mirror of
https://github.com/MicrosoftDocs/windows-itpro-docs.git
synced 2025-06-23 06:13:41 +00:00
Merge branch 'master' into api-update
This commit is contained in:
@ -206,7 +206,7 @@ This node is deprecated. Use **Biometrics/UseBiometrics** node instead.
|
||||
|
||||
<a href="" id="biometrics--only-for---device-vendor-msft-"></a>**Biometrics** (only for ./Device/Vendor/MSFT)
|
||||
Node for defining biometric settings. This node was added in Windows 10, version 1511.
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business prior to Windows 10 version 1903 (May 2019 Update).*
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business.*
|
||||
|
||||
<a href="" id="biometrics-usebiometrics--only-for---device-vendor-msft-"></a>**Biometrics/UseBiometrics** (only for ./Device/Vendor/MSFT)
|
||||
Boolean value used to enable or disable the use of biometric gestures, such as face and fingerprint, as an alternative to the PIN gesture for Windows Hello for Business. Users must still configure a PIN if they configure biometric gestures to use in case of failures. This node was added in Windows 10, version 1511.
|
||||
@ -217,7 +217,7 @@ Default value is true, enabling the biometric gestures for use with Windows Hell
|
||||
|
||||
Supported operations are Add, Get, Delete, and Replace.
|
||||
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business.*
|
||||
*Not supported on Windows Holographic and Windows Holographic for Business prior to Windows 10 version 1903 (May 2019 Update).*
|
||||
|
||||
<a href="" id="biometrics-facialfeaturesuseenhancedantispoofing--only-for---device-vendor-msft-"></a>**Biometrics/FacialFeaturesUseEnhancedAntiSpoofing** (only for ./Device/Vendor/MSFT)
|
||||
Boolean value used to enable or disable enhanced anti-spoofing for facial feature recognition on Windows Hello face authentication. This node was added in Windows 10, version 1511.
|
||||
|
||||
@ -14,10 +14,14 @@ ms.localizationpriority: medium
|
||||
|
||||
# Policy CSP - Browser
|
||||
|
||||
|
||||
> [!NOTE]
|
||||
> You've reached the documentation for Microsoft Edge version 45 and earlier. To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).
|
||||
|
||||
<hr/>
|
||||
|
||||
> [!NOTE]
|
||||
> You've reached the documentation for Microsoft Edge version 45 and earlier. To see the documentation for Microsoft Edge version 77 or later, go to the [Microsoft Edge documentation landing page](https://docs.microsoft.com/DeployEdge/).
|
||||
|
||||
<!--Policies-->
|
||||
## Browser policies
|
||||
|
||||
|
||||
@ -29,21 +29,11 @@ If you have paid subscriptions to Office 365, Microsoft Dynamics CRM Online, Ent
|
||||
|
||||

|
||||
|
||||
3. On the **Admin center** page, hover your mouse over the Admin tools icon on the left and then click **Azure AD**. This will take you to the Azure Active Directory sign-up page and brings up your existing Office 365 organization account information.
|
||||
3. On the **Admin center** page, under Admin Centers on the left, click **Azure Active Directory**. This will take you to the Azure Active Directory portal.
|
||||
|
||||

|
||||
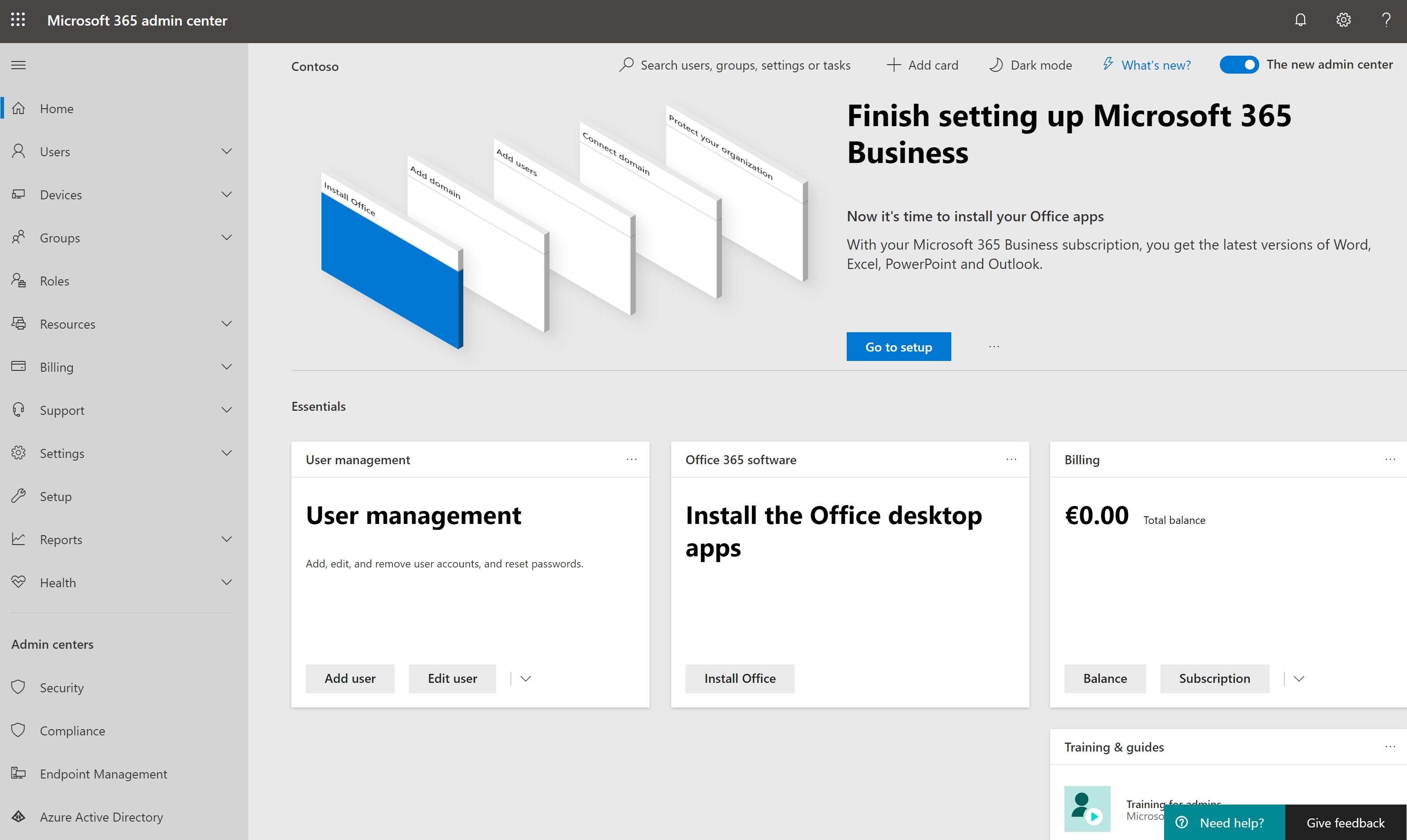
|
||||
|
||||
4. On the **Sign up** page, make sure to enter a valid phone number and then click **Sign up**.
|
||||
|
||||

|
||||
|
||||
5. It may take a few minutes to process the request.
|
||||
|
||||

|
||||
|
||||
6. You will see a welcome page when the process completes.
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
@ -125,9 +125,9 @@ Starting with Windows 10, version 1703, using Settings to control the pause beha
|
||||
|
||||
## Configure when devices receive Quality Updates
|
||||
|
||||
Quality Updates are typically published on the first Tuesday of every month, although they can be released at any time. You can define if, and for how long, you would like to defer receiving Quality Updates following their availability. You can defer receiving these Quality Updates for a period of up to 35 days from their release by setting the **DeferQualityUpdatesPeriodinDays** value.
|
||||
Quality updates are typically published on the first Tuesday of every month, although they can be released at any time. You can define if, and for how long, you would like to defer receiving Quality updates following their availability. You can defer receiving these quality updates for a period of up to 30 days from their release by setting the **DeferQualityUpdatesPeriodinDays** value.
