedures to determine whether tamper protection is enabled.
|
||||
|
||||
#### To determine whether tamper protection is turned on by using PowerShell
|
||||
|
||||
1. Open the Windows PowerShell app.
|
||||
|
||||
2. Use the [Get-MpComputerStatus](https://docs.microsoft.com/powershell/module/defender/get-mpcomputerstatus?view=win10-ps) PowerShell cmdlet.
|
||||
|
||||
3. In the list of results, look for `IsTamperProtected`. (A value of *true* means tamper protection is enabled.)
|
||||
|
||||
#### To determine whether tamper protection is turned on by viewing a registry key
|
||||
|
||||
1. Open the Registry Editor app.
|
||||
|
||||
2. Go to **HKEY_LOCAL_MACHINE** > **SOFTWARE** > **Microsoft** > **Windows Defender** > **Features**.
|
||||
|
||||
3. Look for an entry of **TamperProtection** of type **REG_DWORD**, with a value of **0x5**.<br/>
|
||||
- If you see **TamperProtection** with a value of **0**, tamper protection is not turned on.
|
||||
- If you do not see **TamperProtection** at all, tamper protection is not turned on.
|
||||
|
||||
## Frequently asked questions
|
||||
|
||||
### To which Windows OS versions is configuring Tamper Protection is applicable?
|
||||
### To which Windows OS versions is configuring tamper protection is applicable?
|
||||
|
||||
[Windows 1709](https://docs.microsoft.com/windows/release-information/status-windows-10-1709) or later
|
||||
[Windows 1709](https://docs.microsoft.com/windows/release-information/status-windows-10-1709) or later together with [Microsoft Defender Advanced Threat Protection E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp).
|
||||
|
||||
### Is configuring Tamper Protection in Intune supported on servers?
|
||||
### Is configuring tamper protection in Intune supported on servers?
|
||||
|
||||
No
|
||||
|
||||
### Will Tamper Protection have any impact on third party antivirus registration?
|
||||
### Will tamper protection have any impact on third party antivirus registration?
|
||||
|
||||
No, third-party antivirus will continue to register with the Windows Security application.
|
||||
|
||||
### What happens if Windows Defender Antivirus is not active on a device?
|
||||
|
||||
Tamper Protection will not have any impact on such devices.
|
||||
Tamper protection will not have any impact on such devices.
|
||||
|
||||
### How can I turn Tamper Protection on/off?
|
||||
### How can I turn tamper protection on/off?
|
||||
|
||||
If you are a home user, see [Turn Tamper Protection on (or off) for an individual machine](#turn-tamper-protection-on-or-off-for-an-individual-machine).
|
||||
If you are a home user, see [Turn tamper protection on (or off) for an individual machine](#turn-tamper-protection-on-or-off-for-an-individual-machine).
|
||||
|
||||
If you are an organization using [Microsoft Defender ATP E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp), you should be able to manage Tamper Protection in Intune similar to how you manage other endpoint protection features. See [Turn Tamper Protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune).
|
||||
If you are an organization using [Microsoft Defender ATP E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp), you should be able to manage tamper protection in Intune similar to how you manage other endpoint protection features. See [Turn tamper protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune).
|
||||
|
||||
|
||||
### How does configuring Tamper Protection in Intune affect how I manage Windows Defender Antivirus through my group policy?
|
||||
### How does configuring tamper protection in Intune affect how I manage Windows Defender Antivirus through my group policy?
|
||||
|
||||
Your regular group policy doesn’t apply to Tamper Protection, and changes to Windows Defender Antivirus settings will be ignored when Tamper Protection is on.
|
||||
Your regular group policy doesn’t apply to tamper protection, and changes to Windows Defender Antivirus settings will be ignored when tamper protection is on.
|
||||
|
||||
|
||||
>[!NOTE]
|
||||
>A small delay in Group Policy (GPO) processing may occur if Group Policy settings include values that control Windows Defender Antivirus features protected by Tamper Protection.