|
||||
|
||||
You can set your system to receive updates for other Microsoft products—known as Microsoft Updates (such as Microsoft Office, Visual Studio)—along with Windows Updates by setting the **AllowMUUpdateService** policy. When you do this, these Microsoft Updates will follow the same deferral and pause rules as all other Quality Updates.
|
||||
You can set your system to receive updates for other Microsoft products—known as Microsoft updates (such as Microsoft Office, Visual Studio)—along with Windows updates by setting the **AllowMUUpdateService** policy. When you do this, these Microsoft updates will follow the same deferral and pause rules as all other quality updates.
|
||||
|
||||
>[!IMPORTANT]
|
||||
>This policy defers both Feature and Quality Updates on Windows 10 Mobile Enterprise.
|
||||
@ -146,7 +146,7 @@ You can set your system to receive updates for other Microsoft products—known
|
||||
|
||||
## Pause quality updates
|
||||
|
||||
You can also pause a system from receiving Quality Updates for a period of up to 35 days from when the value is set. After 35 days has passed, the pause setting will automatically expire and the device will scan Windows Update for applicable quality Updates. Following this scan, you can then pause quality Updates for the device again.
|
||||
You can also pause a system from receiving quality updates for a period of up to 35 days from when the value is set. After 35 days have passed, the pause setting will automatically expire and the device will scan Windows Update for applicable quality updates. Following this scan, you can then pause quality updates for the device again.
|
||||
|
||||
Starting with Windows 10, version 1703, when you configure a pause by using policy, you must set a start date for the pause to begin. The pause period is calculated by adding 35 days to this start date.
|
||||
|
||||
@ -201,9 +201,9 @@ The policy settings to **Select when Feature Updates are received** allows you t
|
||||
* Group Policy: **Computer Configuration/Administrative Templates/Windows Components/Windows Update/ Windows Update for Business** - *Select when Preview Builds and Feature Updates are received*
|
||||
* MDM: **Update/BranchReadinessLevel**
|
||||
|
||||
## Exclude drivers from Quality Updates
|
||||
## Exclude drivers from quality updates
|
||||
|
||||
Starting with Windows 10, version 1607, you can selectively opt out of receiving driver update packages as part of your normal quality update cycle. This policy will not apply to updates to drivers provided with the operating system (which will be packaged within a security or critical update) or to Feature Updates, where drivers might be dynamically installed to ensure the Feature Update process can complete.
|
||||
Starting with Windows 10, version 1607, you can selectively opt out of receiving driver update packages as part of your normal quality update cycle. This policy will not apply to updates to drivers provided with the operating system (which will be packaged within a security or critical update) or to feature updates, where drivers might be dynamically installed to ensure the feature update process can complete.
|
||||
|
||||
**Policy settings to exclude drivers**
|
||||
|
||||
|
||||
@ -35,7 +35,7 @@ The following table describes some log files and how to use them for troubleshoo
|
||||
<br>
|
||||
|
||||
<table>
|
||||
<tr><td BGCOLOR="#a0e4fa"><B>Log file</td><td BGCOLOR="#a0e4fa"><B>Phase: Location</td><td BGCOLOR="#a0e4fa"><B>Description</td><td BGCOLOR="#a0e4fa"><B>When to use</td>
|
||||
<tr><td BGCOLOR="#a0e4fa"><font color="#000000"><B>Log file</td><td BGCOLOR="#a0e4fa"><font color="#000000"><B>Phase: Location</td><td BGCOLOR="#a0e4fa"><font color="#000000"><B>Description</td><td BGCOLOR="#a0e4fa"><font color="#000000"><B>When to use</td>
|
||||
<tr><td rowspan="5">setupact.log</td><td>Down-Level:<br>$Windows.~BT\Sources\Panther</td><td>Contains information about setup actions during the downlevel phase. </td>
|
||||
<td>All down-level failures and starting point for rollback investigations.<br> This is the most important log for diagnosing setup issues.</td>
|
||||
<tr><td>OOBE:<br>$Windows.~BT\Sources\Panther\UnattendGC</td>
|
||||
@ -52,7 +52,7 @@ setupapi.dev.log<br>
|
||||
Event logs (*.evtx)</td>
|
||||
<td>$Windows.~BT\Sources\Rollback<td>Additional logs collected during rollback.</td>
|
||||
<td>
|
||||
Setupmem.dmp: If OS bugchecks during upgrade, setup will attempt to extract a mini-dump.<br>
|
||||
Setupmem.dmp: If OS bug checks during upgrade, setup will attempt to extract a mini-dump.<br>
|
||||
Setupapi: Device install issues - 0x30018<br>
|
||||
Event logs: Generic rollbacks (0xC1900101) or unexpected reboots.</td>
|
||||
</table>
|
||||
|
||||
@ -513,9 +513,9 @@ This error has more than one possible cause. Attempt [quick fixes](quick-fixes.m
|
||||
<br /><table>
|
||||
|
||||
<tr>
|
||||
<td BGCOLOR="#a0e4fa"><b>Error code</b></th>
|
||||
<td BGCOLOR="#a0e4fa"><b>Cause</b></th>
|
||||
<td BGCOLOR="#a0e4fa"><b>Mitigation</b></th>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><b>Error code</b></font></td>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><b>Cause</b></font></td>
|
||||
<td BGCOLOR="#a0e4fa"><font color="#000000"><b>Mitigation</b></font></td>
|
||||
</tr>
|
||||
|
||||
<tr>
|
||||
@ -647,7 +647,7 @@ For detailed information on how to run these steps check out <a href="https://bl
|
||||
|
||||
<br><table>
|
||||
|
||||
<tr><td BGCOLOR="#a0e4fa">Error Codes<td BGCOLOR="#a0e4fa">Cause<td BGCOLOR="#a0e4fa">Mitigation</td></tr>
|
||||
<tr><td BGCOLOR="#a0e4fa"><font color="#000000">Error Codes<td BGCOLOR="#a0e4fa"><font color="#000000">Cause<td BGCOLOR="#a0e4fa"><font color="#000000">Mitigation</td></tr>
|
||||
<tr><td>0x80070003- 0x20007
|
||||
<td>This is a failure during SafeOS phase driver installation.
|
||||
|
||||
|
||||
@ -91,7 +91,7 @@ The following tables provide the corresponding phase and operation for values of
|
||||
<br>
|
||||
|
||||
<table cellspacing="0" cellpadding="0">
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><b>Extend code: phase</b></td>
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><font color="#000000"><b>Extend code: phase</b></td>
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'><b>Hex</b><td style='padding:0in 5.4pt 0in 5.4pt'><b>Phase</b>
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'>0<td style='padding:0in 4pt 0in 4pt'>SP_EXECUTION_UNKNOWN
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'>1<td style='padding:0in 4pt 0in 4pt'>SP_EXECUTION_DOWNLEVEL
|
||||
@ -103,7 +103,7 @@ The following tables provide the corresponding phase and operation for values of
|
||||
|
||||
|
||||
<table border="0" style='border-collapse:collapse;border:none'>
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><B>Extend code: operation</B></td>
|
||||
<tr><td colspan="2" align="center" valign="top" BGCOLOR="#a0e4fa"><font color="#000000"><B>Extend code: operation</B></td>
|
||||
<tr><td align="left" valign="top" style='border:dotted #A6A6A6 1.0pt;'>
|
||||
<table>
|
||||
<tr><td style='padding:0in 4pt 0in 4pt'><b>Hex</b><td style='padding:0in 4pt 0in 4pt'><span style='padding:0in 5.4pt 0in 5.4pt;'><b>Operation</b>
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@ -104,13 +104,13 @@ Once the hardware IDs have been captured from existing devices, they can be uplo
|
||||
- [Microsoft Store for Business](https://docs.microsoft.com/microsoft-store/add-profile-to-devices#manage-autopilot-deployment-profiles). You might already be using MSfB to manage your apps and settings.
|
||||
|
||||
A summary of each platform's capabilities is provided below.