|
||||
To avoid any potential delays, it is recommended to remove settings that control Windows Defender Antivirus related behavior from GPO and simply allow Tamper Protection to protect Windows Defender Antivirus settings. <br><br>
|
||||
>A small delay in Group Policy (GPO) processing may occur if Group Policy settings include values that control Windows Defender Antivirus features protected by tamper protection. To avoid any potential delays, we recommend that you remove settings that control Windows Defender Antivirus related behavior from GPO and simply allow tamper protection to protect Windows Defender Antivirus settings. <br><br>
|
||||
> Sample Windows Defender Antivirus settings:<br>
|
||||
> Turn off Windows Defender Antivirus <br>
|
||||
> Computer Configuration\Administrative Templates\Windows Components\Windows Defender\
|
||||
@ -137,31 +167,31 @@ Computer Configuration\Administrative Templates\Windows Components\Windows Defen
|
||||
Value DisableRealtimeMonitoring = 0
|
||||
|
||||
|
||||
### For Microsoft Defender ATP E5, is configuring Tamper Protection in Intune targeted to the entire organization only?
|
||||
### For Microsoft Defender ATP E5, is configuring tamper protection in Intune targeted to the entire organization only?
|
||||
|
||||
Configuring Tamper Protection in Intune can be targeted to your entire organization as well as to devices and user groups with Intune.
|
||||
Configuring tamper protection in Intune can be targeted to your entire organization as well as to devices and user groups with Intune.
|
||||
|
||||
### Can I configure Tamper Protection in System Center Configuration Manager?
|
||||
### Can I configure tamper protection in System Center Configuration Manager?
|
||||
|
||||
Currently we do not have support to manage Tamper Protection through System Center Configuration Manager.
|
||||
Currently we do not have support to manage tamper protection through System Center Configuration Manager.
|
||||
|
||||
### I have the Windows E3 enrollment. Can I use configuring Tamper Protection in Intune?
|
||||
### I have the Windows E3 enrollment. Can I use configuring tamper protection in Intune?
|
||||
|
||||
Currently, configuring Tamper Protection in Intune is only available for customers who have [Microsoft Defender Advanced Threat Protection E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp).
|
||||
Currently, configuring tamper protection in Intune is only available for customers who have [Microsoft Defender Advanced Threat Protection E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp).
|
||||
|
||||
### What happens if I try to change Microsoft Defender ATP settings in Intune, System Center Configuration Manager, and Windows Management Instrumentation when Tamper Protection is enabled on a device?
|
||||
### What happens if I try to change Microsoft Defender ATP settings in Intune, System Center Configuration Manager, and Windows Management Instrumentation when tamper protection is enabled on a device?
|
||||
|
||||
You won’t be able to change the features that are protected by Tamper Protection; those change requests are ignored.
|
||||
You won’t be able to change the features that are protected by tamper protection; those change requests are ignored.
|
||||
|
||||
### I’m an enterprise customer. Can local admins change Tamper Protection on their devices?
|
||||
### I’m an enterprise customer. Can local admins change tamper protection on their devices?
|
||||
|
||||
No. Local admins cannot change or modify Tamper Protection settings.
|
||||
No. Local admins cannot change or modify tamper protection settings.
|
||||
|
||||
### What happens if my device is onboarded with Microsoft Defender ATP and then goes into an off-boarded state?
|
||||
|
||||
In this case, Tamper Protection status changes, and this feature is no longer applied.
|
||||
In this case, tamper protection status changes, and this feature is no longer applied.
|
||||
|
||||
### Will there be an alert about Tamper Protection status changing in the Microsoft Defender Security Center?
|
||||
### Will there be an alert about tamper protection status changing in the Microsoft Defender Security Center?
|
||||
|
||||
Yes. The alert is shown in [https://securitycenter.microsoft.com](https://securitycenter.microsoft.com) under **Alerts**.
|
||||
|
||||
@ -169,7 +199,7 @@ In addition, your security operations team can use hunting queries, such as the
|
||||
|
||||
`AlertEvents | where Title == "Tamper Protection bypass"`
|
||||
|
||||
### Will there be a group policy setting for Tamper Protection?
|
||||
### Will there be a group policy setting for tamper protection?
|
||||
|
||||
No.
|
||||
|
||||
|
||||