|
||||
|
||||
<br>
|
||||
<table>
|
||||
<tr>
|
||||
<td BGCOLOR="#a0e4fa"><B>Platform/Portal</th>
|
||||
<td BGCOLOR="#a0e4fa"><B>Register devices?</th>
|
||||
<td BGCOLOR="#a0e4fa"><B>Create/Assign profile</th>
|
||||
<td BGCOLOR="#a0e4fa"><B>Acceptable DeviceID</th>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Platform/Portal</font></td>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Register devices?</font></td>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Create/Assign profile</font></td>
|
||||
<td BGCOLOR="#a0e4fa"><B><font color="#000000">Acceptable DeviceID</font></td>
|
||||
</tr>
|
||||
|
||||
<tr>
|
||||
|
||||
@ -68,15 +68,16 @@ See the following examples.
|
||||
Install-PackageProvider -Name NuGet -MinimumVersion 2.8.5.201 -Force
|
||||
Install-Module AzureAD -Force
|
||||
Install-Module WindowsAutopilotIntune -Force
|
||||
Install-Module Microsoft.Graph.Intune -Force
|
||||
```
|
||||
|
||||
|
||||
3. Enter the following lines and provide Intune administrative credentials
|
||||
- In the following command, replace the example user principal name for Azure authentication (admin@M365x373186.onmicrosoft.com) with your user account. Be sure that the user account you specify has sufficient administrative rights.
|
||||
- Be sure that the user account you specify has sufficient administrative rights.
|
||||
|
||||
```powershell
|
||||
Connect-MSGraph -user admin@M365x373186.onmicrosoft.com
|
||||
Connect-MSGraph
|
||||
```
|
||||
The password for your account will be requested using a standard Azure AD form. Type your password and then click **Sign in**.
|
||||
The user and password for your account will be requested using a standard Azure AD form. Type your username and password and then click **Sign in**.
|
||||
<br>See the following example:
|
||||
|
||||

|
||||
|
||||
@ -289,6 +289,16 @@ Capability Security Identifiers (SIDs) are used to uniquely and immutably identi
|
||||
|
||||
All Capability SIDs that the operating system is aware of are stored in the Windows Registry in the path `HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities'. Any Capability SID added to Windows by first or third-party applications will be added to this location.
|
||||
|
||||
## Examples of registry keys taken from Windows 10, version 1909, 64-bit Enterprise edition
|
||||
You may see the following registry keys under AllCachedCapabilities:
|
||||
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_DevUnlock
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_DevUnlock_Internal
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_Enterprise
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_General
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_Restricted
|
||||
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\AllCachedCapabilities\capabilityClass_Windows
|
||||
|
||||
All Capability SIDs are prefixed by S-1-15-3
|
||||
|
||||
## See also
|
||||
|
||||
@ -184,6 +184,7 @@ The most common values:
|
||||
| 2 | PA-ENC-TIMESTAMP | This is a normal type for standard password authentication. |
|
||||
| 11 | PA-ETYPE-INFO | The ETYPE-INFO pre-authentication type is sent by the KDC in a KRB-ERROR indicating a requirement for additional pre-authentication. It is usually used to notify a client of which key to use for the encryption of an encrypted timestamp for the purposes of sending a PA-ENC-TIMESTAMP pre-authentication value.<br>Never saw this Pre-Authentication Type in Microsoft Active Directory environment. |
|
||||
| 15 | PA-PK-AS-REP\_OLD | Used for Smart Card logon authentication. |
|
||||
| 16 | PA-PK-AS-REQ | Request sent to KDC in Smart Card authentication scenarios.|
|
||||
| 17 | PA-PK-AS-REP | This type should also be used for Smart Card authentication, but in certain Active Directory environments, it is never seen. |
|
||||
| 19 | PA-ETYPE-INFO2 | The ETYPE-INFO2 pre-authentication type is sent by the KDC in a KRB-ERROR indicating a requirement for additional pre-authentication. It is usually used to notify a client of which key to use for the encryption of an encrypted timestamp for the purposes of sending a PA-ENC-TIMESTAMP pre-authentication value.<br>Never saw this Pre-Authentication Type in Microsoft Active Directory environment. |
|
||||
| 20 | PA-SVR-REFERRAL-INFO | Used in KDC Referrals tickets. |
|
||||
|
||||
@ -126,8 +126,9 @@ This event is always logged regardless of the "Audit Policy Change" sub-category
|
||||
|
||||
- **Subcategory** \[Type = UnicodeString\]**:** the name of auditing subcategory which state was changed. Possible values:
|
||||
|
||||
| Audit Credential Validation | Audit Process Termination | Audit Other Logon/Logoff Events |
|
||||
| Value | Value | Value |
|
||||
|------------------------------------------|----------------------------------------------|--------------------------------------|
|
||||
| Audit Credential Validation | Audit Process Termination | Audit Other Logon/Logoff Events |
|
||||
| Audit Kerberos Authentication Service | Audit RPC Events | Audit Special Logon |
|
||||
| Audit Kerberos Service Ticket Operations | Audit Detailed Directory Service Replication | Audit Application Generated |
|
||||
| Audit Other Logon/Logoff Events | Audit Directory Service Access | Audit Certification Services |
|
||||
@ -145,7 +146,7 @@ This event is always logged regardless of the "Audit Policy Change" sub-category
|
||||
| Audit Policy Change | Audit Non-Sensitive Privilege Use | Audit System Integrity |
|
||||
| Audit Authentication Policy Change | Audit Sensitive Privilege Use | Audit PNP Activity |
|
||||
| Audit Authorization Policy Change | Audit Other Privilege Use Events | |
|
||||
| Group Membership | Audit Network Policy Server | |
|
||||
| Audit Group Membership | Audit Network Policy Server | |
|
||||
|
||||
- **Subcategory GUID** \[Type = GUID\]**:** the unique GUID of changed subcategory.
|
||||
|
||||
|
||||
Binary file not shown.
|
After Width: | Height: | Size: 30 KiB |
@ -130,7 +130,7 @@ h. Select **Manage > Assignments**. In the **Include** tab, select *
|
||||
In terminal, run:
|
||||
|
||||
```bash
|
||||
mdatp --edr --earlypreview true
|
||||
mdatp --edr --early-preview true
|
||||
```
|
||||
|
||||
For versions earlier than 100.78.0, run:
|
||||
|
||||
Binary file not shown.
|
After Width: | Height: | Size: 69 KiB |
Binary file not shown.
|
After Width: | Height: | Size: 62 KiB |
@ -225,7 +225,7 @@ $ mdatp --health healthy
|
||||
The above command prints "1" if the product is onboarded and functioning as expected.
|
||||
|
||||
If the product is not healthy, the exit code (which can be checked through `echo $?`) indicates the problem:
|
||||
- 1 if the device is not yet onboarded
|
||||
- 0 if the device is not yet onboarded
|
||||
- 3 if the connection to the daemon cannot be established—for example, if the daemon is not running
|
||||
|
||||
## Logging installation issues
|
||||
|
||||
@ -371,10 +371,6 @@ The following configuration profile will:
|
||||
### Intune profile
|
||||
|
||||
```XML
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
|
||||
<plist version="1">
|
||||
<dict>
|
||||
<key>PayloadUUID</key>
|
||||
<string>C4E6A782-0C8D-44AB-A025-EB893987A295</string>
|
||||
<key>PayloadType</key>
|
||||
@ -443,8 +439,6 @@ The following configuration profile will:
|
||||
</dict>
|
||||
</dict>
|
||||
</array>
|
||||
</dict>
|
||||
</plist>
|
||||
```
|
||||
|
||||
## Full configuration profile example
|
||||
@ -530,10 +524,6 @@ The following configuration profile contains entries for all settings described
|
||||
### Intune profile
|
||||
|
||||
```XML
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
|
||||
<plist version="1">
|
||||
<dict>
|
||||
<key>PayloadUUID</key>
|
||||
<string>C4E6A782-0C8D-44AB-A025-EB893987A295</string>
|
||||
<key>PayloadType</key>
|
||||
@ -640,8 +630,6 @@ The following configuration profile contains entries for all settings described
|
||||
</dict>
|
||||
</dict>
|
||||
</array>
|
||||
</dict>
|
||||
</plist>
|
||||
```
|
||||
|
||||
## Configuration profile deployment
|
||||
|
||||
@ -174,6 +174,9 @@ When Windows Defender Antivirus is not the active antimalware in your organizati
|
||||
|
||||
If you are onboarding servers and Windows Defender Antivirus is not the active antimalware on your servers, you shouldn't uninstall Windows Defender Antivirus. You'll need to configure it to run on passive mode. For more information, see [Onboard servers](configure-server-endpoints.md).
|
||||
|
||||
> [!NOTE]
|
||||
> Your regular group policy doesn’t apply to Tamper Protection, and changes to Windows Defender Antivirus settings will be ignored when Tamper Protection is on.
|
||||
|
||||
|
||||
For more information, see [Windows Defender Antivirus compatibility](../windows-defender-antivirus/windows-defender-antivirus-compatibility.md).
|
||||
|
||||
|
||||
@ -44,12 +44,21 @@ Each machine in the organization is scored based on three important factors: thr
|
||||
|
||||
You can access the security recommendation from the Microsoft Defender ATP Threat & Vulnerability Management menu, dashboard, software page, and machine page, to give you the context that you need, as you require it.
|
||||
|
||||
From the menu, select **Security recommendations** to get an overview of the running list with its weaknesses, related components, application, operating system, network, accounts, and security controls, associated breach, threats, and recommendation insights, exposed machine trends, status, remediation type and activities.
|
||||
*Security recommendations option from the left navigation menu*
|
||||
|
||||
1. Go to the Threat & Vulnerability Management navigation menu and select **Security recommendations** to open up the list of security recommendations for the threats and vulnerabilities found in your organization. It gives you an overview of the security recommendation context: weaknesses found, related components, the application and operating system where the threat or vulnerabilities were found, network, accounts, and security controls, associated breach, threats, and recommendation insights, exposed machine trends, status, remediation type and activities.
|
||||

|
||||
|
||||
>[!NOTE]
|
||||
> The color of the **Exposed machines** graph changes as the trend changes. If the number of exposed machines is on the rise, the color changes into red. If there's a decrease in the amount of exposed machines, the color of the graph will change into green. This happens per change, which means an increase or decrease of even a single machine will change the graph's color.
|
||||
>[!NOTE]
|
||||
> The color of the **Exposed machines** graph changes as the trend changes. If the number of exposed machines is on the rise, the color changes into red. If there's a decrease in the amount of exposed machines, the color of the graph will change into green. This happens when the numbers on the right hand side is greater than what’s on the left, which means an increase or decrease at the end of even a single machine will change the graph's color.
|
||||
|
||||
You can filter your view based on related components, status, and remediation type. If you want to see the remediation activities of software and software versions which have reached their end-of-life, select **Active**, then select **Software update** from the **Remediation Type** filter, and click **Apply**.
|
||||
<br></br>
|
||||
|
||||
2. Select the security recommendation that you need to investigate or process.
|
||||
<br></br>
|
||||
|
||||
*Top security recommendations from the dashboard*
|
||||
|
||||
In a given day as a Security Administrator, you can take a look at the dashboard to see your exposure score side-by-side with your configuration score. The goal is to lower down your organization's exposure from vulnerabilities, and increase your organization's security configuration to be more resilient against cybersecurity threat attacks. The top security recommendations list can help you achieve that goal.
|
||||
|
||||
|
||||
@ -26,7 +26,7 @@ Describes the best practices, location, values, management, and security conside
|
||||
|
||||
## Reference
|
||||
|
||||
Beginning with Windows Server 2012 and Windows 8, Windows detects user-input inactivity of a sign-in (logon) session by using the security policy setting **Interactive logon: Machine inactivity limit**. If the amount of inactive time exceeds the inactivity limit set by this policy, then the user’s session locks by invoking the screen saver (screen saver should be active on the destination machine). This policy setting allows you to control the locking time by using Group Policy.
|
||||
Beginning with Windows Server 2012 and Windows 8, Windows detects user-input inactivity of a sign-in (logon) session by using the security policy setting **Interactive logon: Machine inactivity limit**. If the amount of inactive time exceeds the inactivity limit set by this policy, then the user’s session locks by invoking the screen saver (screen saver should be active on the destination machine). You can activate the screen saver by enabling the Group Policy **User Configuration\Administrative Templates\Control Panel\Personalization\Enable screen saver**. This policy setting allows you to control the locking time by using Group Policy.
|
||||
|
||||
### Possible values
|
||||
|
||||
|
||||
@ -84,7 +84,7 @@ You can disable this setting to ensure that only globally-defined lists (such as
|
||||
4. Double-click **Configure local administrator merge behavior for lists** and set the option to **Disabled**. Click **OK**.
|
||||
|
||||
> [!NOTE]
|
||||
> If you disable local list merging, it will override controlled folder access settings. It also overrides any protected folders or allowed apps set by the local administrator. For more information about controlled folder access settings, see [Enable controlled folder access](https://docs.microsoft.com/windows/security/threat-protection/windows-defender-exploit-guard/enable-controlled-folders-exploit-guard).
|
||||
> If you disable local list merging, it will override controlled folder access settings. It also overrides any protected folders or allowed apps set by the local administrator. For more information about controlled folder access settings, see [Allow a blocked app in Windows Security](https://support.microsoft.com/help/4046851/windows-10-allow-blocked-app-windows-security).
|
||||
|
||||
## Related topics
|
||||
|
||||
|
||||
@ -13,7 +13,7 @@ author: denisebmsft
|
||||
ms.author: deniseb
|
||||
ms.custom: nextgen
|
||||
audience: ITPro
|
||||
ms.date: 10/02/2018
|
||||
ms.date: 01/06/2020
|
||||
ms.reviewer:
|
||||
manager: dansimp
|
||||
---
|
||||
@ -25,13 +25,13 @@ manager: dansimp
|
||||
- [Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP)](https://go.microsoft.com/fwlink/p/?linkid=2069559)
|
||||
- [Microsoft Edge](https://docs.microsoft.com/microsoft-edge/deploy/microsoft-edge)
|
||||
|
||||
Potentially unwanted applications are not considered viruses, malware, or other types of threats, but they might perform actions on endpoints which adversely affect endpoint performance or use. _PUA_ can also refer to an application that has a poor reputation, as assessed by Microsoft Defender ATP, due to certain kinds of undesirable behavior.
|
||||
Potentially unwanted applications (PUA) are not considered viruses, malware, or other types of threats, but they might perform actions on endpoints which adversely affect endpoint performance or use. _PUA_ can also refer to an application that has a poor reputation, as assessed by Microsoft Defender ATP, due to certain kinds of undesirable behavior.
|
||||
|
||||
For example:
|
||||
|
||||
* **Advertising software:** Software that displays advertisements or promotions, including software that inserts advertisements to webpages.
|
||||
* **Bundling software:** Software that offers to install other software that is not digitally signed by the same entity. Also, software that offers to install other software that qualify as PUA.
|
||||
* **Evasion software:** Software that actively tries to evade detection by security products, including software that behaves differently in the presence of security products.
|
||||
* **Advertising software**: Software that displays advertisements or promotions, including software that inserts advertisements to webpages.
|
||||
* **Bundling software**: Software that offers to install other software that is not digitally signed by the same entity. Also, software that offers to install other software that qualify as PUA.
|
||||
* **Evasion software**: Software that actively tries to evade detection by security products, including software that behaves differently in the presence of security products.
|
||||
|
||||
For more examples and a discussion of the criteria we use to label applications for special attention from security features, see [How Microsoft identifies malware and potentially unwanted applications](../intelligence/criteria.md).
|
||||
|
||||
@ -45,11 +45,11 @@ The next major version of Microsoft Edge, which is Chromium-based, blocks potent
|
||||
|
||||
#### Enable PUA protection in Chromium-based Microsoft Edge
|
||||
|
||||
Although potentially unwanted application protection in Microsoft Edge (Chromium-based) is off by default, it can easily be turned on from within the browser.
|
||||
Although potentially unwanted application protection in Microsoft Edge (Chromium-based) is turned off by default, it can easily be turned on from within the browser.
|
||||
|
||||
1. From the tool bar, select **Settings and more** > **Settings**
|
||||
1. Select **Privacy and services**
|
||||
1. Under the **Services** section, you can toggle **Potentially unwanted app blocking** on or off
|
||||
1. From the tool bar, select **Settings and more** > **Settings**.
|
||||
2. Select **Privacy and services**.
|
||||
3. Under the **Services** section, you can toggle **Potentially unwanted app blocking** on or off.
|
||||
|
||||
> [!TIP]
|
||||
> If you are running Microsoft Edge (Chromium-based), you can safely explore the URL-blocking feature of PUA protection by testing it out on one of our Windows Defender SmartScreen [demo pages](https://demo.smartscreen.msft.net/).
|
||||
@ -58,7 +58,7 @@ Although potentially unwanted application protection in Microsoft Edge (Chromium
|
||||
|
||||
In Chromium-based Edge with PUA protection turned on, Windows Defender SmartScreen will protect you from PUA-associated URLs.
|
||||
|
||||
Admins can [configure](https://docs.microsoft.com/DeployEdge/configure-microsoft-edge) how Microsoft Edge and Windows Defender SmartScreen work together to protect groups of users from PUA-associated URLs. There are several group policy [settings](https://docs.microsoft.com/DeployEdge/microsoft-edge-policies#smartscreen-settings) explicitly for Windows
|
||||
Admins can [configure](https://docs.microsoft.com/DeployEdge/configure-microsoft-edge) how Microsoft Edge and Windows Defender SmartScreen work together to protect groups of users from PUA-associated URLs. There are several group policy [settings](https://docs.microsoft.com/DeployEdge/microsoft-edge-policies#smartscreen-settings) explicitly for Windows
|
||||
Defender SmartScreen available, including [one for blocking PUA](https://docs.microsoft.com/DeployEdge/microsoft-edge-policies#smartscreenpuaenabled). In addition, admins can
|
||||
[configure Windows Defender SmartScreen](https://docs.microsoft.com/microsoft-edge/deploy/available-policies?source=docs#configure-windows-defender-smartscreen) as a whole, using group policy settings to turn Windows Defender SmartScreen on or off.
|
||||
|
||||
@ -71,11 +71,11 @@ The potentially unwanted application (PUA) protection feature in Windows Defende
|
||||
> [!NOTE]
|
||||
> This feature is only available in Windows 10.
|
||||
|
||||
Windows Defender Antivirus blocks detected PUA files, and any attempts to download, move, run, or install them. Blocked PUA files are then moved to quarantine.
|
||||
Windows Defender Antivirus blocks detected PUA files and any attempts to download, move, run, or install them. Blocked PUA files are then moved to quarantine.
|
||||
|
||||
When a PUA is detected on an endpoint, Windows Defender Antivirus sends a notification to the user ([unless notifications have been disabled](configure-notifications-windows-defender-antivirus.md)) in the same format as other threat detections. The notification will be prefaced with _PUA:_ to indicate its content.
|
||||
When a PUA file is detected on an endpoint, Windows Defender Antivirus sends a notification to the user ([unless notifications have been disabled](configure-notifications-windows-defender-antivirus.md)) in the same format as other threat detections. The notification will be prefaced with _PUA:_ to indicate its content.
|
||||
|
||||
The notification will appear in the usual [quarantine list within the Windows Security app](windows-defender-security-center-antivirus.md#detection-history).
|
||||
The notification appears in the usual [quarantine list within the Windows Security app](windows-defender-security-center-antivirus.md#detection-history).
|
||||
|
||||
#### Configure PUA protection in Windows Defender Antivirus
|
||||
|
||||
@ -105,7 +105,7 @@ For Configuration Manager 2012, see [How to Deploy Potentially Unwanted Applicat
|
||||
|
||||
##### Use Group Policy to configure PUA protection
|
||||
|
||||
1. On your Group Policy management computer, open the [Group Policy Management Console](https://technet.microsoft.com/library/cc731212.aspx), right-click the Group Policy Object you want to configure, and select **Edit**.
|
||||
1. On your Group Policy management computer, open the [Group Policy Management Console](https://docs.microsoft.com/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc731212(v=ws.11)), right-click the Group Policy Object you want to configure, and select **Edit**.
|
||||
|
||||
2. In the **Group Policy Management Editor**, go to **Computer configuration** and select **Administrative templates**.
|
||||
|
||||
@ -119,17 +119,30 @@ For Configuration Manager 2012, see [How to Deploy Potentially Unwanted Applicat
|
||||
|
||||
##### Use PowerShell cmdlets to configure PUA protection
|
||||
|
||||
Use the following cmdlet:
|
||||
###### To enable PUA protection
|
||||
|
||||
```PowerShell
|
||||
Set-MpPreference -PUAProtection
|
||||
Set-MpPreference -PUAProtection enable
|
||||
```
|
||||
|
||||
Setting the value for this cmdlet to `Enabled` will turn the feature on if it has been disabled.
|
||||
|
||||
###### To set PUA protection to audit mode
|
||||
|
||||
```PowerShell
|
||||
Set-MpPreference -PUAProtection auditmode
|
||||
```
|
||||
Setting `AuditMode` will detect PUAs without blocking them.
|
||||
|
||||
See [Use PowerShell cmdlets to configure and run Windows Defender Antivirus](use-powershell-cmdlets-windows-defender-antivirus.md) and [Defender cmdlets](https://technet.microsoft.com/library/dn433280.aspx) for more information on how to use PowerShell with Windows Defender Antivirus.
|
||||
###### To disable PUA protection
|
||||
|
||||
We recommend keeping PUA protection turned on. However, you can turn it off by using the following cmdlet:
|
||||
|
||||
```PowerShell
|
||||
Set-MpPreference -PUAProtection disable
|
||||
```
|
||||
Setting the value for this cmdlet to `Disabled` will turn the feature off if it has been enabled.
|
||||
|
||||
See [Use PowerShell cmdlets to configure and run Windows Defender Antivirus](use-powershell-cmdlets-windows-defender-antivirus.md) and [Defender cmdlets](https://docs.microsoft.com/powershell/module/defender/index) for more information on how to use PowerShell with Windows Defender Antivirus.
|
||||
|
||||
#### View PUA events
|
||||
|
||||
|
||||
Binary file not shown.
|
After Width: | Height: | Size: 142 KiB |
@ -11,7 +11,7 @@ ms.pagetype: security
|
||||
ms.localizationpriority: medium
|
||||
author: denisebmsft
|
||||
ms.author: deniseb
|
||||
ms.date: 10/18/2019
|
||||
ms.date: 01/09/2020
|
||||
ms.reviewer:
|
||||
manager: dansimp
|
||||
ms.custom: nextgen
|
||||
@ -30,7 +30,7 @@ Keeping your antivirus protection up to date is critical. There are two componen
|
||||
- *Where* the updates are downloaded from; and
|
||||
- *When* updates are downloaded and applied.
|
||||
|
||||
This article describes the *where* - how to specify where updates should be downloaded from (this is also known as the fallback order). See [Manage Windows Defender Antivirus updates and apply baselines](manage-updates-baselines-windows-defender-antivirus.md) topic for an overview on how updates work, and how to configure other aspects of updates (such as scheduling updates).
|
||||
This article describes how to specify from where updates should be downloaded (this is also known as the fallback order). See [Manage Windows Defender Antivirus updates and apply baselines](manage-updates-baselines-windows-defender-antivirus.md) topic for an overview on how updates work, and how to configure other aspects of updates (such as scheduling updates).
|
||||
|
||||
> [!IMPORTANT]
|
||||
> Microsoft Defender Antivirus Security intelligence updates are delivered through Windows Update and starting Monday, October 21, 2019, all security intelligence updates will be SHA-2 signed exclusively. Your devices must be updated to support SHA-2 in order to update your security intelligence. To learn more, see [2019 SHA-2 Code Signing Support requirement for Windows and WSUS](https://support.microsoft.com/help/4472027/2019-sha-2-code-signing-support-requirement-for-windows-and-wsus).
|
||||
@ -40,7 +40,7 @@ This article describes the *where* - how to specify where updates should be down
|
||||
|
||||
## Fallback order
|
||||
|
||||
Typically, you configure endpoints to individually download updates from a primary source, followed by other sources in order of priority, based on your network configuration. Updates are obtained from sources in the order you specify. If a source is not available, the next source in the list is used.
|
||||
Typically, you configure endpoints to individually download updates from a primary source followed by other sources in order of priority, based on your network configuration. Updates are obtained from sources in the order you specify. If a source is not available, the next source in the list is used.
|
||||
|
||||
When updates are published, some logic is applied to minimize the size of the update. In most cases, only the differences between the latest update and the update that is currently installed (this is referred to as the delta) on the device is downloaded and applied. However, the size of the delta depends on two main factors:
|
||||
- The age of the last update on the device; and
|
||||
@ -73,16 +73,13 @@ Each source has typical scenarios that depend on how your network is configured,
|
||||
|System Center Configuration Manager | You are using System Center Configuration Manager to update your endpoints.|
|
||||
|Security intelligence updates for Windows Defender Antivirus and other Microsoft antimalware (formerly referred to as MMPC) |[Make sure your devices are updated to support SHA-2](https://support.microsoft.com/help/4472027/2019-sha-2-code-signing-support-requirement-for-windows-and-wsus). Microsoft Defender Antivirus Security intelligence updates are delivered through Windows Update, and starting Monday October 21, 2019 security intelligence updates will be SHA-2 signed exclusively. <br/>Download the latest protection updates because of a recent infection or to help provision a strong, base image for [VDI deployment](deployment-vdi-windows-defender-antivirus.md). This option should generally be used only as a final fallback source, and not the primary source. It will only be used if updates cannot be downloaded from Windows Server Update Service or Microsoft Update for [a specified number of days](https://docs.microsoft.com/windows/threat-protection/windows-defender-antivirus/manage-outdated-endpoints-windows-defender-antivirus#set-the-number-of-days-before-protection-is-reported-as-out-of-date).|
|
||||
|
||||
|
||||
You can manage the order in which update sources are used with Group Policy, System Center Configuration Manager, PowerShell cmdlets, and WMI.
|
||||
|
||||
> [!IMPORTANT]
|
||||
> If you set Windows Server Update Service as a download location, you must approve the updates, regardless of the management tool you use to specify the location. You can set up an automatic approval rule with Windows Server Update Service, which might be useful as updates arrive at least once a day. To learn more, see [synchronize endpoint protection updates in standalone Windows Server Update Service](https://docs.microsoft.com/sccm/protect/deploy-use/endpoint-definitions-wsus#to-synchronize-endpoint-protection-definition-updates-in-standalone-wsus).
|
||||
|
||||
|
||||
The procedures in this article first describe how to set the order, and then how to set up the **File share** option if you have enabled it.
|
||||
|
||||
|
||||
## Use Group Policy to manage the update location
|
||||
|
||||
1. On your Group Policy management machine, open the [Group Policy Management Console](https://docs.microsoft.com/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc731212(v=ws.11)), right-click the Group Policy Object you want to configure and click **Edit**.
|
||||
@ -103,7 +100,7 @@ The procedures in this article first describe how to set the order, and then how
|
||||
|
||||
4. Double-click the **Define file shares for downloading security intelligence updates** setting and set the option to **Enabled**.
|
||||
|
||||
5. Enter the file share source. If you have multiple sources, enter each source in the order they should be used, separated by a single pipe. Use [standard UNC notation](https://docs.microsoft.com/openspecs/windows_protocols/ms-dtyp/62e862f4-2a51-452e-8eeb-dc4ff5ee33cc) for denoting the path, for example: `\\host-name1\share-name\object-name|\\host-name2\share-name\object-name`. If you do not enter any paths then this source will be skipped when the VM downloads updates.
|
||||
5. Enter the file share source. If you have multiple sources, enter each source in the order they should be used, separated by a single pipe. Use [standard UNC notation](https://docs.microsoft.com/openspecs/windows_protocols/ms-dtyp/62e862f4-2a51-452e-8eeb-dc4ff5ee33cc) for denoting the path, for example: `\\host-name1\share-name\object-name|\\host-name2\share-name\object-name`. If you do not enter any paths, then this source will be skipped when the VM downloads updates.
|
||||
|
||||
6. Click **OK**. This will set the order of file shares when that source is referenced in the **Define the order of sources...** group policy setting.
|
||||
|
||||
@ -124,7 +121,7 @@ Use the following PowerShell cmdlets to set the update order.
|
||||
Set-MpPreference -SignatureFallbackOrder {LOCATION|LOCATION|LOCATION|LOCATION}
|
||||
Set-MpPreference -SignatureDefinitionUpdateFileSharesSource {\\UNC SHARE PATH|\\UNC SHARE PATH}
|
||||
```
|
||||
See the following for more information:
|
||||
See the following articles for more information:
|
||||
- [Set-MpPreference -SignatureFallbackOrder](https://docs.microsoft.com/powershell/module/defender/set-mppreference)
|
||||
- [Set-MpPreference -SignatureDefinitionUpdateFileSharesSource](https://technet.microsoft.com/itpro/powershell/windows/defender/set-mppreference#-signaturedefinitionupdatefilesharessources)
|
||||
- [Use PowerShell cmdlets to configure and run Windows Defender Antivirus](use-powershell-cmdlets-windows-defender-antivirus.md)
|
||||
@ -139,13 +136,21 @@ SignatureFallbackOrder
|
||||
SignatureDefinitionUpdateFileSharesSource
|
||||
```
|
||||
|
||||
See the following for more information:
|
||||
See the following articles for more information:
|
||||
- [Windows Defender WMIv2 APIs](https://docs.microsoft.com/previous-versions/windows/desktop/defender/windows-defender-wmiv2-apis-portal)
|
||||
|
||||
## Use Mobile Device Management (MDM) to manage the update location
|
||||
|
||||
See [Policy CSP - Defender/SignatureUpdateFallbackOrder](https://docs.microsoft.com/windows/client-management/mdm/policy-csp-defender#defender-signatureupdatefallbackorder) for details on configuring MDM.
|
||||
|
||||
## What if we're using a third-party vendor?
|
||||
|
||||
This article describes how to configure and manage updates for Windows Defender Antivirus. However, third-party vendors can be used to perform these tasks.
|
||||
|
||||
For example, suppose that Contoso has hired Fabrikam to manage their security solution, which includes Windows Defender Antivirus. Fabrikam typically uses [Windows Management Instrumentation](https://docs.microsoft.com/windows/security/threat-protection/windows-defender-antivirus/use-wmi-windows-defender-antivirus), [PowerShell cmdlets](https://docs.microsoft.com/windows/security/threat-protection/windows-defender-antivirus/use-powershell-cmdlets-windows-defender-antivirus), or [Windows command-line](https://docs.microsoft.com/windows/security/threat-protection/windows-defender-antivirus/command-line-arguments-windows-defender-antivirus) to deploy patches and updates.
|
||||
|
||||
> [!NOTE]
|
||||
> Microsoft does not test third-party solutions for managing Windows Defender Antivirus.
|
||||
|
||||
## Related articles
|
||||
|
||||
|
||||
@ -1,9 +1,9 @@
|
||||
---
|
||||
title: Protect security settings with Tamper Protection
|
||||
title: Protect security settings with tamper protection
|
||||
ms.reviewer:
|
||||
manager: dansimp
|
||||
description: Use Tamper Protection to prevent malicious apps from changing important security settings.
|
||||
keywords: malware, defender, antivirus, Tamper Protection
|
||||
description: Use tamper protection to prevent malicious apps from changing important security settings.
|
||||
keywords: malware, defender, antivirus, tamper protection
|
||||
search.product: eADQiWindows 10XVcnh
|
||||
ms.pagetype: security
|
||||
ms.prod: w10
|
||||
@ -17,7 +17,7 @@ ms.author: deniseb
|
||||
ms.custom: nextgen
|
||||
---
|
||||
|
||||
# Protect security settings with Tamper Protection
|
||||
# Protect security settings with tamper protection
|
||||
|
||||
**Applies to:**
|
||||
|
||||
@ -25,9 +25,9 @@ ms.custom: nextgen
|
||||
|
||||
## Overview
|
||||
|
||||
During some kinds of cyber attacks, bad actors try to disable security features, such as anti-virus protection, on your machines. They do this to get easier access to your data, to install malware, or to otherwise exploit your data, identity, and devices. Tamper Protection helps prevent this from occurring.
|
||||
During some kinds of cyber attacks, bad actors try to disable security features, such as anti-virus protection, on your machines. They do this to get easier access to your data, to install malware, or to otherwise exploit your data, identity, and devices. Tamper protection helps prevent this from occurring.
|
||||
|
||||
With Tamper Protection, malicious apps are prevented from taking actions like these:
|
||||
With tamper protection, malicious apps are prevented from taking actions like these:
|
||||
- Disabling virus and threat protection
|
||||
- Disabling real-time protection
|
||||
- Turning off behavior monitoring
|
||||
@ -35,25 +35,40 @@ With Tamper Protection, malicious apps are prevented from taking actions like th
|
||||
- Disabling cloud-delivered protection
|
||||
- Removing security intelligence updates
|
||||
|
||||
Tamper protection now integrates with [Threat & Vulnerability Management](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/next-gen-threat-and-vuln-mgt). Security recommendations include a check to make sure tamper protection is turned on.
|
||||
|
||||

|
||||
|
||||
In the results, you can select **Turn on Tamper Protection** to learn more and turn it on.
|
||||
|
||||

|
||||
|
||||
## How it works
|
||||
|
||||
Tamper Protection essentially locks Windows Defender Antivirus and prevents your security settings from being changed through apps and methods like these:
|
||||
Tamper protection essentially locks Windows Defender Antivirus and prevents your security settings from being changed through apps and methods like these:
|
||||
- Configuring settings in Registry Editor on your Windows machine
|
||||
- Changing settings through PowerShell cmdlets
|
||||
- Editing or removing security settings through group policies
|
||||
- and so on.
|
||||
|
||||
Tamper Protection doesn't prevent you from viewing your security settings. And, Tamper Protection doesn't affect how third-party antivirus apps register with the Windows Security app. If your organization is using Windows 10 Enterprise E5, individual users can't change the Tamper Protection setting; this is managed by your security team.
|
||||
Tamper protection doesn't prevent you from viewing your security settings. And, tamper protection doesn't affect how third-party antivirus apps register with the Windows Security app. If your organization is using Windows 10 Enterprise E5, individual users can't change the tamper protection setting; this is managed by your security team.
|
||||
|
||||
### What do you want to do?
|
||||
|
||||
[Turn Tamper Protection on (or off) for an individual machine using Windows Security](#turn-tamper-protection-on-or-off-for-an-individual-machine)
|
||||
[Turn tamper protection on (or off) for an individual machine using Windows Security](#turn-tamper-protection-on-or-off-for-an-individual-machine)
|
||||
|
||||
[Turn Tamper Protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune)
|
||||
[Turn tamper protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune)
|
||||
|
||||
## Turn Tamper Protection on (or off) for an individual machine
|
||||
## Turn tamper protection on (or off) for an individual machine
|
||||
|
||||
If you are a home user, or you are not subject to settings managed by a security team, you can use the Windows Security app to turn Tamper Protection on or off. You must have appropriate admin permissions on your machine to perform the following task.
|
||||
> [!NOTE]
|
||||
> Tamper protection blocks attempts to modify Windows Defender Antivirus settings through the registry.
|
||||
>
|
||||
> To help ensure that tamper protection doesn’t interfere with third-party security products or enterprise installation scripts that modify these settings, go to **Windows Security** and update **Security intelligence** to version 1.287.60.0 or later. (See [Security intelligence updates](https://www.microsoft.com/wdsi/definitions).)
|
||||
>
|
||||
> Once you’ve made this update, tamper protection will continue to protect your registry settings, and will also log attempts to modify them without returning errors.
|
||||
|
||||
If you are a home user, or you are not subject to settings managed by a security team, you can use the Windows Security app to turn tamper protection on or off. You must have appropriate admin permissions on your machine to perform the following task.
|
||||
|
||||
1. Click **Start**, and start typing *Defender*. In the search results, select **Windows Security**.
|
||||
|
||||
@ -61,25 +76,17 @@ If you are a home user, or you are not subject to settings managed by a security
|
||||
|
||||
3. Set **Tamper Protection** to **On** or **Off**.
|
||||
|
||||
> [!NOTE]
|
||||
> Tamper Protection blocks attempts to modify Windows Defender Antivirus settings through the registry.
|
||||
>
|
||||
> To help ensure that Tamper Protection doesn’t interfere with third-party security products or enterprise installation scripts that modify these settings, go to **Windows Security** and update **Security intelligence** to version 1.287.60.0 or later. (See [Security intelligence updates](https://www.microsoft.com/wdsi/definitions).)
|
||||
>
|
||||
> Once you’ve made this update, Tamper Protection will continue to protect your registry settings, and will also log attempts to modify them without returning errors.
|
||||
## Turn tamper protection on (or off) for your organization using Intune
|
||||
|
||||
|
||||
## Turn Tamper Protection on (or off) for your organization using Intune
|
||||
|
||||
If you are part of your organization's security team, you can turn Tamper Protection on (or off) for your organization in the Microsoft 365 Device Management portal (Intune). (This feature is rolling out now; if you don't have it yet, you should very soon, assuming your organization has [Microsoft Defender Advanced Threat Protection](../microsoft-defender-atp/whats-new-in-microsoft-defender-atp.md) (Microsoft Defender ATP) and that you meet the prerequisites listed below.)
|
||||
If you are part of your organization's security team, you can turn tamper protection on (or off) for your organization in the Microsoft 365 Device Management portal (Intune). (This feature is rolling out now; if you don't have it yet, you should very soon, assuming your organization has [Microsoft Defender Advanced Threat Protection](../microsoft-defender-atp/whats-new-in-microsoft-defender-atp.md) (Microsoft Defender ATP) and that you meet the prerequisites listed below.)
|
||||
|
||||
You must have appropriate [permissions](../microsoft-defender-atp/assign-portal-access.md), such as global admin, security admin, or security operations, to perform the following task.
|
||||
|
||||
1. Make sure your organization meets the following requirements:
|
||||
1. Make sure your organization meets all of the following requirements:
|
||||
|
||||
- Your organization must have [Microsoft Defender ATP E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp) (this is included in Microsoft 365 E5. See [Microsoft 365 Enterprise overview](https://docs.microsoft.com/microsoft-365/enterprise/microsoft-365-overview) for more details.)
|
||||
- Your organization's devices must be managed by [Intune](https://docs.microsoft.com/intune/device-management-capabilities).
|
||||
- Your Windows machines must be running [Windows OS 1903](https://docs.microsoft.com/windows/release-information/status-windows-10-1903) or later.
|
||||
- Your Windows machines must be running [Windows OS 1709](https://docs.microsoft.com/windows/release-information/status-windows-10-1709) or later.
|
||||
- You must be using Windows security with [security intelligence](https://www.microsoft.com/wdsi/definitions) updated to version 1.287.60.0 (or above)
|
||||
- Your machines must be using anti-malware platform version 4.18.1906.3 (or above) and anti-malware engine version 1.1.15500.X (or above). (See [Manage Windows Defender Antivirus updates and apply baselines](manage-updates-baselines-windows-defender-antivirus.md).)
|
||||
|
||||
@ -90,44 +97,67 @@ You must have appropriate [permissions](../microsoft-defender-atp/assign-portal-
|
||||
4. Create a profile that includes the following settings:
|
||||
|
||||
- **Platform**: Windows 10 and later
|
||||
|
||||
- **ProfileType**: Endpoint protection
|
||||
|
||||
- **Settings** > Windows Defender Security Center > Tamper Protection
|
||||
|
||||
5. Assign the profile to one or more groups.
|
||||
|
||||
### Are you using Windows OS 1709?
|
||||
|
||||
If you are using Windows OS 1709, you don't have the Windows Security app on your computer. In this case, the one of the following procedures to determine whether tamper protection is enabled.
|
||||
|
||||
#### To determine whether tamper protection is turned on by using PowerShell
|
||||
|
||||
1. Open the Windows PowerShell app.
|
||||
|
||||
2. Use the [Get-MpComputerStatus](https://docs.microsoft.com/powershell/module/defender/get-mpcomputerstatus?view=win10-ps) PowerShell cmdlet.
|
||||
|
||||
3. In the list of results, look for `IsTamperProtected`. (A value of *true* means tamper protection is enabled.)
|
||||
|
||||
#### To determine whether tamper protection is turned on by viewing a registry key
|
||||
|
||||
1. Open the Registry Editor app.
|
||||
|
||||
2. Go to **HKEY_LOCAL_MACHINE** > **SOFTWARE** > **Microsoft** > **Windows Defender** > **Features**.
|
||||
|
||||
3. Look for an entry of **TamperProtection** of type **REG_DWORD**, with a value of **0x5**.<br/>
|
||||
- If you see **TamperProtection** with a value of **0**, tamper protection is not turned on.
|
||||
- If you do not see **TamperProtection** at all, tamper protection is not turned on.
|
||||
|
||||
## Frequently asked questions
|
||||
|
||||
### To which Windows OS versions is configuring Tamper Protection is applicable?
|
||||
### To which Windows OS versions is configuring tamper protection is applicable?
|
||||
|
||||
Windows 1903 May release
|
||||
[Windows 1709](https://docs.microsoft.com/windows/release-information/status-windows-10-1709) or later together with [Microsoft Defender Advanced Threat Protection E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp).
|
||||
|
||||
### Is configuring Tamper Protection in Intune supported on servers?
|
||||
### Is configuring tamper protection in Intune supported on servers?
|
||||
|
||||
No
|
||||
|
||||
### Will Tamper Protection have any impact on third party antivirus registration?
|
||||
### Will tamper protection have any impact on third party antivirus registration?
|
||||
|
||||
No, third-party antivirus will continue to register with the Windows Security application.
|
||||
|
||||
### What happens if Microsoft Defender Antivirus is not active on a device?
|
||||
### What happens if Windows Defender Antivirus is not active on a device?
|
||||
|
||||
Tamper Protection will not have any impact on such devices.
|
||||
Tamper protection will not have any impact on such devices.
|
||||
|
||||
### How can I turn Tamper Protection on/off?
|
||||
### How can I turn tamper protection on/off?
|
||||
|
||||
If you are a home user, see [Turn Tamper Protection on (or off) for an individual machine](#turn-tamper-protection-on-or-off-for-an-individual-machine).
|
||||
If you are a home user, see [Turn tamper protection on (or off) for an individual machine](#turn-tamper-protection-on-or-off-for-an-individual-machine).
|
||||
|
||||
If you are an organization using [Microsoft Defender ATP E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp), you should be able to manage Tamper Protection in Intune similar to how you manage other endpoint protection features. See [Turn Tamper Protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune).
|
||||
If you are an organization using [Microsoft Defender ATP E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp), you should be able to manage tamper protection in Intune similar to how you manage other endpoint protection features. See [Turn tamper protection on (or off) for your organization using Intune](#turn-tamper-protection-on-or-off-for-your-organization-using-intune).
|
||||
|
||||
|
||||
### How does configuring Tamper Protection in Intune affect how I manage Windows Defender Antivirus through my group policy?
|
||||
### How does configuring tamper protection in Intune affect how I manage Windows Defender Antivirus through my group policy?
|
||||
|
||||
Your regular group policy doesn’t apply to Tamper Protection, and changes to Windows Defender Antivirus settings will be ignored when Tamper Protection is on.
|
||||
Your regular group policy doesn’t apply to tamper protection, and changes to Windows Defender Antivirus settings will be ignored when tamper protection is on.
|
||||
|
||||
|
||||
>[!NOTE]
|
||||
>A small delay in Group Policy (GPO) processing may occur if Group Policy settings include values that control Windows Defender Antivirus features protected by Tamper Protection.
|
||||
To avoid any potential delays, it is recommended to remove settings that control Windows Defender Antivirus related behavior from GPO and simply allow Tamper Protection to protect Windows Defender Antivirus settings. <br><br>
|
||||
>A small delay in Group Policy (GPO) processing may occur if Group Policy settings include values that control Windows Defender Antivirus features protected by tamper protection. To avoid any potential delays, we recommend that you remove settings that control Windows Defender Antivirus related behavior from GPO and simply allow tamper protection to protect Windows Defender Antivirus settings. <br><br>
|
||||
> Sample Windows Defender Antivirus settings:<br>
|
||||
> Turn off Windows Defender Antivirus <br>
|
||||
> Computer Configuration\Administrative Templates\Windows Components\Windows Defender\
|
||||
@ -137,31 +167,31 @@ Computer Configuration\Administrative Templates\Windows Components\Windows Defen
|
||||
Value DisableRealtimeMonitoring = 0
|
||||
|
||||
|
||||
### For Microsoft Defender ATP E5, is configuring Tamper Protection in Intune targeted to the entire organization only?
|
||||
### For Microsoft Defender ATP E5, is configuring tamper protection in Intune targeted to the entire organization only?
|
||||
|
||||
Configuring Tamper Protection in Intune can be targeted to your entire organization as well as to devices and user groups with Intune.
|
||||
Configuring tamper protection in Intune can be targeted to your entire organization as well as to devices and user groups with Intune.
|
||||
|
||||
### Can I configure Tamper Protection in System Center Configuration Manager?
|
||||
### Can I configure tamper protection in System Center Configuration Manager?
|
||||
|
||||
Currently we do not have support to manage Tamper Protection through System Center Configuration Manager.
|
||||
Currently we do not have support to manage tamper protection through System Center Configuration Manager.
|
||||
|
||||
### I have the Windows E3 enrollment. Can I use configuring Tamper Protection in Intune?
|
||||
### I have the Windows E3 enrollment. Can I use configuring tamper protection in Intune?
|
||||
|
||||
Currently, configuring Tamper Protection in Intune is only available for customers who have [Microsoft Defender Advanced Threat Protection E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp).
|
||||
Currently, configuring tamper protection in Intune is only available for customers who have [Microsoft Defender Advanced Threat Protection E5](https://www.microsoft.com/microsoft-365/windows/microsoft-defender-atp).
|
||||
|
||||
### What happens if I try to change Microsoft Defender ATP settings in Intune, System Center Configuration Manager, and Windows Management Instrumentation when Tamper Protection is enabled on a device?
|
||||
### What happens if I try to change Microsoft Defender ATP settings in Intune, System Center Configuration Manager, and Windows Management Instrumentation when tamper protection is enabled on a device?
|
||||
|
||||
You won’t be able to change the features that are protected by Tamper Protection; those change requests are ignored.
|
||||
You won’t be able to change the features that are protected by tamper protection; those change requests are ignored.
|
||||
|
||||
### I’m an enterprise customer. Can local admins change Tamper Protection on their devices?
|
||||
### I’m an enterprise customer. Can local admins change tamper protection on their devices?
|
||||
|
||||
No. Local admins cannot change or modify Tamper Protection settings.
|
||||
No. Local admins cannot change or modify tamper protection settings.
|
||||
|
||||
### What happens if my device is onboarded with Microsoft Defender ATP and then goes into an off-boarded state?
|
||||
|
||||
In this case, Tamper Protection status changes, and this feature is no longer applied.
|
||||
In this case, tamper protection status changes, and this feature is no longer applied.
|
||||
|
||||
### Will there be an alert about Tamper Protection status changing in the Microsoft Defender Security Center?
|
||||
### Will there be an alert about tamper protection status changing in the Microsoft Defender Security Center?
|
||||
|
||||
Yes. The alert is shown in [https://securitycenter.microsoft.com](https://securitycenter.microsoft.com) under **Alerts**.
|
||||
|
||||
@ -169,7 +199,7 @@ In addition, your security operations team can use hunting queries, such as the
|
||||
|
||||
`AlertEvents | where Title == "Tamper Protection bypass"`
|
||||
|
||||
### Will there be a group policy setting for Tamper Protection?
|
||||
### Will there be a group policy setting for tamper protection?
|
||||
|
||||
No.
|
||||
|
||||
|
||||
Reference in New Issue
Block a user